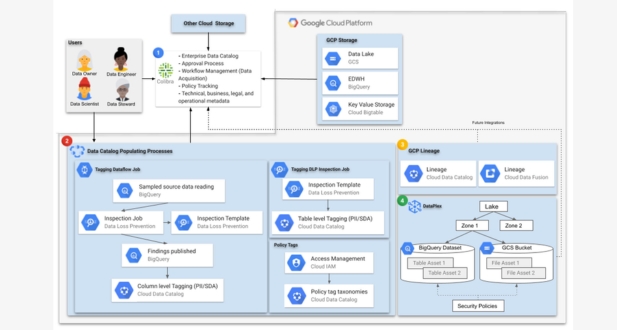
Google Workspace compliance
Introduction
In today’s rapidly evolving digital landscape, organizations are relying more than ever on cloud-based collaboration and productivity tools. Google Workspace, formerly known as G Suite, stands out as one of the leading platforms, offering a suite of applications such as Gmail, Google Drive, Google Docs, and more. As businesses embrace the advantages of Google Workspace, they must also address the critical aspects of compliance and data governance to ensure the security, privacy, and integrity of their data. In this comprehensive guide, we will delve into the intricacies of compliance and data governance within Google Workspace, exploring key concepts, best practices, and tools to navigate the complex seas of data management.
Understanding Compliance in Google Workspace

Compliance refers to adhering to laws, regulations, and industry standards relevant to an organization’s operations. In the context of Google Workspace, compliance encompasses various aspects, including data protection, privacy, and security. Google has implemented robust measures to ensure compliance with global standards such as GDPR (General Data Protection Regulation), HIPAA (Health Insurance Portability and Accountability Act), and more.
GDPR Compliance:
- Data Processing Transparency: Google Workspace allows organizations to maintain transparency in data processing activities, providing insights into how user data is handled within the platform.
- User Consent Management: To comply with GDPR’s consent requirements, Google Workspace enables organizations to manage user consents effectively, ensuring that users have control over their data.
- Right to Be Forgotten: Google Workspace includes features that support the right to be forgotten, allowing organizations to delete user data upon request, as mandated by GDPR.
HIPAA Compliance:
- Business Associate Agreement (BAA): Google Workspace offers a BAA for covered entities and business associates in the healthcare sector. This agreement outlines the measures and safeguards in place to protect sensitive healthcare data, aligning with HIPAA regulations.
- Security Controls: Google Workspace implements stringent security controls to safeguard healthcare information, including encryption, access controls, and audit logs.
Industry-Specific Compliance:
- Sarbanes-Oxley (SOX): Organizations in the finance sector often need to comply with regulations like SOX. Google Workspace provides tools to support financial data management, secure communication, and compliance reporting to meet SOX requirements.
- Other Industry Standards: Depending on the industry, Google Workspace offers features to address specific compliance needs. This includes tools for legal holds, eDiscovery, and audit logs for organizations in the legal sector, and similar tailored features for other industries.
Security Measures:
- Encryption: Google Workspace employs encryption to protect data both in transit and at rest, ensuring the confidentiality and integrity of information.
- Access Controls: Organizations can define and manage access controls to restrict user permissions, reducing the risk of unauthorized access to sensitive data.
- Audit Logs: Detailed audit logs provide a record of user activities, helping organizations track and review actions within the platform for compliance purposes.
Regular Updates and Training:
- Policy Updates: Google Workspace regularly updates its policies to align with evolving compliance standards, ensuring that organizations benefit from the latest security and privacy measures.
- Training Resources: Google provides educational resources and training materials to help organizations and users understand and implement compliance measures effectively.
- By incorporating these features and tools, Google Workspace aims to provide a secure and compliant environment for organizations across various industries. It allows users to leverage the platform’s capabilities while meeting the specific legal and regulatory requirements relevant to their operations.
Data Governance Best Practices in Google Workspace

Data governance involves managing data assets to ensure high data quality, integrity, and security. In the context of Google Workspace, effective data governance practices are essential for maintaining control over data and mitigating risks.
User Access Controls and Permissions:
Regularly review and update access controls: Google Workspace provides administrators with the ability to manage user access to various applications and services. Periodic reviews and updates to access controls help align them with evolving data governance policies and ensure that users have the appropriate level of access based on their roles and responsibilities.
