Introduction of AWS Compliance and Governance
In the rapidly evolving landscape of cloud computing, ensuring compliance has become a paramount concern for businesses across various industries. Compliance refers to adhering to a set of regulations, standards, and best practices designed to safeguard sensitive data, maintain privacy, and uphold the integrity of operations. In the context of cloud environments, compliance becomes even more critical due to the shared responsibility model between cloud service providers and their customers.
Importance of Compliance in Cloud Environments:
In cloud environments, businesses entrust cloud service providers, such as Amazon Web Services (AWS), with the responsibility of managing infrastructure, networking, and other core services. However, customers retain responsibility for securing their data, configuring access controls, and ensuring compliance with industry-specific regulations. Failure to meet compliance requirements can result in severe consequences, including legal liabilities, financial penalties, and reputational damage.
AWS Governance and Compliance Services:
AWS recognizes the importance of providing robust tools and services to help customers achieve and maintain compliance in their cloud environments. AWS offers a comprehensive suite of governance and compliance services that empower organizations to build and operate secure and compliant workloads. These services span across various aspects of compliance, including data protection, access control, auditing, and more.
Some key AWS services related to governance and compliance include:
- AWS Organizations:
AWS Organizations allows customers to consolidate multiple AWS accounts into an organization to simplify billing and provide centralized management of accounts.
- Service Control Policies (SCPs):
SCPs, a feature of AWS Organizations, enable customers to set fine-grained permissions and controls across their accounts, ensuring compliance with organizational policies.
- AWS Control Tower:
AWS Control Tower is a service that simplifies the process of setting up and governing a secure, multi-account AWS environment based on AWS best practices.
- AWS Config:
AWS Config provides a detailed inventory of AWS resources, tracks changes, and enables compliance by assessing resource configurations against desired settings.
- AWS CloudTrail:
AWS CloudTrail records API calls and actions taken on AWS resources, providing visibility into user activity and changes for compliance and security analysis.
- AWS Security Hub:
AWS Security Hub aggregates security findings from various AWS services, helping customers prioritize and remediate security and compliance issues.
By leveraging these services, businesses can establish a robust governance framework and meet compliance requirements, ensuring a secure and resilient cloud environment.
Key Concepts in AWS Compliance
In the realm of AWS compliance, several key concepts lay the foundation for building and maintaining secure and resilient cloud environments. Understanding these concepts is crucial for organizations seeking to navigate the complex landscape of compliance requirements and leverage the capabilities provided by AWS. Let’s delve into three key concepts: the Shared Responsibility Model, the AWS Well-Architected Framework, and Compliance as Code.
Shared Responsibility Model:
At the core of AWS compliance is the Shared Responsibility Model, a fundamental concept that outlines the division of responsibilities between AWS and its customers. In this model:
- AWS manages the security of the cloud, encompassing the infrastructure, hardware, software, and facilities that run AWS services.
- Customers are responsible for the security in the cloud, which includes securing data, configuring access controls, and implementing security best practices within their AWS environment.
Understanding this delineation is crucial for organizations as it helps establish clear accountability and guides the implementation of security measures to meet compliance requirements.
AWS Well-Architected Framework:
The AWS Well-Architected Framework is a set of best practices designed to help organizations build secure, high-performing, resilient, and efficient infrastructure for their applications. The framework consists of five pillars:
- Operational Excellence:
- Focuses on operational practices to deliver business value. It includes monitoring, incident response, and evolving procedures over time.
- Security:
- Prioritizes implementing strong identity controls, conducting regular audits, and protecting data confidentiality and integrity.
- Reliability:
- Ensures a workload can recover from failures and meet customer demands by designing for resiliency and anticipating failure scenarios.
- Performance Efficiency:
- Optimizes workload performance based on requirements, using resources efficiently to meet business needs.
- Cost Optimization:
- Seeks to avoid unnecessary costs by understanding and controlling where money is being spent, selecting the right resources, and monitoring spending over time.
