Introduction to the AWS Shared Responsibility Model:
AWS’s Responsibility: AWS is responsible for the security “of” the cloud. This means AWS manages the security of the underlying infrastructure, such as hardware, software, networking, and facilities that run the AWS cloud services. They also ensure compliance with industry standards and regulations, provide security features within their services, and offer tools for customers to enhance their security posture.
Customer’s Responsibility: The customer is responsible for the security “in” the cloud. This includes securing the data, managing user access, configuring network security, and implementing security best practices within the applications and workloads they deploy on AWS. Customers are also responsible for implementing appropriate security controls and measures to protect their data and applications.
Clarifying the division of security responsibilities between AWS and the customer:
AWS-Managed Services: These are services where AWS is responsible for security “of” the cloud. This includes services like Amazon S3 (Simple Storage Service), Amazon DynamoDB, and Amazon RDS (Relational Database Service). AWS ensures the security and compliance of these services, including infrastructure security, patch management, and data encryption at rest.
Customer-Managed Services: These are services where the customer has more control and responsibility for security “in” the cloud. This typically includes tasks such as configuring firewall rules, managing user access and permissions, encrypting data in transit, and implementing security monitoring and logging.
Key security considerations for both AWS-managed and customer-managed components:
- Data Encryption: Ensuring data is encrypted both at rest and in transit to protect it from unauthorized access.
- Identity and Access Management (IAM): Properly managing user identities, roles, and permissions to control access to AWS resources.
- Network Security: Configuring security groups, network ACLs (Access Control Lists), and VPC (Virtual Private Cloud) settings to control inbound and outbound traffic.
- Logging and Monitoring: Implementing logging and monitoring solutions to detect and respond to security incidents in a timely manner.
- Compliance and Governance: Ensuring compliance with industry regulations and standards, as well as implementing governance policies to maintain security and compliance posture.
Fundamentals of AWS Security Services
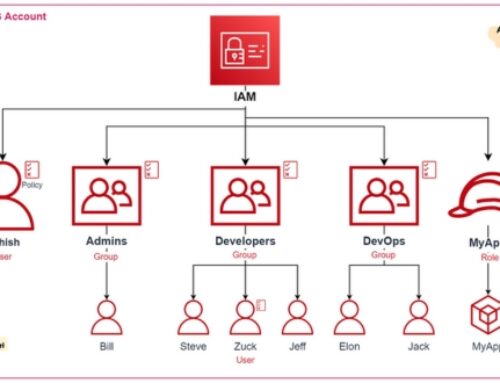
AWS Identity and Access Management (IAM):
IAM is a crucial service that allows you to manage access to AWS services and resources securely.
With IAM, you can create and manage AWS users and groups, and assign permissions to allow or deny their access to specific resources.
IAM provides features such as multi-factor authentication (MFA), identity federation, and integration with other AWS services for fine-grained access control.
AWS Key Management Service (KMS):
KMS is a managed service that makes it easy for you to create and control the encryption keys used to encrypt your data.
It allows you to create and manage keys centrally, and integrate encryption seamlessly into your applications and AWS services.
KMS provides features such as key rotation, auditing, and integration with AWS CloudTrail for logging key usage.
AWS Security Hub:
Security Hub provides a comprehensive view of your security posture across your AWS accounts.
It aggregates and prioritizes security findings from various AWS services, such as Amazon GuardDuty, AWS Inspector, and AWS Firewall Manager.
Security Hub helps you identify security vulnerabilities, compliance issues, and potential threats, and provides actionable insights to remediate them.
AWS Config:
AWS Config enables you to assess, audit, and evaluate the configurations of your AWS resources continuously.
It records and evaluates configurations changes, allowing you to assess compliance with your organization’s policies and industry regulations.
AWS Config provides features such as configuration history, configuration snapshots, and rules to define and enforce compliance checks.
Conducting a Risk Assessment in AWS
Conducting a risk assessment in AWS (Amazon Web Services) involves a systematic evaluation of potential threats and vulnerabilities within your AWS environment to identify risks to the confidentiality, integrity, and availability of your data and resources.
