In the ever-evolving landscape of cloud computing, Google Cloud Platform (GCP) stands out as a powerhouse offering a myriad of services to cater to diverse business needs. Among the foundational components of GCP, the Virtual Private Cloud (VPC) plays a crucial role in providing a secure and isolated environment for your resources. In this comprehensive guide, we will delve deep into the intricacies of setting up a GCP Virtual Private Cloud, exploring its key concepts, features, and best practices.
Understanding GCP Virtual Private Cloud (VPC)
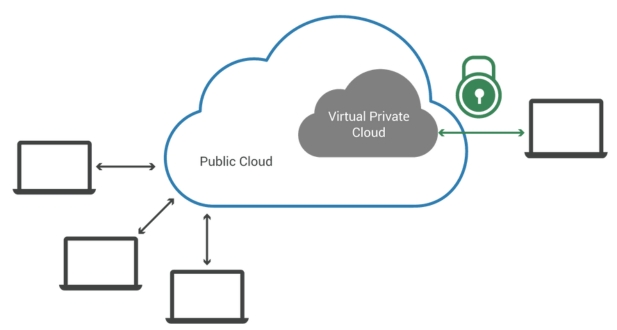
What is a Virtual Private Cloud?
A Virtual Private Cloud (VPC) is a fundamental component of cloud computing infrastructure, offering users a secure and isolated environment within a larger cloud platform such as Google Cloud Platform (GCP). The primary purpose of a VPC is to provide users with a dedicated and private space where they can deploy and manage their resources, ensuring a higher level of control and security over their data and applications.
Within a Virtual Private Cloud, users have the flexibility to design and customize their private network. This includes the ability to define IP addresses, create subnets, and configure routing tables according to their specific requirements. The customization options provided by VPCs allow users to tailor the network architecture to suit the needs of their applications and workloads, providing a high degree of flexibility and scalability.
One of the key advantages of a Virtual Private Cloud is the inherent isolation it offers. Resources deployed within a VPC are logically separated from the rest of the cloud infrastructure, creating a virtual barrier that restricts external access. This isolation ensures that the user’s data and applications remain secure and protected from unauthorized access, making VPCs an essential element for maintaining the confidentiality and integrity of sensitive information.
Furthermore, the secure communication between resources within the VPC is facilitated by the private network. This means that applications and services deployed in different parts of the VPC can interact with each other seamlessly while maintaining a level of isolation from external networks. This not only enhances security but also promotes efficient and reliable communication between components of a user’s cloud-based infrastructure.
A Virtual Private Cloud serves as a secure and customizable enclave within a cloud platform, empowering users with the tools to design and manage their private network. The isolation provided by VPC ensures the confidentiality of data and applications, making it a crucial component for businesses and organizations looking to leverage the benefits of cloud computing while maintaining a high level of control and security.
Core Components of GCP VPC
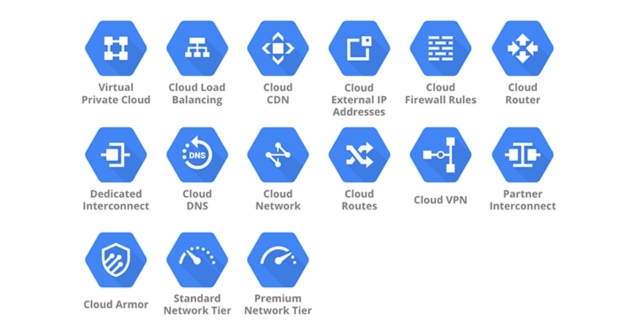
The core components of Google Cloud Platform’s (GCP) Virtual Private Cloud (VPC) are essential elements that collectively form the infrastructure for managing and organizing resources in the cloud environment.
Networks:
Networks serve as the fundamental building blocks in GCP VPC, establishing the connectivity framework for your resources. They provide a foundation for organizing workloads and can be created in multiple instances to segregate different types of activities, such as development, testing, and production. Networks are pivotal in ensuring that resources can communicate effectively within the cloud infrastructure.
Subnets:
Subnets represent subdivisions within a network, offering a way to segment resources based on various criteria such as availability zones or geographic locations. This segmentation is crucial for resource allocation and management. By using subnets, you can optimize the performance and reliability of your applications and services while maintaining control over the geographical distribution of your resources.
Firewalls:
GCP VPC incorporates a robust firewall mechanism that plays a pivotal role in controlling the flow of incoming and outgoing traffic to and from your resources. Through the definition of firewall rules, administrators can regulate and restrict network access, enhancing the overall security posture of the VPC. This feature ensures that only authorized traffic is permitted, mitigating potential security threats.