- Adhering to the principles of the Well-Architected Framework aids organizations in building compliant architectures that align with industry best practices.
Compliance as Code:
Compliance as Code represents a modern approach to implementing and enforcing compliance controls through code and automation. By treating compliance as code, organizations can:
- Define compliance policies and controls using code-based configurations.
- Automate the enforcement of these policies, ensuring consistent and auditable compliance across their infrastructure.
This approach enhances agility, allows for rapid scalability, and facilitates continuous compliance monitoring. Tools like AWS Config, AWS CloudFormation, and infrastructure as code (IaC) frameworks play crucial roles in implementing Compliance as Code practices.
AWS Compliance Standards and Certifications
Navigating the complex landscape of compliance standards and certifications is essential for organizations utilizing AWS services. This section provides an in-depth exploration of common compliance standards, AWS-specific certifications, and the documentation and resources available for ensuring compliance within the AWS environment.
Overview of Common Compliance Standards:
- GDPR (General Data Protection Regulation):
- Focuses on protecting the privacy and personal data of European Union (EU) citizens.
- Key components include data subject rights, lawful processing, and data breach notifications.
- HIPAA (Health Insurance Portability and Accountability Act):
- Enforces standards for securing protected health information (PHI) in the healthcare industry.
- Emphasizes safeguards, access controls, and audit controls to protect patient data.
- SOC 2 (Service Organization Control 2):
- Developed by the American Institute of CPAs (AICPA), SOC 2 focuses on the security, availability, processing integrity, confidentiality, and privacy of customer data.
- Commonly used for technology and cloud computing organizations.
- ISO 27001:
- An international standard for information security management systems (ISMS).
- Emphasizes a risk-based approach to security, encompassing policies, processes, and controls.
- PCI DSS (Payment Card Industry Data Security Standard):
- Mandated for organizations handling credit card transactions.
- Focuses on securing payment card data through encryption, access controls, and regular security assessments.
Understanding these standards is crucial for organizations, as compliance with them demonstrates a commitment to data security, privacy, and regulatory requirements.
AWS Compliance Certifications:
AWS undergoes rigorous assessments and certifications to demonstrate its commitment to security and compliance. Key certifications include:
- FedRAMP (Federal Risk and Authorization Management Program):
- Authorizes AWS to handle U.S. government data with a focus on security and risk management.
- FISMA (Federal Information Security Management Act):
- Enables federal agencies to adopt secure cloud services, ensuring compliance with FISMA requirements.
- PCI DSS:
- AWS is PCI DSS Level 1 certified, providing a secure environment for handling payment card data.
- ISO 27001:
- AWS maintains ISO 27001 certification, validating its commitment to information security.
Understanding these certifications is crucial for organizations selecting AWS as their cloud provider, as it ensures that AWS adheres to industry-specific compliance requirements.
Compliance Documentation and Resources:
AWS provides extensive documentation and resources to assist organizations in achieving and maintaining compliance. These include:
- AWS Artifact:
- A self-service portal offering on-demand access to AWS compliance reports and other documentation.
- AWS Compliance Center:
- A dedicated resource hub providing information on AWS’s compliance with various standards and regulations.
- AWS Well-Architected Tool:
- Offers best practices and recommendations for building secure and compliant workloads in the cloud.
Accessing these resources empowers organizations to stay informed, implement best practices, and demonstrate compliance to stakeholders and regulatory bodies.
Governance Best Practices in AWS
Effectively managing and governing AWS resources is paramount for organizations to maintain compliance, security, and operational efficiency. This section delves into governance best practices within AWS, emphasizing key tools and services designed to streamline the management of multiple accounts and enforce policies across diverse environments.