Identifying Assets and Resources within Your AWS Environment:
- Begin by cataloging all assets and resources hosted in your AWS environment. This includes virtual machines, databases, storage buckets, networking components, applications, and any other services utilized.
- Document the purpose, sensitivity, and criticality of each asset to understand its importance to your business operations.
Assessing Vulnerabilities and Threats Specific to Cloud Environments:
- Conduct a thorough assessment of potential vulnerabilities and threats that could impact your AWS infrastructure. These may include misconfigurations, insecure access controls, data breaches, insider threats, DDoS attacks, and more.
- Consider both technical vulnerabilities and human factors such as user errors or malicious activities.
Prioritizing Risks Based on Severity and Impact on Business Operations:
- Evaluate the identified risks based on their likelihood of occurrence and potential impact on your business operations.
- Classify risks according to their severity levels (e.g., low, medium, high) and prioritize mitigation efforts accordingly.
- Factors to consider when prioritizing risks include the value of the asset, the sensitivity of the data it stores, regulatory requirements, and potential financial losses.
Implementing Risk Mitigation Strategies and Controls:
- Develop and implement risk mitigation strategies and controls to address identified vulnerabilities and threats.
- These strategies may include implementing encryption mechanisms, enforcing access controls, regularly patching and updating software, monitoring for suspicious activities, implementing multi-factor authentication, and configuring network security measures such as firewalls.
- Ensure that mitigation efforts align with industry best practices, AWS security recommendations, and any applicable regulatory requirements.
- Continuously monitor and review your risk mitigation measures to adapt to evolving threats and changes in your AWS environment.
Throughout the risk assessment process, collaboration between various stakeholders such as IT teams, security professionals, compliance officers, and business leaders is crucial to ensure comprehensive coverage and effective risk management within your AWS environment. Regularly reassessing risks and refining mitigation strategies is essential to maintaining a secure and resilient cloud infrastructure.
Securing AWS Infrastructure
Best practices for securing AWS Virtual Private Clouds (VPCs):
AWS Virtual Private Cloud (VPC) is a virtual network dedicated to your AWS account. Implementing best practices for securing VPCs involves securely designing the network architecture, such as using private subnets for sensitive resources, employing strong authentication mechanisms for accessing VPC resources, and restricting access through the use of network ACLs and security groups.
Implementing network security controls using AWS Security Groups and Network ACLs:
AWS Security Groups act as virtual firewalls for EC2 instances and other AWS resources. They control inbound and outbound traffic at the instance level by specifying allowed protocols, ports, and IP ranges. Network Access Control Lists (ACLs) operate at the subnet level and provide an additional layer of security by filtering traffic at the network level.
Configuring AWS WAF (Web Application Firewall) for protecting web applications:
AWS Web Application Firewall (WAF) is a managed service that helps protect web applications from common web exploits that could affect application availability, compromise security, or consume excessive resources. WAF allows you to create rules to filter and monitor HTTP and HTTPS traffic to your web applications.
Utilizing AWS Shield for DDoS (Distributed Denial of Service) protection:
AWS Shield is a managed Distributed Denial of Service (DDoS) protection service that safeguards applications running on AWS against large-scale attacks. AWS Shield Standard provides protection against common and most frequently occurring infrastructure layer (Layer 3 and 4) DDoS attacks, while AWS Shield Advanced offers additional protection against more sophisticated and larger attacks, along with 24/7 support from AWS DDoS Response Team (DRT).
Data Protection in AWS
Encryption at Rest and in Transit:
- Encryption at rest involves securing data stored in AWS services such as Amazon S3, Amazon RDS, or Amazon EBS volumes using encryption keys managed by AWS Key Management Service (KMS). This ensures that even if unauthorized individuals gain access to the underlying storage, the data remains unintelligible without the encryption keys.
