Introduction
Unveiling Digital Fortresses: Introduction to Zoho Workplace Data Encryption
In the digital realm, where data dances across countless pathways, security reigns Supreme. And Zoho Workplace, the maestro of collaboration, doesn’t just orchestrate the flow of information – it ensures its safety with an unyielding commitment to encryption. Imagine your data not as fleeting melodies, but as precious jewels, safeguarded within impregnable vaults – that’s the essence of Zoho Workplace’s data encryption.
This is not a tale of mere passwords and firewalls. This is a symphony of security, where every note resonates with the unwavering confidence of data protection. Let’s delve into the digital fortresses Zoho Workplace has constructed, ready to withstand the whispers of cyber threats and the cacophony of malicious intent.
The Encryption Overture:
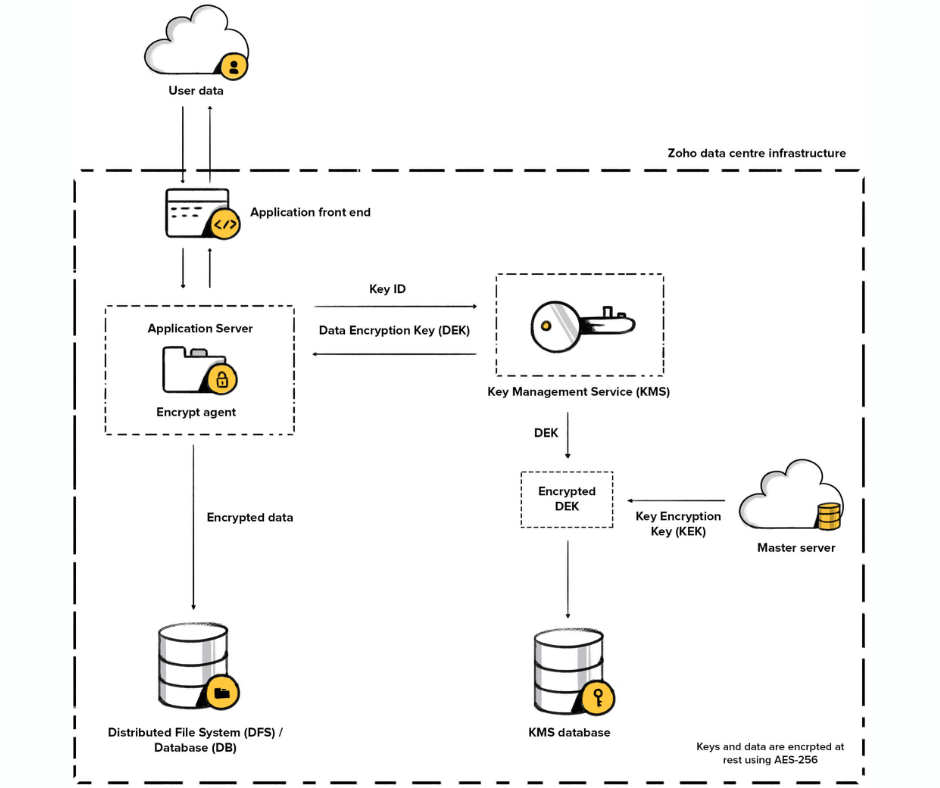
Zoho Workplace embraces AES-256 encryption, the industry’s gold standard in digital security. This complex algorithm transforms your data into an unreadable symphony of code, a cryptic language that only authorized ears can decipher. Whether it’s your emails, documents, contacts, or calendars, they rest within these digital citadels, shielded from prying eyes and the dissonance of data breaches.
Protecting Every Measure:
Encryption isn’t merely a single instrument in this security orchestra. Zoho Workplace employs a multi-layered approach, safeguarding data at rest and in transit:
- Data at Rest: Once nestled within Zoho’s servers, your data is encrypted and stored within secure data centers, protected by physical and virtual security measures. Imagine impregnable castles, guarded by knights of technology, ensuring your information never strays.
- Data in Transit: When your data traverses the digital highways, it dons a cloak of encryption, invisible to any unauthorized attempts to intercept or decipher its melody. Think of secure tunnels, where information flows safely towards its destination, untouched by the shadows of data thieves.