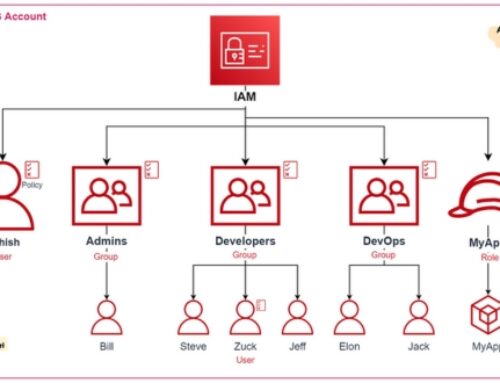
AWS Organizations:
- Managing Multiple AWS Accounts:
- AWS Organizations provides a centralized framework for managing multiple AWS accounts.
- Enables organizations to create, move, and remove accounts, facilitating better governance and resource organization.
- Organizational Units (OUs):
- Utilizing OUs within AWS Organizations to group accounts based on business units, applications, or environments.
- Streamlines policy application and simplifies resource management within the organizational structure.
Service Control Policies (SCPs):
- Policy Definition and Enforcement:
- SCPs in AWS Organizations define permission guardrails that apply to member accounts.
- Enables organizations to set fine-grained controls on AWS service access, ensuring adherence to security and compliance requirements.
- Policy Application to OUs and Accounts:
- Applying SCPs at the OU level to enforce policies across specific segments of the organization.
- SCPs provide granular control over which AWS services and actions are allowed or denied.
AWS Control Tower:
- Setting Up a Secure, Multi-Account Environment:
- AWS Control Tower automates the setup of a secure, multi-account AWS environment.
- Establishes a landing zone with best practices, ensuring a well-architected foundation for workloads.
- Account Vending and Onboarding:
- Facilitates the creation and onboarding of new accounts with predefined guardrails and policies.
- Simplifies the process of scaling the AWS environment while maintaining governance standards.
Automated Landing Zone:
- Establishing a Secure Baseline:
- AWS Control Tower creates an automated landing zone that adheres to AWS best practices.
- Ensures that new accounts and workloads start with a secure baseline, minimizing security risks.
AWS Single Sign-On (SSO):
- Centralized Identity Management:
- AWS SSO simplifies identity management by providing centralized user access control.
- Integrates with AWS Organizations, enabling organizations to manage user access across accounts centrally.
Implementing these governance best practices empowers organizations to maintain control, security, and compliance across their AWS environments. As we progress, we will explore additional aspects of compliance and governance, including auditability, risk management, and strategies for continuous improvement.
Identity and Access Management (IAM) for Compliance
In the realm of AWS compliance, Identity and Access Management (IAM) serves as a foundational component, providing a robust framework for managing user access, permissions, and ensuring compliance with various industry standards. This section delves into IAM basics, the implementation of Role-Based Access Control (RBAC), and best practices for IAM to meet compliance requirements.
IAM Basics:
- Access Management Overview:
- IAM is AWS’s service for managing access to AWS resources securely.
- Centralized control over AWS account users, groups, and permissions.
- User Authentication and Authorization:
- IAM facilitates user authentication and authorization, ensuring that only authenticated and authorized entities access AWS resources.
- Leverages username and password or AWS Identity Federation for authentication.
- IAM Policies:
- Policies in IAM define permissions for actions in AWS resources.
- Policies are JSON documents that specify the actions allowed or denied, the resources involved, and the conditions under which actions are allowed or denied.
Role-Based Access Control (RBAC):
- Fine-Grained Access Control:
- RBAC in IAM allows organizations to define roles that grant specific permissions to entities.
- Roles are assigned to users, groups, or services based on their responsibilities.
- Least Privilege Principle:
- Implementing the least privilege principle by assigning the minimum necessary permissions to perform tasks.
- Ensures that entities have access only to the resources required for their specific roles.
IAM Best Practices for Compliance:
- Regularly Review and Rotate Credentials:
- Implementing a credential rotation policy to enhance security.
- Regularly reviewing and rotating IAM user access keys and secret access keys.
