Introduction
What is AWS CloudFormation?

AWS CloudFormation is a powerful service provided by Amazon Web Services (AWS) that allows users to define and provision their infrastructure as code. In simpler terms, it enables you to describe your AWS resources and their dependencies in a declarative template, written in either JSON or YAML format. This template acts as a blueprint for your infrastructure, specifying the configuration of various AWS resources such as EC2 instances, S3 buckets, RDS databases, and more. CloudFormation then takes care of provisioning and managing these resources, ensuring that they are created, updated, and deleted in a consistent and predictable manner.
Key Concepts and Terminology
To effectively use AWS CloudFormation, it’s essential to understand its key concepts and terminology. One fundamental concept is the CloudFormation template, which defines the desired state of your infrastructure. Templates consist of resource definitions, parameters, mappings, outputs, and other optional sections. Resources represent the AWS components you want to provision, such as EC2 instances or VPCs. Parameters allow you to customize your templates by providing input values at runtime, while mappings enable you to define conditional values based on input parameters or regions. Outputs provide information about the resources created by the stack, such as their ARNs or IP addresses.
Additionally, CloudFormation stacks are the highest-level containers for organizing and managing related AWS resources. Stacks can be created, updated, and deleted as a single unit, making it easy to manage complex infrastructures.
Benefits of Using CloudFormation
There are several benefits to using AWS CloudFormation for infrastructure provisioning and management. Firstly, CloudFormation allows for infrastructure as code (IaC), which brings the benefits of version control, automation, and repeatability to your infrastructure deployments. By defining your infrastructure in code, you can easily track changes over time, roll back to previous versions if necessary, and replicate environments across different regions or AWS accounts. Furthermore, CloudFormation provides a unified way to manage resources across various AWS services, eliminating the need to manually provision and configure each resource individually. This saves time and reduces the risk of human error.
Additionally, CloudFormation integrates seamlessly with other AWS services, such as AWS Identity and Access Management (IAM) for security, AWS CloudTrail for auditing, and AWS CloudWatch for monitoring, providing a comprehensive solution for managing your AWS infrastructure.
Comparison with Other Infrastructure as Code (IaC) Tools
While AWS CloudFormation is a powerful tool for infrastructure automation, it’s essential to understand how it compares to other IaC tools in the market. One popular alternative is Terraform, an open-source tool developed by HashiCorp. Terraform supports multiple cloud providers, including AWS, Azure, and Google Cloud Platform, allowing for a more agnostic approach to infrastructure management. Unlike CloudFormation, which is AWS-specific, Terraform uses its own domain-specific language (DSL) called HashiCorp Configuration Language (HCL), which some users may find more intuitive or flexible. Additionally, Terraform has a vibrant community and a rich ecosystem of plugins and modules, offering greater extensibility and customization options.
However, CloudFormation has the advantage of tighter integration with AWS services and native support for AWS-specific features and best practices. Ultimately, the choice between CloudFormation and other IaC tools depends on factors such as familiarity with the tooling, specific requirements, and preferences for cloud provider agnosticism versus deep integration with AWS.
Getting Started with CloudFormation Templates
Anatomy of a CloudFormation Template
A CloudFormation template is essentially a text file written in either JSON or YAML format that describes the AWS resources and their configurations needed to deploy an application or infrastructure stack. The template consists of several key components:
- Format Version: Specifies the version of the template format being used.
- Description: Provides a human-readable description of the template’s purpose.
- Parameters: Allows users to input custom values when creating or updating a stack.
- Mappings: Defines a mapping between keys and corresponding values.
- Resources: Defines the AWS resources to be provisioned, such as EC2 instances, S3 buckets, or IAM roles.
- Outputs: Specifies the values that should be returned once the stack is created or updated.
YAML vs. JSON: Choosing the Right Format
CloudFormation templates can be written in either YAML or JSON format. YAML offers a more human-readable and concise syntax, while JSON is stricter and might be preferred in certain environments where interoperability and strict validation are necessary. Both formats have their advantages and disadvantages, so the choice depends on personal preference and project requirements.
Writing Your First Template
In this section, users are guided through the process of writing a simple CloudFormation template. They learn how to define parameters, resources, and outputs based on their application or infrastructure requirements. The tutorial might include examples of creating EC2 instances, setting up security groups, and configuring networking resources.
Deploying a Stack Using the AWS Management Console

Once the template is written, users can deploy it using the AWS Management Console. This involves logging into the AWS console, navigating to the CloudFormation service, and creating a new stack. Users upload their template file, specify any required parameters, and initiate the stack creation process. The console provides visibility into the stack’s status and any events or errors encountered during deployment.