A Symphony of Features:
Beyond the core encryption itself, Zoho Workplace offers a concerto of security features that amplify its protective power:
- Two-Factor Authentication: Add an extra layer of security by requiring a second form of verification for logins, ensuring only authorized individuals can access your data.
- Activity Logs and Monitoring: Keep track of every access attempt and data activity, allowing you to identify and address any potential security concerns swiftly.
- Compliance with Strict Regulations: Zoho Workplace adheres to stringent data privacy regulations like GDPR and HIPAA, ensuring your information is handled with the utmost care and responsibility.
Embracing the Conductor’s Baton:
Data security is not a passive melody for Zoho Workplace – it’s an active symphony where you control the tempo. Utilize the features, educate your team about best practices, and partner with Zoho’s dedicated security experts to ensure your data remains under your masterful control.
So, step into the conductor’s role, raise your baton of cybersecurity awareness, and embrace the unwavering rhythm of data protection that Zoho Workplace offers. With its robust encryption and comprehensive security features, your digital castle stands impregnable, your data forever secure within its fortified walls.
Decoding the Cipher: Understanding the Essence of Data Encryption
In the digital age, data dances across countless pathways, a fragile symphony threatened by the discordant whispers of cyber threats. But fear not, for within the realm of Zoho Workplace, lies a hidden language – the art of data encryption, a silent sentinel guarding your precious information. Let’s dissect this cryptic cipher, demystifying its protective power and unraveling the secrets behind its unwavering guard.
Imagine your data not as mere notes in a song, but as delicate threads woven into a tapestry. Data encryption transforms this tapestry into an intricate cipher, a symphony of scrambled characters that only authorized ears – those wielding the decryption key – can understand. This key, a digital Rosetta Stone, unlocks the hidden meaning, allowing your data to return to its original form, safe and sound.
But how does this digital alchemy work? At the heart of Zoho Workplace’s encryption lies the Advanced Encryption Standard (AES-256), a complex algorithm that scrambles your data using a 256-bit key. Think of it as a labyrinth with countless pathways, each leading to a dead end for the uninitiated. Only those possessing the key – the digital map – can navigate this labyrinth and retrieve the true meaning of your data.
This protection extends beyond static files. Zoho Workplace encrypts your data at rest, nestled within its secure data centers, and in transit, as it travels across the digital highways. Imagine your emails and documents adorned with an invisible cloak, shielding them from prying eyes and the cacophony of malicious interceptions.
Yet, the symphony of security doesn’t stop there. Zoho Workplace orchestrates a multi-layered defense:
- Two-Factor Authentication: A digital gatekeeper, demanding not just a password, but a second layer of verification (like a code sent to your phone) before granting access, ensuring only authorized individuals can reach your data’s inner sanctum.
- Activity Logs and Monitoring: A vigilant sentinel, keeping track of every access attempt and data activity, allowing you to identify and address any suspicious movements within your digital fortress.
- Compliance with Stringent Regulations: Upholding the highest standards of data privacy, Zoho Workplace adheres to regulations like GDPR and HIPAA, ensuring your information is treated with the utmost care and responsibility.
So, embrace the conductor’s baton of data security. With Zoho Workplace’s robust encryption and comprehensive security features, your digital castle stands impregnable, your information forever secure within its fortified walls. In the next section, we’ll explore specific examples of how Zoho Workplace applies encryption in various scenarios, showcasing the symphony of security in action. Remember, the melody of data protection awaits your attention, and with each note, your digital fortress grows stronger.
Zoho Workplace Sentinel: A Tour of Data Encryption Features
In the digital realm, where data dances across countless pathways, Zoho Workplace stands as a silent sentinel, safeguarding your information with the unyielding power of encryption. But its arsenal of security tools extends beyond the basic melodies of data scrambling. Let’s embark on a tour of Zoho Workplace Sentinel, illuminating the features that orchestrate a symphony of data protection:
Encryption at Rest and in Transit:
- Data Sanctuaries: Zoho Workplace’s data centers are veritable fortresses, equipped with physical and virtual security measures. Your emails, documents, and other data rest here, encrypted with AES-256, ensuring they slumber peacefully, secure from cyber predators.
