Introduction to AWS Identity and Access Management (IAM)
Amazon Web Services (AWS) Identity and Access Management (IAM) serves as the linchpin of cloud security, providing a robust framework for managing user identities and access permissions within the AWS ecosystem. As organizations migrate to the cloud, the significance of IAM becomes paramount, addressing the challenges of secure access, authorization, and centralized governance.
Overview of IAM
IAM, at its core, is a comprehensive web service that allows users to control and secure access to AWS resources. It plays a pivotal role in safeguarding sensitive data and critical infrastructure components hosted on the AWS cloud. The fundamental principle is to authenticate users, devices, and applications while enforcing granular access policies tailored to specific roles and responsibilities.
IAM acts as the gatekeeper, ensuring that only authenticated and authorized entities can interact with AWS resources. By defining and managing identities, organizations can establish a robust security perimeter that aligns with their specific requirements.
Key Concepts
To comprehend the essence of IAM, one must grasp its key components:
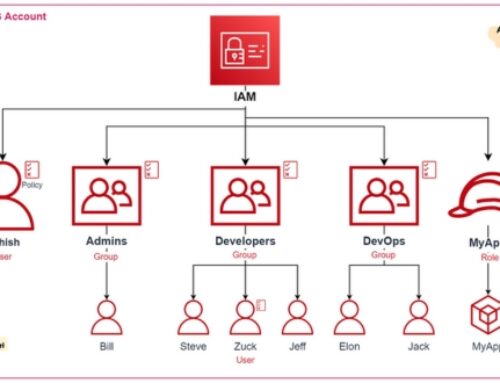
- IAM Users: These are entities with unique credentials used to interact with AWS. Users can be assigned individual security credentials and placed into groups.
- IAM Groups: Groups are collections of IAM users. Instead of assigning permissions directly to users, organizations can assign permissions to groups, streamlining access management.
- IAM Roles: Roles are AWS Identity and Access Management entities with policies that determine what permissions are granted to users or other roles. Roles are often used in scenarios that require cross-account access.
- IAM Policies: Policies are the building blocks of IAM, defining permissions and determining what actions are allowed or denied. They are attached to users, groups, or roles.
Benefits of IAM
The adoption of IAM brings forth a myriad of advantages for organizations navigating the complexities of cloud security:
- Enhanced Security: IAM establishes a secure foundation, ensuring that only authenticated and authorized entities can access AWS resources.
- Fine-Grained Access Control: With IAM policies, organizations can define precise permissions, adhering to the principle of least privilege and mitigating security risks.
- Centralized Management: IAM provides a centralized console for managing identities and access, simplifying the administration of user credentials, permissions, and policies.
In essence, IAM is the cornerstone of secure, well-managed AWS environments, offering organizations the tools needed to fortify their cloud infrastructure.
IAM Users and Groups
In this section, we will explore the intricacies of creating, managing IAM users, leveraging groups, and implementing policies for fine-grained access control.
Creating and Managing Users
IAM users are the foundation of access control in AWS, representing entities with unique credentials and permissions. Creating and managing IAM users involves a step-by-step process to ensure secure and efficient access management.
- User Creation:
- Navigate to the IAM console and select “Users.”
- Choose “Add user” to initiate the user creation wizard.
- Specify the username and access type (programmatic, AWS Management Console, or both).
- Set permissions by attaching policies directly or placing the user into IAM groups.
- Permissions and Policies:
- Define permissions by attaching IAM policies that specify what actions a user can perform on which resources.
- IAM policies are JSON documents outlining the permissions, and they can be fine-tuned to grant access to specific services, actions, and resources.
- Password Management:
- Implement robust password policies to enhance security.
- Leverage multi-factor authentication (MFA) for an additional layer of protection.
- Lifecycle Management:
- Regularly review and update user permissions based on evolving roles and responsibilities.
- Deactivate or delete unused users to maintain a clean and secure IAM environment.
Working with Groups
IAM groups provide a mechanism for simplifying access management by aggregating users with similar roles or responsibilities. Efficient group management is crucial for maintaining an organized and secure access structure.