Declarative Resource Provisioning
Resource Types and Properties:
This refers to the different types of resources that can be provisioned, such as virtual machines, databases, networks, etc. Each resource type has its properties, which define its characteristics and behavior.
Parameters and Input Variables: Parameters are values that can be passed to a template during its execution to customize its behavior. Input variables are similar to parameters but are typically defined outside the template and can be used to make the template more flexible and reusable.
Mapping and Conditionals:
Mapping allows you to define a set of key-value pairs to use in your template. It is useful for mapping different values based on conditions or input parameters. Conditionals enable you to control the execution flow of your template based on certain conditions, allowing for more dynamic and flexible provisioning.
Outputs and Exporting Stack Data:
Outputs allow you to define the values that you want to retrieve once the stack (collection of resources) is created or updated. This could be useful for obtaining information such as the IP address of a provisioned server or the endpoint of a database. Exporting stack data enables sharing of resources or information between different stacks or templates.
Intrinsic Functions for Dynamic Templates:
Intrinsic functions are built-in functions provided by the infrastructure as code tool or platform that allow for dynamic and flexible template creation. These functions can perform various tasks such as referencing other resources, performing calculations, generating unique identifiers, and more. They enable the creation of templates that adapt to changing conditions or requirements dynamically.
Declarative resource provisioning involves defining resources and their properties in a structured manner, using parameters and variables for flexibility, employing mappings and conditionals for dynamic behavior, capturing outputs for retrieval of information, and leveraging intrinsic functions for creating dynamic templates. This approach simplifies the management of resources and promotes consistency, scalability, and automation in infrastructure provisioning.
Advanced Template Techniques
Nested Stacks for Modularization:
Nested stacks in AWS CloudFormation allow you to break down complex infrastructure into smaller, more manageable units. This modularization makes it easier to organize, maintain, and update your infrastructure code. With nested stacks, you can create reusable templates for common components or services, such as networking, databases, or application tiers, and then reference them within a parent template. This approach promotes code reuse, simplifies dependency management, and enhances the overall maintainability of your CloudFormation templates.
Custom Resources with AWS Lambda:

Custom resources enable you to extend the capabilities of CloudFormation by incorporating custom logic or integrating with external services that are not natively supported. By leveraging AWS Lambda functions as custom resources, you can execute custom code during the stack creation or update process. This allows you to perform tasks such as provisioning resources in third-party systems, configuring advanced settings, or automating complex workflows. Custom resources offer flexibility and versatility, enabling you to address unique requirements and integrate with a wide range of services beyond what is directly supported by CloudFormation.
StackSets for Multi-Account and Multi-Region Deployments:
StackSets is a feature of AWS CloudFormation that enables centralized management and deployment of stacks across multiple AWS accounts and regions. With StackSets, you can define a template once and then deploy it to multiple accounts and regions simultaneously or sequentially. This simplifies the process of deploying infrastructure consistently across different environments, such as development, testing, and production. StackSets also provide capabilities for automated rollback, drift detection, and stack instance management, making it easier to maintain consistency and compliance across your entire organization.
Using AWS Serverless Application Model (SAM) with CloudFormation:
The AWS Serverless Application Model (SAM) is an extension of AWS CloudFormation that simplifies the deployment and management of serverless applications on AWS. SAM provides a simplified syntax and additional resource types specifically designed for building serverless architectures, such as AWS Lambda functions, API Gateway APIs, and DynamoDB tables.
By leveraging SAM with CloudFormation, you can define serverless applications using high-level constructs, streamline the deployment process, and take advantage of built-in capabilities for handling common serverless patterns, such as event-driven processing and auto-scaling.
CloudFormation Macros for Template Preprocessing:
CloudFormation macros enable you to preprocess templates before they are executed, allowing you to add custom logic, perform transformations, or generate template fragments dynamically. Macros can be used to automate repetitive tasks, enforce best practices, or customize templates based on specific requirements.
For example, you can use macros to generate resource configurations based on input parameters, apply naming conventions, or inject environment-specific settings. By leveraging macros, you can enhance the flexibility, scalability, and reusability of your CloudFormation templates, while also reducing the complexity of template management and maintenance.
Managing Dependencies and Relationships
Understanding Resource Dependencies:
When you’re working with AWS CloudFormation templates, it’s crucial to understand the dependencies between resources. This involves understanding which resources rely on others for proper functioning. For example, a database resource might depend on a VPC (Virtual Private Cloud) or a security group. CloudFormation uses dependency information to determine the order in which resources should be created or deleted to maintain consistency and avoid errors.