- Encryption in transit involves securing data as it moves between different systems or services within the AWS infrastructure. This can be achieved using protocols such as TLS/SSL for communication between clients and AWS services or between different AWS services.
Managing Data Access Controls and Permissions:
AWS Identity and Access Management (IAM) allows administrators to manage access to AWS services and resources securely. IAM enables the creation of policies that define who can access specific resources and what actions they can perform. By carefully configuring IAM policies, organizations can ensure that only authorized individuals or systems have access to sensitive data.
Leveraging AWS Data Loss Prevention (DLP) Tools:
AWS offers various tools and services for data loss prevention, such as Amazon Macie. Macie uses machine learning to automatically discover, classify, and protect sensitive data stored in AWS. It can identify personally identifiable information (PII), financial data, and other types of sensitive data, helping organizations to enforce compliance and prevent data leaks or unauthorized access.
Securing Data Backups and Disaster Recovery Mechanisms:
It’s crucial to ensure that data backups are securely stored and protected against unauthorized access or tampering. AWS offers services like Amazon S3 for durable and scalable object storage, which can be used for storing backup data securely. Additionally, organizations should implement robust disaster recovery mechanisms using services like AWS Backup or AWS Disaster Recovery Services to ensure business continuity in the event of data loss or system failures.
Monitoring and Incident Response
Setting up logging and monitoring using AWS CloudWatch:
AWS CloudWatch is a monitoring and observability service provided by Amazon. It allows you to collect and track metrics, monitor log files, set alarms, and automatically react to changes in your AWS resources. Setting up logging involves configuring CloudWatch to collect logs from various AWS services such as EC2 instances, Lambda functions, and RDS databases. By monitoring these logs, you can gain insights into the health and performance of your AWS environment, detect anomalies, and troubleshoot issues.
Configuring AWS CloudTrail for auditing and tracking API activity:
AWS CloudTrail is a service that enables governance, compliance, operational auditing, and risk auditing of your AWS account. It records API calls made on your account and delivers log files containing information about those calls. By configuring CloudTrail, you can track who has accessed your AWS resources, what actions they performed, and when the actions occurred. This information is crucial for security, compliance, and troubleshooting purposes.
Establishing incident response procedures and protocols:
Incident response procedures are plans and processes designed to detect, respond to, and recover from security incidents in a timely and effective manner. This involves identifying potential security threats, defining roles and responsibilities for incident responders, establishing communication channels, and outlining steps to contain and mitigate the impact of incidents. Incident response protocols may include steps such as initial assessment, containment, eradication, recovery, and post-incident analysis.
Leveraging AWS Incident Response services for timely threat detection and response:
AWS provides various services and features to help organizations detect and respond to security threats effectively. This includes services like AWS GuardDuty for threat detection, AWS Security Hub for centralized security management, and AWS Inspector for vulnerability assessment. By leveraging these services, organizations can enhance their ability to detect and respond to security incidents in real-time, reducing the time to identify and mitigate threats.
Compliance and Governance in AWS
Compliance and governance in AWS (Amazon Web Services) refer to the set of practices and tools used to ensure that cloud infrastructure and applications meet regulatory requirements, industry standards, and internal policies. Here’s a more detailed explanation of each aspect mentioned:
Understanding compliance requirements and industry standards:
This involves identifying the specific regulations, standards, and internal policies that your organization must adhere to. This could include industry-specific regulations such as GDPR (General Data Protection Regulation), HIPAA (Health Insurance Portability and Accountability Act), PCI DSS (Payment Card Industry Data Security Standard), or governmental regulations like SOC 2 (System and Organization Controls 2). Understanding these requirements is crucial for designing and maintaining a compliant AWS environment.
Implementing AWS Config Rules and AWS Trusted Advisor:
AWS Config Rules is a service that allows you to define and enforce rules for your AWS resources’ configurations. These rules can help ensure that your infrastructure complies with best practices, security standards, and regulatory requirements. AWS Trusted Advisor is a service that provides best practice recommendations for optimizing your AWS environment across various dimensions including cost optimization, performance, security, and fault tolerance. By leveraging both AWS Config Rules and Trusted Advisor, organizations can continuously monitor their AWS environment for compliance issues and take proactive measures to address them.