- Creating IAM Groups:
- Access the IAM console and navigate to the “Groups” section.
- Choose “Create group” and define the group name.
- Attach policies to the group to grant specific permissions to all members.
- Advantages of Group Usage:
- Simplified Access Control: Changes in permissions can be applied to entire groups, streamlining access management.
- Scalability: As the organization grows, groups facilitate the seamless addition of new users with predefined access.
- Best Practices for Group Management:
- Role-Based Groups: Create groups based on roles or functions within the organization.
- Regular Audits: Conduct periodic audits to ensure groups align with current business requirements.
- Avoid Overlapping Permissions: Prevent redundant permissions by carefully structuring group memberships.
IAM Policies
IAM policies are the linchpin of access control, defining what actions users and groups are allowed or denied. Crafting effective policies requires a deep understanding of the organization’s security requirements.
- Policy Anatomy:
- Policies are JSON documents with statements specifying permissions.
- Each statement includes an “Effect” (allow or deny), “Action” (specific AWS actions), and “Resource” (AWS resources affected).
- Granular Control with Policies:
- IAM policies enable fine-grained control over AWS resources.
- Policies can be attached to users, groups, or roles, providing flexibility in access management.
- Conditional Policies:
- Implement conditions within policies to add contextual restrictions.
- Conditions may include IP address ranges, time frames, or the presence of MFA.
- Regular Review and Revision:
- Periodically review and revise policies to align with changing business needs.
- Utilize AWS Policy Simulator for testing the impact of policy changes before implementation.
In essence, IAM users and groups, coupled with meticulously crafted policies, form the backbone of AWS access management.
IAM Roles and Permissions
In this section, we will explore the dynamic realm of IAM roles, understanding their role-based access control (RBAC) concepts, how permissions are assigned, and the intricacies of cross-account access.
Understanding IAM Roles
IAM roles introduce a versatile approach to access control, allowing entities in AWS to assume roles with specific permissions. Role-based access control (RBAC) is a fundamental concept, emphasizing the principle of least privilege and enhancing security posture.
- Role Basics:
- IAM roles represent a set of permissions that define what actions are allowed or denied within AWS resources.
- Roles are not associated with a specific user or group but are assumed by entities like IAM users, AWS services, or even external identities.
- Use Cases for IAM Roles:
- Temporary Permissions: IAM roles are often used to grant temporary permissions. Entities assume roles for a defined period, reducing the risk of long-standing elevated privileges.
- Cross-Account Access: Roles facilitate secure access between AWS accounts, enabling collaboration without sharing long-term credentials.
- Federation: External identities, such as those from Active Directory or identity providers, can assume IAM roles for seamless integration.
- Role Assumption:
- Entities assume roles using temporary security credentials obtained through AWS Security Token Service (STS).
- Trust policies define the entities that can assume a role, implementing a secure trust relationship.
Assigning Permissions
The assignment of permissions to IAM roles is a pivotal aspect of IAM configuration, requiring a comprehensive understanding of policy creation, evaluation logic, and best practices for effective access management.
- Granting Permissions:
- Permissions are granted to IAM roles through the attachment of policies.
- Policies dictate the actions that can be performed and the resources on which these actions can be executed.
- Policy Evaluation Logic:
- IAM uses a deny-by-default policy evaluation logic. If no explicit permission is granted, the action is denied.
- Policies can be attached directly to roles or inherited through group memberships.
- Dynamic Policies with Variables:
- Leverage policy variables, such as ${aws:username} or ${aws:userid}, to create dynamic and context-aware policies.
- Dynamic policies enhance flexibility in access management.
Cross-Account Access
IAM roles extend their functionality beyond a single AWS account, allowing secure cross-account access. Configuring cross-account roles requires meticulous setup and adherence to best practices for secure delegation.
- Configuring IAM Roles for Cross-Account Access:
- Define a trust relationship in the form of a trust policy, specifying the trusted entities (accounts or users).
- Grant permissions in the trusted account by attaching policies to the role.
- Secure Delegation Best Practices:
- Least Privilege: Assign the minimum necessary permissions for the intended tasks to minimize the potential impact of compromised roles.