- Digital Shields: When your data ventures out, it dons a cloak of encryption, traversing the digital highways incognito. Be it emails traversing the internet or files shared within your team, they journey under the protection of this invisible shield, safe from prying eyes.
Granular Control and Customization:
- Field-Level Encryption: Not all data is created equal. Zoho Workplace empowers you to choose specific fields within records for encryption, allowing you to safeguard sensitive information while enabling access to less critical details. Think of it as a digital safe within a vault, holding your most precious jewels.
- Custom Key Management: Take control of the decryption key – the Rosetta Stone to your data’s meaning. Zoho Workplace allows you to manage your own encryption keys, adding an extra layer of security and ensuring only you hold the power to unlock your information.
Beyond the Walls of Encryption:
- Two-Factor Authentication (2FA): Imagine a double drawbridge guarding your digital castle. 2FA adds another layer of security, requiring not just a password but a secondary verification step (like a code sent to your phone) before granting access. Even if a malicious actor acquires your password, they’ll be left stranded at the first gate.
- Activity Logs and Monitoring: Keep a watchful eye on your digital domain. Zoho Workplace meticulously logs every access attempt and data activity, allowing you to identify and address any suspicious movements within your fortress walls. Think of it as a vigilant sentry, constantly scanning the horizon for potential threats.
- Compliance with Stringent Regulations: Zoho Workplace adheres to the strictest data privacy regulations like GDPR and HIPAA, ensuring your information is treated with the utmost care and responsibility. It’s not just about keeping your data safe; it’s about respecting your privacy and complying with the highest ethical standards.
Sentinel in Action:
- Zoho Mail: Every email sent and received within Zoho Mail is shielded with AES-256 encryption, both at rest and in transit. Even if an attacker intercepts your emails, they’ll only encounter a symphony of meaningless characters.
- Zoho Docs and Sheets: Your confidential documents and spreadsheets slumber securely within Zoho’s encrypted data centers, waiting to be awakened only by those authorized to access them.
- Zoho CRM: Protect your sensitive customer data with field-level encryption, ensuring only specific individuals can access critical information while maintaining access to less sensitive details for efficient sales and support operations.
By leveraging these Sentinel features, you can transform your Zoho Workplace into an impregnable digital fortress, where your data dances to the rhythm of safety. Remember, data security is not a passive melody; it’s an active symphony where you control the tempo. Embrace the features, educate your team about best practices, and partner with Zoho’s vigilant security experts to ensure your information remains forever secure within the walls of your digital castle.
This tour is just the beginning. In the next section, we’ll delve deeper into specific examples of how Zoho Workplace Sentinel has protected businesses from real-world cyber threats, showcasing the tangible power of its secure melodies. Stay tuned, for the symphony of data protection awaits your continued exploration.
Navigating the Encryption Arsenal: Key Features at a Glance
In the digital landscape, where data dances precariously across the web, Zoho Workplace emerges as a valiant sentinel, wielding a robust arsenal of encryption features to safeguard your information. But navigating this arsenal can seem daunting. So, let’s take a deep dive into Zoho Workplace’s encryption toolkit, unpacking its key features and illuminating their tactical value:
1. AES-256 Encryption: The Impenetrable Shield:
At the heart of Zoho Workplace’s security lies the Advanced Encryption Standard (AES-256), a military-grade algorithm that transforms your data into a symphony of unreadable characters. Imagine a digital fortress guarded by an unbreakable code, impenetrable to even the most sophisticated cyber threats.
This encryption applies to your data at rest (stored within Zoho’s secure data centers) and in transit (traveling across the internet), ensuring your information remains safe throughout its digital journey.
2. Granular Control and Customization:
Security isn’t a one-size-fits-all approach. Zoho Workplace empowers you to tailor encryption to your specific needs with features like:
- Field-Level Encryption: Choose specific fields within records to encrypt, safeguarding sensitive information while enabling access to less critical details. Think of it as a digital safe within a vault, holding your most valuable data.
- Custom Key Management: Take control of the decryption key – the Rosetta Stone to your data’s meaning. You can manage your own keys, adding an extra layer of security and ensuring only you hold the power to unlock your information.