- Use IAM Roles for AWS Services:
- Leveraging IAM roles for AWS services to grant permissions dynamically.
- Enhances security by reducing the need for static credentials.
- Multi-Factor Authentication (MFA):
- Enforcing MFA for IAM users to add an extra layer of security.
- MFA helps protect against unauthorized access, especially for users with elevated privileges.
- Audit IAM Policies:
- Regularly auditing IAM policies to ensure they align with compliance requirements.
- Removing unnecessary permissions and maintaining an up-to-date understanding of access controls.
IAM’s role in compliance extends beyond access management, contributing to the establishment of a secure and well-governed AWS environment.
Security Automation and Monitoring
In the realm of security automation and monitoring within AWS, two key services—AWS Config and AWS Security Hub—play pivotal roles in ensuring adherence to compliance standards and promptly identifying security issues.
AWS Config:
- Monitoring Resource Configurations:
- AWS Config continuously monitors and records configurations of AWS resources.
- Provides a historical view of resource changes, aiding in compliance audits.
- Rule-Based Evaluation:
- Config allows the creation of rules that define desired configurations.
- Rules evaluate whether the current configurations comply with predefined policies.
- Automated Remediation:
- Config supports automated remediation through AWS Systems Manager Automation.
- Enables the automatic correction of non-compliant configurations.
- Change Tracking:
- Captures changes to resource configurations, allowing organizations to understand the impact of alterations.
- Facilitates tracking changes across AWS accounts and regions.
AWS Security Hub:
- Centralized Security Findings:
- Security Hub aggregates security findings from various AWS services and integrated third-party solutions.
- Provides a centralized view of security alerts and vulnerabilities.
- Prioritizing Security Issues:
- Security Hub prioritizes security findings based on severity and provides insights into the overall security posture.
- Allows organizations to focus on addressing the most critical issues first.
- Automated Compliance Checks:
- Integrates with AWS Config to perform automated compliance checks.
- Ensures that resource configurations align with compliance standards.
- Custom Actions and Insights:
- Enables the creation of custom actions for responding to security findings.
- Provides actionable insights and recommendations for remediation.
By leveraging AWS Config and Security Hub, organizations can automate the monitoring of resource configurations and consolidate security findings, contributing to a proactive approach to compliance and security. These services empower businesses to swiftly identify and address potential vulnerabilities, thereby enhancing the overall resilience of their AWS environments.
As we navigate through AWS compliance and governance, the integration of security automation and monitoring becomes crucial for maintaining a secure and compliant infrastructure.
Data Encryption and Compliance
When it comes to data encryption and compliance in AWS, safeguarding sensitive information is paramount. Employing encryption both in transit and at rest is a fundamental practice to meet regulatory requirements and protect data integrity.
Encryption in Transit and at Rest:
- Secure Data Transmission:
- AWS ensures the use of secure communication protocols, such as TLS, for encrypting data during transit.
- Safeguards against unauthorized interception and ensures compliance with encryption standards.
- Data at Rest Encryption:
- AWS provides services like Amazon S3 and Amazon EBS that support encryption of stored data.
- Encryption at rest mitigates the risk of unauthorized access to data residing in storage.
AWS Key Management Service (KMS):
- Centralized Key Management:
- AWS KMS is a fully managed service for creating and controlling encryption keys.
- Offers centralized key management to simplify and enhance the security of data encryption.
- Granular Access Controls:
- KMS allows organizations to define granular access controls on keys.
- Ensures that only authorized entities can encrypt or decrypt data, aligning with compliance requirements.
- Integration with AWS Services:
- KMS seamlessly integrates with various AWS services, facilitating the encryption of data across the entire infrastructure.
- Provides a consistent and scalable approach to managing encryption keys.
By embracing encryption in transit and at rest, and leveraging AWS KMS for robust key management, organizations fortify their data protection mechanisms. This not only aligns with compliance standards but also instills confidence in customers and stakeholders regarding the security and privacy of sensitive information.