- Regular Auditing: Conduct audits to review and refine cross-account role configurations.
- Policy Conditions: Implement conditions in trust policies to add an additional layer of security.
IAM roles, with their flexible and granular access control capabilities, play a pivotal role in securing AWS environments.
Multi-Factor Authentication (MFA)
In this section, we will explore the crucial realm of Multi-Factor Authentication (MFA), understanding its significance in bolstering account security, the steps involved in setting it up, and best practices for its effective implementation.
Introduction to MFA
- Significance of MFA:
- MFA adds an extra layer of security by requiring users to provide multiple forms of verification before gaining access to their accounts.
- By combining something the user knows (password) with something they possess (MFA device), the risk of unauthorized access is significantly reduced.
- Enhancing Account Security:
- MFA mitigates the vulnerabilities associated with single-factor authentication, such as password compromises.
- Protects against unauthorized access, especially critical for accounts with elevated privileges.
Setting Up MFA
- Configuring MFA Devices:
- Walkthrough on how to set up MFA devices, including options like virtual MFA devices or hardware tokens.
- Step-by-step guidance on associating MFA with IAM users for an added layer of security.
- Enabling MFA for IAM Users:
- IAM users can be configured to use MFA, ensuring an additional authentication step during login.
- Methods for enabling MFA, including the AWS Management Console and AWS CLI.
Best Practices
- Strategies for Enforcing MFA:
- Mandatory MFA for High-Privilege Actions: Implement policies that mandate MFA for IAM users performing sensitive operations.
- Conditional MFA: Utilize AWS Identity and Access Management (IAM) policies to require MFA under specific conditions or IP ranges.
- Managing MFA Devices Securely:
- Device Management Policies: Establish policies for managing MFA devices, including procedures for replacement or deactivation.
- Monitoring and Reporting: Regularly monitor MFA device usage and have mechanisms for reporting suspicious activity.
- Backup and Recovery Procedures:
- Lost or Stolen Devices: Provide clear guidelines on what actions users should take if their MFA device is lost or stolen.
- Account Recovery: Establish secure account recovery procedures to avoid lockouts in case of MFA device issues.
Multi-Factor Authentication is a cornerstone in the defense against unauthorized access, and understanding its implementation and best practices is paramount for a robust security posture.
IAM Security Best Practices
In this section, we delve into the core security best practices for AWS Identity and Access Management (IAM), emphasizing the principles and measures essential for maintaining a secure access environment.
Least Privilege Principle
- Definition and Importance:
- Least Privilege Defined: Adhering to the principle of least privilege involves granting users the minimum access needed to perform their tasks.
- Reducing Attack Surface: By limiting permissions, the potential impact of compromised accounts or accidental misconfigurations is significantly reduced.
- Implementation Strategies:
- Granular Permissions: Assign permissions at a granular level, ensuring users have only the necessary access for their specific roles.
- Role-Based Access Control (RBAC): Leverage IAM roles to allocate permissions based on job functions, facilitating a more structured and secure access model.
Regular Audits
- Purpose and Significance:
- Ongoing Evaluation: Regularly reviewing IAM policies and permissions ensures alignment with business requirements and security standards.
- Detecting Anomalies: Audits are crucial for identifying and rectifying any inconsistencies or unauthorized access that may have arisen over time.
- Conducting Audits:
- Periodic Reviews: Establish a routine schedule for auditing IAM configurations, considering factors like organizational changes or system updates.
- Automated Auditing Tools: Explore AWS tools and third-party solutions for automating policy checks and audits, enhancing efficiency.
Strong Password Policies
- Strengthening Passwords:
- Complexity Requirements: Enforce strong password policies, including a mix of uppercase and lowercase letters, numbers, and special characters.
- Regular Rotation: Implement regular password rotation practices to reduce the risk associated with prolonged use of the same credentials.
- Multi-Factor Authentication (MFA):
- Enhancing Password Security: Combine strong password policies with MFA to add an additional layer of security.
- Mandatory MFA: Consider making MFA mandatory for accounts with elevated privileges or accessing sensitive data.