Leveraging AWS Artifact for accessing compliance reports and documentation:
AWS Artifact is a service that provides on-demand access to AWS compliance reports and documentation. These include reports such as SOC reports, PCI DSS compliance packages, and certifications like ISO 27001. By using AWS Artifact, organizations can easily access the documentation necessary to demonstrate compliance to auditors, regulators, and other stakeholders.
Integrating third-party compliance tools with AWS services:
Many organizations use third-party compliance tools and services to augment the capabilities of AWS-native tools. These tools may offer specialized features, deeper insights, or support for specific regulatory requirements. Integration with AWS services allows organizations to leverage the benefits of both AWS and third-party tools seamlessly. Common areas where third-party tools are integrated include vulnerability management, threat detection, log management, and compliance reporting.
Compliance and governance in AWS involve a combination of understanding regulatory requirements, implementing AWS-native tools like Config Rules and Trusted Advisor, accessing compliance documentation through AWS Artifact, and integrating third-party tools to enhance compliance capabilities. By adopting these practices, organizations can ensure that their AWS environments are secure, compliant, and well-governed.
Continuous Improvement and Optimization
- Implementing a culture of continuous improvement and learning: This involves fostering a mindset within the organization where security is not seen as a one-time task but rather as an ongoing process. It includes promoting awareness among employees about the importance of security, encouraging them to stay updated with the latest security trends and practices, and providing avenues for continuous learning such as training sessions, workshops, and knowledge-sharing forums.
- Conducting regular security assessments and audits: Regular security assessments and audits are essential to identify vulnerabilities, weaknesses, and compliance gaps in the AWS environment. These assessments can include vulnerability scanning, penetration testing, configuration audits, and compliance checks against relevant standards and regulations. By conducting these assessments on a periodic basis, organizations can proactively identify and address security issues before they can be exploited by attackers.
- Staying updated with AWS security best practices and emerging threats: AWS regularly updates its security best practices and guidelines to help organizations protect their cloud environments effectively. It’s crucial for organizations to stay abreast of these updates and incorporate them into their security policies and procedures. Additionally, staying informed about emerging threats and vulnerabilities specific to AWS services and configurations is essential for maintaining a proactive defense posture.
- Leveraging AWS Managed Services for ongoing security monitoring and management: AWS offers various managed services that can help organizations streamline and automate security monitoring and management tasks. These services, such as AWS Security Hub, AWS Guard Duty, AWS Config, and AWS Identity and Access Management (IAM), provide centralized visibility into security-related activities, automate threat detection and remediation, and enforce security policies across the AWS environment. By leveraging these managed services, organizations can enhance their security posture while reducing the operational burden associated with managing security infrastructure.
Conclusion:
In an era marked by digital transformation and cloud adoption, safeguarding your organization’s assets in the AWS cloud is paramount. By understanding the intricacies of AWS cloud security assessment and implementing robust security measures, businesses can mitigate risks effectively and embrace the full potential of cloud computing with confidence. Remember, security is not a destination but a journey—an ongoing effort that requires vigilance, adaptation, and collaboration across all levels of the organization.
It’s crucial for ensuring the confidentiality, integrity, and availability of data and resources stored and processed in the AWS cloud, protecting against cyber threats and compliance violations.
Key components typically include evaluating AWS Identity and Access Management (IAM), network security, data encryption, logging and monitoring, compliance with industry standards, and best practices.
Assessments should be conducted regularly, ideally on a quarterly or annual basis, or whenever significant changes are made to the AWS environment.
Qualified security professionals with expertise in AWS cloud security should conduct these assessments. Alternatively, organizations may engage third-party security firms specializing in cloud security.
Common risks include misconfigured security settings, unauthorized access, data breaches, insider threats, insecure APIs, lack of encryption, and inadequate logging and monitoring.