Routes:
Routing tables within GCP VPC define how network traffic is directed, determining the paths that data takes between different resources and subnets. Configuring routes is essential for optimizing communication within the VPC, ensuring efficient data transfer between various components of the cloud infrastructure.
Cloud Router:
Cloud Router facilitates dynamic routing within the VPC by enabling the automatic exchange of routes between the on-premises network and the GCP VPC. This dynamic routing capability enhances flexibility and responsiveness in managing network traffic, contributing to a more adaptable and scalable cloud environment.
Cloud VPN/Interconnect:
For establishing secure connections between on-premises networks and GCP VPC, Cloud VPN and Cloud Interconnect are vital components. Cloud VPN offers a secure virtual private network connection, while Cloud Interconnect provides a reliable, dedicated connection. Both options contribute to establishing robust, secure, and efficient communication channels between on-premises infrastructure and resources within the GCP VPC.
Setting Up Your GCP Virtual Private Cloud
Prerequisites
Before embarking on the setup process for your Google Cloud Platform (GCP) Virtual Private Cloud (VPC), ensure that you have certain prerequisites in place. Firstly, you need a valid GCP account to create and manage resources efficiently.
Step-by-Step Setup
- Accessing the GCP Console:
Start by logging into the GCP Console. If you do not possess an account, you can easily sign up for a free trial to get started with the setup process.
- Creating a New Project:
Within the GCP Console, navigate to the project selector and click on “New Project.” Here, provide a name for your project, select the appropriate billing account, and then click “Create” to proceed with the project creation.
- Enabling APIs:
Before setting up the Virtual Private Cloud, it’s crucial to enable the necessary APIs. Navigate to the “APIs & Services” section, click on “Dashboard,” and then click on “+ ENABLE APIS AND SERVICES.” Search for “Compute Engine API” and ensure it is enabled.
- Creating a VPC Network:
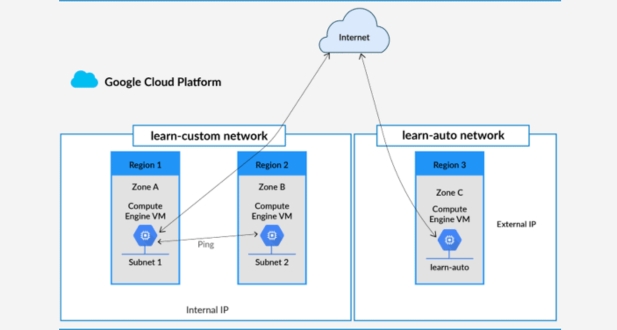
In the GCP Console, head to the “VPC” section and click on “VPC networks.” Click on “Create VPC Network” and provide a name for your network. Choose the routing mode (automatic or custom) and configure additional settings as needed. Click “Create” to establish your Virtual Private Cloud.
- Creating Subnets:
Within your VPC, the creation of subnets is necessary. Go to the “VPC networks” page, select your VPC, and click on “Subnets.” Click “Create Subnet” and fill in the required details, including the subnet name, IP range, and region. Repeat this step to generate additional subnets.
- Configuring Firewall Rules:
Navigate to the “Firewall” section in the GCP Console. Click on “Create Firewall Rule” and define the rule details, specifying the allowed protocols and ports. You have the flexibility to create rules for both ingress and egress traffic. Click “Create” to apply the firewall rule.
- Creating Virtual Machines (VMs):
Now that your VPC is set up, proceed to deploy virtual machines. Head to the “Compute Engine” section and click on “VM instances.” Click “Create Instance” to configure your VM, specifying details such as the machine type, boot disk, and network settings.
- Testing Connectivity:
Once your Virtual Machines are up and running, it is essential to test the connectivity between them. Ping one VM from another to ensure that the network configuration is correct, validating the successful establishment of your GCP Virtual Private Cloud.
Advanced GCP VPC Configurations
- Shared VPC:
Google Cloud Platform (GCP) offers the flexibility of creating shared Virtual Private Clouds (VPCs), a configuration where a host project shares its networks with other projects referred to as service projects. This functionality is particularly advantageous in scenarios where different teams or departments within an organization need to collaborate while still maintaining network isolation. Shared VPCs streamline the network administration process by allowing centralized control and resource sharing among multiple projects.
- VPC Peering:
VPC peering is a powerful feature that enables communication between Virtual Private Clouds without the necessity for a Virtual Private Network (VPN) or Interconnect. By establishing peering connections, GCP users can seamlessly extend their network and facilitate resource sharing across different projects or even organizations. This not only simplifies the network architecture but also enhances the efficiency of data transfer and collaboration, making it an essential tool for organizations with complex cloud infrastructures.