Incorporating these IAM security best practices establishes a robust foundation for safeguarding AWS environments.
IAM Integration with AWS Services
In this section, we explore the seamless integration of AWS Identity and Access Management (IAM) with various AWS services, focusing on the utilization of IAM roles and policies for secure and controlled access.
AWS Service Roles
- IAM Roles Overview:
- Dynamic Permissions: AWS service roles enable dynamic assignment of permissions to AWS services, enhancing flexibility in managing access.
- Scoped Access: These roles are tailored for specific AWS services, ensuring precise control over the resources they can interact with.
- Use Cases and Benefits:
- Lambda Function Execution: IAM roles are commonly used for granting AWS Lambda functions the necessary permissions to interact with other AWS resources.
- Managed Policies: Service roles often come with managed policies, simplifying the permission assignment process for common use cases.
Integration with S3 and EC2
- IAM Policies for S3 Access:
- Granular Bucket Permissions: Craft IAM policies to define access controls at the S3 bucket level, specifying who can perform actions like reading, writing, or deleting objects.
- Cross-Account Access: IAM can facilitate secure cross-account access to S3 resources, allowing fine-grained control over data sharing.
- IAM Policies for EC2 Instances:
- Instance Profiles: IAM roles can be associated with EC2 instances using instance profiles, providing temporary credentials to applications running on the instances.
- Least Privilege for Instances: Implement IAM policies that grant EC2 instances the minimum required permissions, following the principle of least privilege.
Best Practices for Secure Access
- Principle of Least Privilege:
- IAM Roles Refinement: Apply the principle of least privilege when defining roles, ensuring that AWS services only have access to the resources essential for their tasks.
- Regular Audits: Periodically review and refine service roles and associated policies to align with current business requirements.
- Monitoring and Logging:
- CloudTrail Integration: Integrate IAM with AWS CloudTrail to capture detailed logs of actions performed by AWS services, aiding in security audits and incident response.
- Alerting Mechanisms: Implement alerting mechanisms based on CloudWatch Events to promptly detect and respond to any suspicious activities involving IAM roles.
Understanding the intricacies of IAM integration with AWS services is pivotal for creating a secure and well-coordinated access control framework.
IAM Access Analyzer and Policy Simulator
In this section, we delve into two powerful tools offered by AWS Identity and Access Management (IAM) – the Access Analyzer and the Policy Simulator. These tools play pivotal roles in enhancing the security posture of AWS environments by providing insights into resource access policies and facilitating proactive validation of IAM policy changes.
Access Analyzer
- Uncovering Unintended Access Permissions:
- Resource Policy Analysis: AWS Access Analyzer diligently examines resource policies, including S3 buckets, IAM roles, and KMS keys, to identify and highlight unintended access permissions.
- Granular Insights: The tool offers granular insights into who can access resources and how, ensuring a comprehensive understanding of potential security risks.
- Integration with AWS Organizations:
- Centralized Analysis: Access Analyzer seamlessly integrates with AWS Organizations, enabling centralized analysis of resource policies across an entire organization.
- Cross-Account Visibility: Gain visibility into potential cross-account access risks, facilitating proactive security measures.
- Remediation Recommendations:
- Actionable Insights: Access Analyzer doesn’t just identify issues; it goes further by providing actionable recommendations for remediation.
- Policy Adjustments: Users can adjust resource policies directly from the Access Analyzer console, streamlining the process of fixing identified vulnerabilities.
Policy Simulator
- Proactive Validation of Policy Changes:
- Policy Simulation Environment: The Policy Simulator creates a controlled environment for simulating IAM policy changes without affecting actual permissions.
- Risk-Free Testing: Users can test policy modifications in a risk-free environment to understand their impact before deploying changes in a production setting.
- Policy Simulation Use Cases:
- Impact Analysis: Evaluate the impact of policy changes on specific IAM entities or resources, helping prevent unintended consequences.
- Iterative Policy Refinement: Policy Simulator supports an iterative approach to policy refinement, allowing users to fine-tune access controls with confidence.