Data Classification and Labeling:
Classify data based on sensitivity: Not all data carries the same level of importance or sensitivity. Google Workspace offers tools for data classification and labeling, allowing organizations to categorize data according to its level of confidentiality. This enables more precise control over data access, sharing, and protection.
Data Loss Prevention (DLP) Policies:
Configure robust DLP policies: Google Workspace’s DLP policies enable organizations to prevent the inadvertent or intentional sharing of sensitive information. Organizations can configure these policies to detect and block the transmission of specific types of data, ensuring compliance with industry regulations and safeguarding against data breaches.
Auditing and Monitoring:
Maintain visibility into user activities: Regularly review audit logs provided by Google Workspace to monitor user activities, file accesses, and administrative actions. This visibility helps organizations identify unusual or suspicious behavior, respond promptly to security incidents, and demonstrate compliance with data governance policies during audits.
Incident Response Planning:
Develop an incident response plan: Despite robust preventive measures, incidents may occur. Establish a well-defined incident response plan that outlines the steps to be taken in the event of a security breach or data incident. This plan should include communication protocols, escalation procedures, and post-incident analysis to continually improve data governance practices.
Data Retention Policies:
Implement clear data retention policies: Define and enforce data retention policies within Google Workspace to ensure that data is retained only for the necessary period. Regularly review and update these policies to align with legal requirements, industry standards, and organizational needs. This helps avoid unnecessary data storage and potential legal issues.
User Training and Awareness:
Educate users on data governance best practices: Conduct regular training sessions to ensure that users are aware of data governance policies and best practices within Google Workspace. This includes proper data handling, adherence to security protocols, and awareness of potential risks. Well-informed users contribute to a more secure and compliant data environment.
Tools and Features for Compliance and Data Governance
Google Workspace provides a range of tools and features designed to assist organizations in achieving compliance and implementing effective data governance.
Google Vault:
- Data Retention and eDiscovery: Google Vault allows organizations to define retention policies for different data types, ensuring compliance with legal and regulatory requirements. It also facilitates eDiscovery, enabling organizations to search and retrieve specific information for legal purposes.
Security Center:
- Threat Monitoring: The Security Center provides real-time insights into potential security threats within Google Workspace. It allows organizations to monitor user activity, and permissions, and identify anomalies that may indicate security risks.
- Vulnerability Management: This feature assists in identifying and addressing potential vulnerabilities in the organization’s security infrastructure.
Advanced Mobile Management (AMM):
- Mobile Device Security: With the rise of mobile workforces, AMM becomes crucial. It allows organizations to enforce security policies on mobile devices, ensuring that corporate data accessed on these devices remains secure.
- Remote Management: In the event of a lost or stolen device, AMM enables remote wipe capabilities, safeguarding sensitive information.
Compliance Manager:
- Centralized Compliance Dashboard: The Compliance Manager provides a centralized dashboard for organizations to track and manage their compliance status. This includes real-time updates on adherence to various regulatory requirements.
- Assessment Management: Organizations can use the tool to conduct and manage compliance assessments, ensuring that they meet the necessary standards.
- Reporting: Compliance Manager generates comprehensive reports, aiding in audits and demonstrating the organization’s commitment to regulatory compliance.
Additional Notes:
- These tools collectively contribute to a comprehensive approach to compliance and data governance within Google Workspace.
- The integration of these features helps organizations maintain control over their data, ensure regulatory compliance, and respond effectively to legal requirements.
- Regular updates and improvements to these tools ensure that organizations stay ahead of emerging threats and evolving compliance standards.
In summary, Google Workspace’s suite of tools and features for compliance and data governance offers organizations the necessary resources to maintain a secure and compliant digital environment.
Collaboration with Confidence: Google Workspace Security Features
Google Workspace prioritizes security in collaboration, offering a robust set of features to ensure the confidentiality and integrity of shared information. These security features contribute to compliance and data governance, addressing the evolving challenges of the digital landscape.
Encryption: Securing Data in Transit and at Rest
Encryption is a cornerstone of data security. Google Workspace employs strong encryption protocols to safeguard data both during transmission and while at rest. This means that even if unauthorized access occurs, the data remains unreadable and unusable without the appropriate decryption keys.