Audit and Compliance Reporting in AWS
- AWS CloudTrail for Comprehensive Tracking:
- Purposeful Monitoring: AWS CloudTrail serves as a comprehensive auditing tool, allowing organizations to monitor and log user activity, API usage, and resource changes.
- Transparent Trail of Actions: By recording every interaction with AWS resources, CloudTrail provides a transparent trail of actions, aiding in forensic analysis and compliance audits.
- Generating Compliance Reports:
- Automated Report Generation: AWS offers tools and services that facilitate the automated generation of compliance reports.
- Customizable Reports: Organizations can tailor these reports to align with specific compliance requirements, ensuring a detailed overview of adherence to industry standards.
- Visibility into User Actions:
- User Accountability: CloudTrail provides visibility into which users are performing specific actions, enhancing accountability and helping meet compliance mandates that require traceability.
- Investigation and Analysis: In the event of a security incident or the need for a compliance audit, CloudTrail logs serve as a valuable resource for investigation and analysis.
- Integration with Other AWS Services:
- Centralized Logging: CloudTrail seamlessly integrates with other AWS services, ensuring centralized and standardized logging of activities across the entire cloud infrastructure.
- Holistic Compliance Overview: The integration allows organizations to maintain a holistic view of compliance across various AWS services and resources.
- Real-Time Monitoring and Alerts:
- Alerting Mechanisms: CloudTrail supports real-time monitoring and alerting, enabling organizations to respond promptly to suspicious activities and potential compliance violations.
- Proactive Compliance Management: Real-time alerts empower organizations to proactively manage compliance, addressing issues as they arise rather than retroactively.
By leveraging AWS CloudTrail for audit trail creation and utilizing AWS tools for compliance report generation, organizations ensure not only adherence to regulatory standards but also a proactive stance in maintaining a secure and compliant cloud environment. This comprehensive approach to audit and compliance reporting aligns with industry best practices and fosters a culture of continuous improvement in governance.
Cost Optimization and Compliance:
- Understanding Cost Implications of Compliance:
- Balancing Act: Achieving and maintaining compliance involves certain costs, including investments in tools, personnel training, and adherence to specific standards.
- Total Cost of Compliance: Organizations need to assess the total cost of compliance, considering both direct and indirect expenses associated with meeting regulatory requirements.
- Cost-Effective Compliance Strategies:
- Strategic Resource Allocation: Optimizing costs while ensuring compliance requires strategic resource allocation. It involves identifying areas where efficiency gains can be made without compromising regulatory obligations.
- Leveraging Cloud Economics: Cloud providers like AWS offer scalable and pay-as-you-go models, allowing organizations to align their compliance efforts with cost-effective cloud solutions.
- Automation for Efficiency:
- Automated Compliance Checks: Implementing automation in compliance processes can significantly reduce manual efforts and associated costs.
- Continuous Monitoring: Automation facilitates continuous monitoring, enabling real-time compliance checks without incurring excessive operational expenses.
- Training and Skill Development:
- Investment in Knowledge: Building internal expertise through training programs and skill development is an investment that pays off in terms of operational efficiency and reduced dependency on external resources.
- Long-Term Cost Savings: Well-trained teams are more adept at managing compliance-related tasks efficiently, contributing to long-term cost savings.
- Scalability and Elasticity:
- Scalable Solutions: Leveraging scalable solutions on cloud platforms allows organizations to adapt to changing compliance requirements without incurring significant upfront costs.
- Elasticity for Flexibility: The elasticity of cloud resources provides the flexibility to scale compliance efforts up or down based on evolving needs, optimizing costs in the process.
Balancing the costs of compliance with effective strategies for optimization is essential for organizations aiming to meet regulatory standards without unnecessary financial burdens. By adopting a proactive and strategic approach, businesses can align compliance efforts with cost-effective practices, ensuring a sustainable and efficient governance model.