- Advanced Simulation Scenarios:
- Conditions and Variables: The simulator supports complex scenarios involving conditions and variables, offering a comprehensive testing ground for diverse IAM policy configurations.
- Effective Permissions: Understand the effective permissions granted by policies in different situations, aiding in crafting precise and secure access controls.
Strengthening IAM Security Posture
- Continuous Improvement:
- Iterative Refinement: Access Analyzer and Policy Simulator contribute to an iterative approach to IAM policy management, promoting continuous improvement.
- Security Best Practices: Leveraging these tools aligns with security best practices, ensuring that IAM configurations evolve with the dynamic nature of cloud environments.
As we navigate the intricacies of IAM Access Analyzer and Policy Simulator, it becomes evident that these tools are indispensable for organizations committed to maintaining robust security practices in their AWS deployments.
Conclusion: Enhancing Security with AWS IAM
In the dynamic landscape of cloud computing, security stands as a paramount concern, and AWS Identity and Access Management (IAM) emerges as a linchpin in fortifying digital fortresses. As we conclude our journey through the multifaceted realm of IAM, it becomes evident that mastering these capabilities is not merely a best practice; it is a strategic imperative for organizations navigating the intricate terrain of AWS services.
IAM: A Keystone of Cloud Security
- Foundational Security Pillar:
IAM, with its nuanced approach to user management, access policies, and authentication mechanisms, forms the foundational security pillar upon which resilient cloud architectures are built.
- Fine-Grained Access Control:
The robustness of IAM lies in its ability to provide fine-grained access control, adhering to the principle of least privilege and ensuring that users and entities have precisely the permissions they need – no more, no less.
Continuous Improvement and Adaptability
- Iterative Refinement:
IAM is not a static component; it thrives on iterative refinement. Organizations are encouraged to continually assess and adjust IAM configurations, leveraging tools like IAM Access Analyzer and Policy Simulator.
- Adapting to Evolving Threats:
In a landscape where threats evolve rapidly, IAM’s adaptability ensures that security postures can dynamically respond to emerging challenges. Access Analyzer aids in identifying and mitigating risks, while the Policy Simulator offers a safe playground for testing and refining policies.
Enhancing Collaboration and Productivity
- User-Friendly Collaboration:
IAM’s user and group management capabilities foster user-friendly collaboration within AWS environments. Teams can collaborate seamlessly while adhering to security best practices.
- Secure DevOps Integration:
IAM seamlessly integrates with DevOps processes, ensuring that security is not a roadblock but an enabler in the rapid deployment of applications and services.
Looking Beyond: Emerging Trends and Advanced IAM Strategies
- Continuous Learning:
As technology evolves, so does IAM. Organizations are encouraged to stay abreast of emerging trends, ensuring that IAM implementations align with the latest security standards and innovations.
- Advanced IAM Strategies:
The future holds promise for advanced IAM strategies, including integration with emerging technologies like artificial intelligence and machine learning. Continuous education and exploration will be key to harnessing these advancements.
In conclusion, AWS IAM is not merely a service; it is a strategic ally in the ongoing battle for cloud security. Embracing IAM’s capabilities, optimizing access controls, and staying vigilant against emerging threats position organizations to not only withstand challenges but to thrive in the ever-evolving landscape of cloud computing. As we bid farewell to this exploration, may your IAM mastery be a beacon of security and resilience in your AWS endeavors.
AWS IAM (Identity and Access Management) is a web service that helps securely control access to AWS resources. It allows organizations to manage users, groups, and permissions within their AWS environment.
IAM is crucial for securing AWS resources by enabling organizations to manage and control access to services. It follows the principle of least privilege, ensuring users have only the necessary permissions for their tasks.
Users are created in the IAM console. After logging in, navigate to the IAM dashboard, select “Users,” and click “Add user.” Specify user details, set permissions, and create the user.
The principle of least privilege means granting users the minimum level of access required to perform their tasks. This reduces the risk of unintended actions or exposure of sensitive data.
Yes, IAM users can belong to multiple groups, allowing for efficient management of permissions. Users inherit permissions from all groups to which they belong.