- Hybrid Connectivity:
GCP supports hybrid cloud architectures, providing a robust solution for connecting on-premises data centers to GCP VPCs. This connectivity can be established through either Cloud VPN or Cloud Interconnect, both of which offer secure and reliable connections. Hybrid connectivity is crucial for organizations with existing on-premises infrastructure looking to leverage the benefits of the cloud. It ensures a seamless and secure integration between on-premises and cloud environments, allowing for resource scalability and flexibility.
- Identity and Access Management (IAM):
In the context of Virtual Private Clouds, Identity and Access Management (IAM) plays a pivotal role in ensuring the security of the network. GCP’s IAM allows users to define granular permissions, controlling who can access and modify resources within the VPC. This approach adheres to the principle of least privilege, ensuring that users have only the necessary permissions to perform their tasks. By enforcing strict access controls through IAM, organizations can significantly enhance the overall security posture of their VPCs, mitigating the risk of unauthorized access and potential security breaches.
Key Concepts:
Subnets:
In the context of Google Cloud Platform (GCP), subnets play a crucial role in organizing and managing the IP addresses within a Virtual Private Cloud (VPC). Essentially, a subnet represents a subdivision of the IP range allocated to a VPC, and each subnet is associated with a specific region and availability zone. The careful delineation of subnets allows for efficient resource organization, as it enables the allocation of resources to specific subnets based on their functionalities or requirements. This subdivision is particularly advantageous for optimizing resource utilization and facilitating effective IP address management within the GCP infrastructure.
IP Addressing:
GCP provides the flexibility to define both internal (private) and external (public) IP addresses to cater to different networking needs. External IP addresses can be reserved and assigned to specific resources, such as load balancers, enabling external communication with these resources. On the other hand, internal IP addresses are used for communication within the VPC, ensuring secure and isolated network traffic. This duality in IP addressing allows users to tailor their network architecture to meet specific requirements, whether they involve external interactions or internal communication between resources within the GCP environment.
Firewall Rules:
Firewall rules serve as the gatekeepers of network traffic in a GCP VPC, controlling both incoming and outgoing data to and from resources. By default, GCP implements rules that deny all incoming traffic while allowing all outgoing traffic. This default configuration enhances the security of the VPC by enforcing a restrictive stance on incoming connections. However, users have the flexibility to define custom firewall rules to meet their specific security and networking needs. These custom rules can be tailored based on protocols, ports, and source or destination IP addresses, providing a granular level of control over the network traffic within the GCP infrastructure.
Routes:
In a GCP VPC, routing tables play a pivotal role in directing network traffic between different subnets. Default routes are automatically created to ensure basic connectivity within the VPC. Additionally, users can add custom routes to the routing tables to customize and optimize the flow of traffic based on specific requirements. This ability to tailor routing configurations allows for more fine-grained control over how data is directed within the GCP infrastructure, enabling users to design a network architecture that aligns with their application’s needs and overall performance objectives.
Best Practices for GCP VPC Setup
Creating a well-structured and secure Virtual Private Cloud (VPC) in Google Cloud Platform (GCP) is vital for the effective management and protection of cloud resources. This article outlines best practices for setting up a VPC in GCP, focusing on network design, security, performance, and cost-efficiency.
1. Start with a Strong Design
Understand Your Requirements: Before setting up a VPC, assess your organization’s needs. Consider aspects like the number of projects, expected traffic, types of services you will deploy, and compliance requirements.
Use Custom VPCs Over Default: Default VPCs provide ease of use but may not meet specific security or organizational needs. Custom VPCs offer greater control over IP ranges, subnets, and routing.
Create Multiple Subnets: Design multiple subnets within your VPC to separate resources logically. This separation can enhance security and network efficiency.
2. Implement Robust Security Measures
Firewall Rules: Implement least privilege access by configuring firewall rules. Ensure that only necessary ports and IP ranges are open.
VPC Service Controls: Utilize VPC Service Controls to create a security perimeter around your GCP resources to prevent data exfiltration.
Private Google Access: Enable Private Google Access for services that need to access Google APIs and services without exposing traffic to the public internet.
3. Optimize for Performance and Reliability
Region and Zone Selection: Choose regions and zones that are closest to your user base to reduce latency. Also, consider the geographical distribution for disaster recovery.
Dynamic Routing: Use dynamic routing for automatic network route updates. This ensures optimal paths for traffic and reduces manual route management.