Cross-Stack References:
Cross-stack references allow you to access resources defined in other CloudFormation stacks. This feature is particularly useful when you have complex architectures spread across multiple stacks. By referencing resources in other stacks, you can create more modular and reusable templates, promoting better organization and maintainability of your infrastructure.
Using AWS::CloudFormation::Stack Resource:
The AWS::CloudFormation::Stack resource type enables you to create nested stacks within your main CloudFormation template. Nested stacks allow you to break down complex architectures into smaller, more manageable units. Each nested stack has its own template and set of resources, but it can also reference resources from the parent stack, facilitating modularity and reusability.
Importing Existing Resources into CloudFormation:
This feature allows you to import existing AWS resources into a CloudFormation stack. When you’re adopting CloudFormation for existing infrastructure, or when you have resources provisioned outside of CloudFormation, importing them allows you to manage them alongside other resources in your stack. This process involves providing CloudFormation with metadata about the existing resources so it can track and manage them effectively.
Security Best Practices
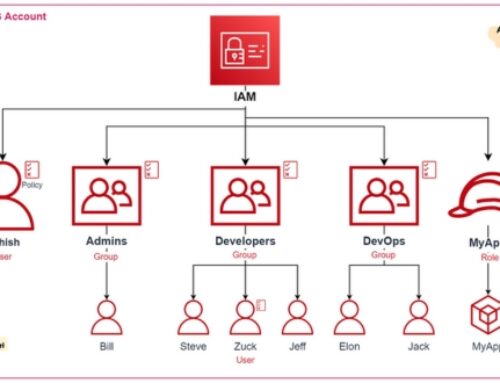
IAM Roles and Policies (Identity and Access Management):
IAM (Identity and Access Management) is a crucial aspect of AWS security that involves managing access to AWS services and resources securely.
IAM Roles define permissions for a set of users, applications, or services. They provide temporary access credentials that can be assumed by entities such as AWS services or users.
IAM Policies are JSON documents that define permissions, specifying what actions are allowed or denied on which AWS resources.
Best practices in this area include:
- Implementing the principle of least privilege, ensuring that entities have only the permissions they need to perform their tasks.
- Regularly reviewing and auditing IAM policies to remove unnecessary permissions and reduce the attack surface.
- Enabling Multi-Factor Authentication (MFA) for IAM users to add an extra layer of security.
Securing Sensitive Data:
This involves protecting sensitive data such as personally identifiable information (PII), financial data, and intellectual property from unauthorized access or disclosure.
AWS offers various services and features to help secure sensitive data, including encryption, access controls, and compliance certifications.
Best practices include:
- Encrypting data both in transit and at rest using AWS Key Management Service (KMS) or other encryption mechanisms.
- Implementing access controls and using IAM policies to restrict access to sensitive data.
- Regularly scanning and monitoring for potential security vulnerabilities or data breaches.
Stack Policies and Permissions Boundaries:
AWS CloudFormation allows you to create and manage AWS infrastructure as code using templates.
Stack Policies enable you to control updates to specific resources within a CloudFormation stack, ensuring that critical resources are not inadvertently modified or deleted.
Permissions Boundaries restrict the maximum permissions that an IAM entity (such as a user or role) can have, providing an additional layer of control over access to AWS resources.
Best practices include:
- Using stack policies to prevent unauthorized modifications to critical resources in CloudFormation stacks.
- Defining and enforcing permissions boundaries to limit the permissions of IAM entities, reducing the risk of privilege escalation attacks.
AWS CloudFormation Guardrails:
CloudFormation Guardrails refer to implementing controls and constraints to ensure that CloudFormation templates adhere to security and compliance requirements.
This may involve using AWS Config rules, AWS Service Catalog, or third-party tools to enforce policies and standards for infrastructure deployments.
Best practices include:
- Implementing automated checks and validations for CloudFormation templates to ensure compliance with security policies and best practices.
- Integrating CloudFormation Guardrails into CI/CD pipelines to enforce security and compliance checks during the deployment process.
Advanced Template Techniques
Nested Stacks for Modularization
Nested stacks allow you to break down complex CloudFormation templates into smaller, more manageable units.
With nested stacks, you can create a hierarchy of templates where one stack can reference another stack as a resource.
This modular approach makes it easier to organize and maintain your infrastructure as code by separating different components or layers of your application.
Custom Resources with AWS Lambda
Custom resources enable you to extend CloudFormation’s capabilities by integrating with AWS Lambda functions.
You can use custom resources to perform tasks that are not directly supported by CloudFormation resources or to integrate with external services during stack creation or updates.
AWS Lambda functions can be triggered by CloudFormation events, allowing you to execute custom logic to provision or configure resources dynamically.