Endpoint Management: Securing Devices and Access Points
As remote work becomes more prevalent, securing endpoints is crucial for effective data governance. Google Workspace includes endpoint management features that enable organizations to enforce security policies on devices accessing the platform. This encompasses device-level encryption, secure access controls, and the ability to remotely wipe data from lost or compromised devices.
Advanced Threat Protection: Guarding Against Cyber Threats
In the dynamic digital landscape, cyber threats are a constant concern. Google Workspace incorporates advanced threat protection mechanisms to guard against phishing, malware, and other cyber threats. These features include real-time scanning of email attachments, link scanning, and proactive detection of suspicious activities, providing a layered defense against evolving threats.
Context-Aware Access: Fine-Tuned Security Controls
Recognizing that not all data and users are equal, Google Workspace introduces context-aware access features. These features enable organizations to apply fine-tuned security controls based on factors such as user location, device status, and network conditions. This adaptability ensures that security measures align with the dynamic nature of modern work environments, offering a more nuanced and responsive approach to data protection.
By integrating these security features into its collaboration tools, Google Workspace aims to create a secure environment where organizations can collaborate with confidence, knowing that their sensitive information is protected against a range of potential threats and vulnerabilities.
Challenges in Achieving Compliance
Integration with Third-Party Compliance Solutions: Many organizations operate in highly regulated industries, such as finance or healthcare, and need to adhere to specific compliance standards and certifications. While Google Workspace provides robust security features, integrating with third-party compliance solutions may be necessary to meet industry-specific requirements and standards.
Policy Enforcement: Defining and enforcing compliance policies consistently across the organization is a challenge. Organizations need to establish and communicate clear policies regarding data handling, sharing, and storage within Google Workspace. Automation tools and regular training sessions can help ensure that employees adhere to these policies.
Data Retention and Deletion: Compliance often involves strict guidelines on data retention and deletion. Organizations must implement policies and procedures within Google Workspace to manage the lifecycle of data, ensuring that information is retained for the required duration and properly deleted when no longer needed.
Continuous Monitoring and Updates: Compliance requirements evolve, and organizations need to adapt to changes in regulations and standards. Continuous monitoring of Google Workspace, regular updates to security configurations, and staying informed about industry developments are essential to maintaining compliance over time.
Employee Awareness and Training: Employees play a crucial role in maintaining compliance. Providing regular training and awareness programs on data security, privacy policies, and compliance guidelines within Google Workspace can help mitigate risks associated with human error and enhance overall compliance posture.
Collaboration with Google Support: In some cases, organizations may face challenges in understanding and implementing specific compliance features within Google Workspace. Collaborating with Google Support and seeking assistance can be beneficial in addressing unique compliance concerns and ensuring that the platform is configured to meet regulatory requirements effectively.
Google’s Role in Ensuring a Secure Environment
Security Certifications:
Google Workspace undergoes regular audits and certifications to adhere to industry-specific compliance standards. These certifications, such as ISO 27001 and SOC 2, demonstrate Google’s commitment to meeting stringent security and privacy requirements. Organizations can rely on these certifications to trust that their data is handled securely within the Google Workspace environment.
Advanced Threat Protection:
Google Workspace is equipped with advanced threat protection features that act as a robust defense against various cyber threats. These features include mechanisms to detect and prevent phishing attacks, malware, and other security risks. By leveraging these tools, organizations can enhance the overall security posture of their digital workspace and protect sensitive information from unauthorized access.
Security Center and Investigation Tool:
The Security Center within Google Workspace serves as a centralized hub for monitoring and managing security settings. It provides administrators with a comprehensive view of security metrics and alerts, enabling them to respond promptly to potential security incidents. The Investigation Tool complements this by facilitating forensic investigations, allowing organizations to understand the nature of security events and take appropriate action.
Continuous Improvement:
Google prioritizes continuous improvement in the realm of security and compliance. This commitment is reflected in regular updates and enhancements to Google Workspace. By staying at the forefront of technological advancements and evolving security threats, Google ensures that organizations using Google Workspace benefit from the latest and most effective security measures in the ever-changing landscape of cloud computing.