Use Cloud Load Balancing: Implement Cloud Load Balancing for distributing user traffic across multiple instances, improving performance and availability.
4. Cost Management Subnetting Strategy: Efficiently plan your subnets to avoid underutilization or overprovisioning of network resources, which can lead to unnecessary costs.
Monitor Network Traffic: Regularly monitor network traffic and usage patterns to identify opportunities for optimization and cost reduction.
5. Regular Audits and Compliance Conduct Regular Audits
Regularly audit your VPC setup to ensure compliance with internal policies and external regulations.Logging and Monitoring: Enable VPC Flow Logs and Cloud Monitoring to track network performance and detect anomalies.
6. Best Practices for Hybrid and Multi-cloud Setups
Cloud Interconnect and VPN: For hybrid cloud environments, use Cloud Interconnect for a high-speed, direct connection or Cloud VPN for encrypted connections over the public internet.
Consistent Network Policies: Maintain consistent network policies across cloud environments to streamline management and security.
Planning and Design:
Before embarking on the creation of your Google Cloud Platform (GCP) Virtual Private Cloud (VPC), it is crucial to engage in meticulous planning and design. Take into consideration various factors such as resource placement, IP addressing, and future scalability requirements. A well-thought-out network architecture is essential for the efficient operation and management of your cloud infrastructure. This planning phase lays the foundation for a scalable and resilient VPC.
Use of Subnetting:
One of the key strategies in optimizing your GCP VPC is the use of subnetting. Subnets allow you to effectively organize and segment your resources, facilitating better resource management and enhancing security by isolating workloads. By logically dividing your network into subnets, you can assign specific IP ranges to different segments, providing granular control over communication between resources and improving overall network efficiency.
Firewall Rules:
To ensure the security of your GCP VPC, it is imperative to define explicit firewall rules. These rules control inbound and outbound traffic to and from your resources. Regularly auditing and updating these firewall rules is essential to align them with your organization’s evolving security policies. Implementing a proactive approach to firewall management helps fortify your VPC against potential security threats and ensures that access controls remain effective.
Dynamic Routing:
In scenarios where connectivity between your on-premises network and your GCP VPC is a requirement, consider implementing Cloud Router for dynamic routing. Dynamic routing allows for automatic updates to the network routing tables, optimizing the flow of traffic between different network segments. This is especially valuable in hybrid cloud setups, providing a seamless and efficient communication channel between on-premises and cloud environments.
Monitoring and Logging:
Implementing robust monitoring and logging practices is critical for maintaining the security and performance of your GCP VPC. Monitoring tools can track network activity, detect anomalies, and provide insights into potential security incidents. By leveraging logging services, you can gather detailed information about events within your VPC, enabling a timely response to security threats and ensuring compliance with regulatory requirements.
Regular Audits:
Periodic audits of your VPC configuration are essential to ensure ongoing alignment with best practices and compliance with security standards. Regular reviews help identify any misconfigurations or vulnerabilities that may have emerged over time. By conducting audits at predetermined intervals, you can proactively address issues and make necessary adjustments to enhance the overall security and efficiency of your GCP VPC.
Documentation:
Maintaining comprehensive documentation of your GCP VPC setup is a fundamental practice for effective management and troubleshooting. Document network diagrams, IP addressing schemes, and firewall rules to provide a clear reference for administrators and support teams. This documentation not only aids in troubleshooting but also facilitates knowledge transfer within the organization, ensuring that all stakeholders have a comprehensive understanding of the VPC architecture and its components.
Conclusion
Mastering the setup of a GCP Virtual Private Cloud is a fundamental skill for cloud architects and administrators. This guide has provided a detailed walkthrough of the key concepts, setup process, and advanced configurations of GCP VPC. By following best practices and staying informed about updates and new features, you can build and manage secure, scalable, and efficient cloud networks on Google Cloud Platform. As you continue to explore GCP’s vast ecosystem, the knowledge gained from this guide will serve as a solid foundation for your cloud journey.
Subnetting allows you to divide a VPC’s IP address range into subnetworks, enabling better organization and control over routing and firewall rules within the VPC.
Yes, you can specify a custom IP address range when creating a VPC. However, once a VPC is created, you cannot modify its IP address range.
You can establish a VPN (Virtual Private Network) or use Cloud Interconnect to connect your on-premises network to a GCP VPC.
A firewall rule controls incoming and outgoing traffic to and from instances in a VPC. You can define rules based on IP addresses, protocols, and ports.
Yes, VPC peering allows you to connect VPCs in the same or different projects, enabling communication between instances in those VPCs.