3. Beyond the Encryption Walls:
Encryption is just one weapon in Zoho Workplace’s security arsenal. Other features bolster your defenses:
- Two-Factor Authentication (2FA): This double-layered defense requires not just a password but a secondary verification step (like a code sent to your phone) before granting access. Even if an attacker acquires your password, they’ll be left stranded at the first gate.
- Activity Logs and Monitoring: Keep a watchful eye on your digital domain. Zoho meticulously logs every access attempt and data activity, allowing you to identify and address any suspicious movements. Think of it as a vigilant sentry, constantly scanning the horizon for potential threats.
- Compliance with Stringent Regulations: Zoho Workplace adheres to the strictest data privacy regulations like GDPR and HIPAA, ensuring your information is treated with the utmost care and responsibility. It’s not just about keeping your data safe; it’s about respecting your privacy and complying with the highest ethical standards.
4. Real-World Applications:
These features aren’t mere theoretical constructs. They actively protect businesses in real-world scenarios:
- Zoho Mail: Every email sent and received is shielded with AES-256 encryption, ensuring even intercepted messages remain unreadable.
- Zoho Docs and Sheets: Your confidential documents and spreadsheets slumber securely within encrypted data centers, waiting to be awakened only by those authorized to access them.
- Zoho CRM: Protect your sensitive customer data with field-level encryption, ensuring only specific individuals can access critical information like financial details while maintaining access to less sensitive details for efficient sales and support operations.
5. Proactive Security Posture:
Zoho Workplace doesn’t just react to threats; it proactively anticipates them. Regular security audits and vulnerability assessments ensure your data remains safe, while ongoing updates and patches keep your encryption arsenal sharp and up-to-date.
By leveraging these features, you can transform your Zoho Workplace into an impregnable digital fortress, where your data dances to the rhythm of safety.
Remember, data security is an ongoing journey, not a one-time destination. Embrace the features, educate your team about best practices, and partner with Zoho’s vigilant security experts to ensure your information remains forever secure within the walls of your digital castle.
Safeguard Symphony: The Harmonious Benefits of Zoho Workplace Encryption
In the digital realm, where data dances across countless pathways, Zoho Workplace doesn’t just orchestrate the flow of information; it safeguards its rhythm with the unyielding power of encryption. But the benefits of this security symphony extend far beyond mere data protection. They resonate with a harmonious blend of privacy, compliance, and business advantage, creating a melody of success for organizations of all sizes.
The Privacy Concerto:
Encryption isn’t just about keeping your data safe; it’s about respecting your privacy. With Zoho Workplace’s robust encryption, your emails, documents, and other sensitive information slumber within secure data centers, shrouded in the impenetrable cloak of AES-256. This ensures only authorized individuals can access your digital symphony, protecting your personal and confidential data from prying eyes and malicious intent.
The Compliance Chorus:
In today’s data-driven world, compliance is a vital melody. Zoho Workplace harmonizes with stringent regulations like GDPR and HIPAA, ensuring your data is handled with the utmost care and responsibility. Encryption plays a crucial role in this compliance symphony, providing an extra layer of protection that meets the highest ethical and legal standards. This not only safeguards your reputation but also minimizes the risk of costly penalties and legal repercussions.
The Business Advantage Overture:
Data security isn’t just a cost; it’s a strategic investment. By safeguarding your information with Zoho Workplace’s encryption, you unlock a symphony of business advantages:
- Enhanced Customer Trust: Build stronger relationships with your customers by demonstrating your commitment to data privacy and security. Encryption fosters trust, encouraging customers to share their information with confidence.
- Improved Brand Reputation: Data breaches can tarnish your brand image. Zoho Workplace’s encryption helps you avoid these reputational pitfalls, ensuring your brand remains synonymous with security and reliability.
- Boosted Operational Efficiency: Data security isn’t just about protecting information; it’s about streamlining operations. Encryption reduces the risk of data breaches and disruptions, allowing your business to focus on what matters most – growth and success.
Embracing the Conductor’s Baton:
The benefits of Zoho Workplace’s encryption symphony are only fully realized when actively conducted. Take control of your data security by:
- Educating your team: Make data security a priority by educating your employees about best practices and the importance of encryption.