Future Trends in AWS Compliance and Governance:
- Evolving Compliance Standards:
- Dynamic Regulatory Landscape: As technology advances and global challenges emerge, compliance standards are expected to evolve. Organizations should anticipate changes in regulations, ensuring a proactive approach to meet future compliance requirements.
- Adaptive Frameworks: The future will likely witness the emergence of more adaptive compliance frameworks that can swiftly accommodate alterations in regulatory landscapes without causing significant disruptions.
- Integration of AI in Compliance:
- AI-Driven Compliance Solutions: The integration of Artificial Intelligence (AI) in compliance processes is poised to revolutionize the way organizations ensure adherence to standards.
- Automated Risk Assessment: AI algorithms can enhance risk assessment by analyzing vast datasets, identifying patterns, and predicting potential compliance issues. This automated approach promises more accurate and efficient risk management.
- Blockchain for Immutable Records:
- Immutable Records: The use of blockchain technology may become more prevalent for creating immutable and transparent records of compliance-related activities. This can enhance the verifiability and integrity of compliance data.
- Enhanced Cloud-Native Compliance Tools:
- Cloud-Native Compliance Solutions: With the increasing adoption of cloud-native architectures, compliance tools are likely to be further optimized for seamless integration with cloud environments.
- Automated Auditing: Cloud platforms, including AWS, may introduce more sophisticated automated auditing tools that provide real-time insights into compliance status.
- Focus on Zero Trust Security Models:
- Zero Trust Architecture: Future compliance and governance trends may emphasize the implementation of Zero Trust security models. This approach assumes no inherent trust, requiring continuous verification of entities accessing resources.
Anticipating and adapting to these future trends will position organizations to stay ahead in the dynamic landscape of AWS compliance and governance. By embracing emerging technologies and adopting forward-looking strategies, businesses can proactively address evolving regulatory challenges.
Conclusion: Navigating the Landscape of AWS Compliance and Governance
In the ever-evolving landscape of AWS, compliance and governance stand as paramount pillars for organizations aiming to navigate the complexities of the cloud securely. As regulatory environments shift, organizations leveraging AWS must not only adhere to current standards but also prepare for future developments.
The journey through AWS compliance and governance involves a multifaceted approach, encompassing shared responsibility, well-architected frameworks, and innovative technologies. The evolution of compliance standards necessitates a proactive stance, with organizations embracing adaptive frameworks that can swiftly accommodate changes.
As we look ahead, the integration of Artificial Intelligence promises to revolutionize compliance practices. AI-driven solutions, coupled with blockchain technology for immutable records, will contribute to more robust, efficient, and transparent compliance processes.
The rise of cloud-native compliance tools tailored for AWS environments reinforces the importance of staying abreast of technological advancements. Furthermore, a shift towards Zero Trust security models highlights the industry’s commitment to continuous verification and enhanced security postures.
In conclusion, successfully navigating the AWS compliance and governance landscape requires a commitment to staying informed, embracing innovation, and fostering a culture of proactive adherence to evolving standards. As organizations embark on this journey, they position themselves not just for compliance but for resilience and success in the dynamic realm of AWS.
AWS Compliance and Governance refer to the set of practices and tools employed to ensure that organizations using Amazon Web Services adhere to regulatory standards, manage access securely, and implement best practices for data protection.
The Shared Responsibility Model outlines the responsibilities of AWS and its customers in terms of security and compliance. AWS manages security of the cloud, while customers manage security in the cloud.
AWS adheres to various compliance standards such as GDPR, HIPAA, SOC 2, and more. These standards ensure that AWS services meet specific regulatory requirements.
The AWS Well-Architected Framework provides best practices for building secure, high-performing, resilient, and efficient infrastructure for applications. It serves as a guide for customers to improve their architectures.
AWS Control Tower helps in setting up and governing a secure, multi-account AWS environment. It simplifies the process of provisioning accounts and ensures they adhere to established best practices.