Google’s proactive approach to security, coupled with industry certifications, advanced threat protection, robust security tools, and a commitment to continuous improvement, establishes Google Workspace as a secure and trustworthy platform for organizations seeking a reliable and protected digital workspace.
Core Principles of Data Governance in Google Workspace
Data Classification:
- Google Workspace enables organizations to implement robust data classification policies. This involves categorizing data based on its sensitivity, allowing users to label documents and emails with appropriate levels of confidentiality or importance.
- This classification system helps in setting clear guidelines for handling different types of data, ensuring that sensitive information is treated with the necessary precautions.
Access Controls:
- Google Workspace provides advanced access control features, allowing administrators to define and manage user permissions effectively. This ensures that only authorized individuals have access to specific data and applications.
- Following the principle of least privilege is crucial, as it limits access to the minimum necessary for individuals to perform their job functions. This reduces the risk of unauthorized access and data exposure.
Data Loss Prevention (DLP):
- DLP policies are essential for preventing the unauthorized sharing or leakage of sensitive information. Google Workspace includes powerful DLP features that enable organizations to create and enforce rules governing the handling of data.
- These policies can identify and block attempts to share sensitive information outside the organization, helping prevent accidental data breaches and ensuring compliance with data protection regulations.
Audit Trails and Monitoring:
- Google Workspace provides comprehensive audit trail capabilities, allowing organizations to maintain detailed logs of user activities. This includes tracking changes to documents, email access, and other user actions.
- Monitoring user activity through audit trails is crucial for ensuring compliance with internal policies and external regulations. It also facilitates quick response to any security incidents by providing a clear record of what actions were taken and by whom.
Conclusion
As organizations continue to embrace the collaborative power of Google Workspace, it is essential to prioritize compliance and data governance. This comprehensive guide has explored the intricacies of compliance within Google Workspace, including GDPR, HIPAA, and industry-specific regulations. Additionally, we delved into data governance best practices and highlighted the tools and features provided by Google Workspace to facilitate effective compliance management.
By adopting a proactive approach to compliance and data governance, organizations can not only meet regulatory requirements but also enhance data security, privacy, and overall operational efficiency. As the digital landscape evolves, staying informed about updates to Google Workspace features and industry regulations will be key to maintaining a robust compliance and data governance strategy.
Google Workspace employs encryption, access controls, and secure infrastructure to protect data. Additionally, it offers features like data loss prevention (DLP) to prevent accidental data leaks.
Yes, Google Workspace is designed to be GDPR-compliant, providing tools and features to help organizations meet their obligations under the General Data Protection Regulation.
Google Workspace allows organizations to choose the geographic location where their data is stored, helping them comply with data residency requirements.
Yes, administrators can use audit logs in Google Workspace to track user activity, helping with compliance monitoring and investigations.
Google Vault is an archiving and e-discovery tool that helps organizations retain, search, and export data for compliance purposes, including legal and regulatory requirements.
Yes, administrators can configure data retention policies in Google Workspace to automatically delete or retain data based on organizational requirements and compliance standards.
Google Workspace uses advanced security features, including anti-phishing and anti-malware protections, to secure email communication and meet compliance standards.
Yes, administrators can control access to third-party applications and assess their compliance with security and data protection standards using Google Workspace.
Yes, Google Workspace provides secure collaboration features, such as sharing controls and guest access settings, allowing users to collaborate with external partners while maintaining compliance.
Google Workspace is designed with robust infrastructure and backup mechanisms to ensure data integrity and availability, reducing the risk of data loss.
Yes, administrators have granular control over security settings in Google Workspace, allowing them to customize security configurations to align with organizational compliance requirements.
Yes, Google Vault within Google Workspace supports e-discovery, enabling organizations to search and export data for legal and compliance purposes.
Google Workspace provides tools and resources to assist with data transfer and migration, ensuring a secure and compliant transition to the platform.
Yes, Google Workspace offers APIs and integration capabilities, allowing organizations to integrate with third-party compliance tools and services as needed.
Google Workspace provides features and configurations that cater to the compliance requirements of various regulated industries, such as finance and healthcare.
Yes, Google Workspace supports secure access on mobile devices with features like mobile device management (MDM) and mobile application management (MAM).