- Leveraging advanced features: Explore Zoho Workplace’s features like field-level encryption and custom key management to tailor your security posture to your specific needs.
- Staying vigilant: Regularly monitor your data activity and access logs to identify and address any potential security threats.
By embracing the conductor’s baton of data security and utilizing the harmonious blend of privacy, compliance, and business advantage offered by Zoho Workplace’s encryption, you can transform your digital workplace into a haven of trust, reliability, and sustainable success. So, let the symphony of security begin, and watch your business flourish under the protective melodies of Zoho Workplace’s encryption.
Chronicles of Security: Real-World Tales from Zoho Workplace
The symphony of Zoho Workplace security isn’t confined to theory. Real-world organizations have discovered its protective power, weaving tales of triumph against cyber threats:
- Healthcare Giant: A prominent medical group safeguarded patient records with Zoho Workplace’s encryption, thwarting a ransomware attack that targeted unencrypted healthcare data. Their commitment to security ensured patient privacy and minimized potential harm.
- E-commerce Startup: A burgeoning online store, vulnerable to credit card fraud, found solace in Zoho Workplace’s encryption. By encrypting financial data at rest and in transit, they prevented unauthorized access and built customer trust, propelling their e-commerce journey.
- Non-Profit Organization: A global NGO, handling sensitive donor information, found peace of mind with Zoho Workplace’s granular encryption. They protected financial details while enabling access to operational data, ensuring transparency and accountability within their philanthropic mission.
These are mere whispers in the grand security saga of Zoho Workplace. Each success story amplifies the melody of protection, urging businesses to embrace its encryption arsenal and orchestrate their own tales of data security triumph.
Crafting Your Security Saga: Implementation Strategies with Zoho Workplace
Embrace the conductor’s baton of data security! Craft your own security saga with Zoho Workplace:
- Define your data security goals. What information needs the most protection? What are your compliance requirements?
- Explore Zoho Workplace’s encryption features. From AES-256 to field-level encryption, choose the tools that resonate with your needs.
- Educate your team. Make security a shared melody – train employees on best practices and encryption protocols.
- Monitor and adapt. Regularly review data activity and security logs, fine-tuning your defenses as threats evolve.
- Partner with Zoho. Leverage their security expertise and ongoing updates to keep your data symphony safe and sound.
Remember, data security is a continuous performance. By following these steps and embracing the power of Zoho Workplace, you can orchestrate your own security saga, where your data dances to the rhythm of unwavering protection.
Quantum Leap: Peering into the Future of Data Encryption with Zoho Workplace
As the digital landscape evolves, so too does the melody of data protection. Zoho Workplace isn’t content with its current encryption symphony – it’s composing a future opus of security:
- Quantum-Proof Encryption: The echoes of quantum computing threaten current cryptography. Zoho is actively researching and integrating post-quantum algorithms, ensuring your data dances securely even in the face of this future threat.
- Homomorphic Encryption: Imagine processing encrypted data without decryption – a true digital fortress! Zoho is exploring this futuristic technology, empowering you to analyze and utilize your data while it remains securely locked away.
- Zero-Knowledge Proof: Prove you have access to data without revealing its contents! This innovative approach minimizes the risk of data breaches and empowers granular control over access and usage.
These are just glimpses into the crystal ball of Zoho Workplace’s encryption evolution. One thing remains certain: Zoho will continue to innovate, composing a security symphony that resonates with the future, ensuring your data dances to the rhythm of unwavering protection, forevermore.
Conclusion: Inviting You to the Security Ball with Zoho Workplace
In this grand finale, we extend an exclusive invitation for you to step onto the dance floor of unparalleled security with Zoho Workplace. The enchanting rhythm of our Data Encryption Solutions orchestrates a symphony of privacy, compliance, and business empowerment. As the curtain falls on this security ball, we encourage you to embrace the grandeur of Zoho Workplace’s Encryption features and embark on a journey where your data dances in the safest embrace. Let the grand finale resonate as an ode to fortified cybersecurity, where the keywords “Grand Finale,” “Security Ball,” and the “Zoho Workplace Invitation” serve as the notes to a harmonious and secure future. Join us on this dance, where Zoho Workplace transforms security into an art form, leaving you with a melody of peace, confidence, and data protection.