StackSets for Multi-Account and Multi-Region Deployments
StackSets enable you to deploy CloudFormation stacks across multiple AWS accounts and regions simultaneously.
This feature is particularly useful for managing infrastructure deployments in large, distributed environments where you need to maintain consistency across multiple accounts and regions.
StackSets allow you to centrally manage and orchestrate deployments, ensuring that changes are applied consistently across all targeted accounts and regions.
Using AWS Serverless Application Model (SAM) with CloudFormation
AWS SAM is an extension of CloudFormation that simplifies the deployment of serverless applications on AWS.
SAM provides a shorthand syntax for defining serverless resources such as AWS Lambda functions, API Gateway APIs, and DynamoDB tables.
By using SAM with CloudFormation, you can leverage the benefits of both services to define and deploy complex serverless applications with ease, while still having the flexibility and power of CloudFormation for managing other AWS resources.
CloudFormation Macros for Template Preprocessing
CloudFormation macros allow you to perform template preprocessing to automate repetitive tasks or customize the behavior of your templates.
Macros are essentially AWS Lambda functions that can modify CloudFormation templates before they are processed.
You can use macros to implement custom logic, define reusable patterns, or apply transformations to your templates, making them more flexible and easier to maintain.
Testing and Validation
Unit Testing CloudFormation Templates
Unit testing CloudFormation templates involves testing individual components or resources within the template in isolation. This ensures that each resource is configured correctly and behaves as expected. Unit tests for CloudFormation templates can be performed using tools like AWS CloudFormation Linter or cfn-lint, which check the syntax and structure of the template against best practices and AWS service specifications. These tests typically verify things like resource properties, dependencies, and template parameters.
Integration Testing with AWS CodePipeline
Integration testing with AWS CodePipeline involves testing the interaction between different components of your application deployment pipeline. AWS CodePipeline is a continuous integration and delivery service that automates the build, test, and deployment phases of your release process. Integration testing in this context ensures that changes introduced in one phase of the pipeline do not negatively impact subsequent phases. For example, it verifies that code changes integrated into the build phase do not break the deployment phase. This can involve running end-to-end tests, API tests, or other types of integration tests.
Continuous Deployment Pipelines with AWS CloudFormation
Continuous deployment pipelines with AWS CloudFormation involve automating the deployment of infrastructure changes using CloudFormation templates. AWS CloudFormation allows you to define your infrastructure as code, making it easier to manage and deploy resources consistently across environments. Continuous deployment pipelines using CloudFormation typically involve defining stages and actions in AWS CodePipeline to trigger the creation or update of CloudFormation stacks. This ensures that infrastructure changes are deployed automatically whenever there’s a new version of your application code.
Third-Party Tools and Utilities for Validation
There are several third-party tools and utilities available for validating CloudFormation templates and ensuring best practices.
These tools complement the built-in capabilities of AWS CloudFormation and provide additional checks for security, compliance, and performance. Some popular third-party tools include Troposphere, which allows you to define CloudFormation templates using Python code; StackMaster, which provides a command-line interface for managing CloudFormation stacks; and Former2, which generates CloudFormation templates from existing AWS resources. These tools can help improve the efficiency and reliability of your infrastructure deployment process by automating validation and enforcing best practices.
Testing and validation play crucial roles in ensuring the reliability, security, and efficiency of infrastructure deployment processes using AWS CloudFormation and related services like AWS CodePipeline. By performing unit testing, integration testing, and leveraging third-party tools for validation, you can mitigate risks, detect issues early, and maintain the quality of your infrastructure-as-code deployments.
Optimization and Cost Management
Right-Sizing Resources:
Right-sizing resources refers to optimizing the allocation of resources in a cloud environment to match the workload requirements. This involves ensuring that you have the appropriate type and size of resources (such as virtual machines, storage, or databases) to meet your application’s performance needs without overspending on unnecessary capacity. Right-sizing often involves analyzing resource utilization metrics, such as CPU and memory usage, to identify opportunities for downsizing or upsizing instances to achieve a better balance between performance and cost.
Using AWS Trusted Advisor for Cost Optimization:
AWS Trusted Advisor is a tool provided by Amazon Web Services (AWS) that offers recommendations to help optimize your AWS infrastructure for cost, performance, security, and fault tolerance. In the context of cost optimization, Trusted Advisor analyzes your AWS usage and provides suggestions for reducing costs by identifying unused or underutilized resources, highlighting opportunities to leverage reserved instances or spot instances, and recommending best practices for cost-effective architecture design.
CloudFormation Drift Detection:
AWS CloudFormation is a service that allows you to provision and manage AWS infrastructure as code using templates. CloudFormation drift detection helps you identify any divergence between the actual configuration of deployed resources and the desired state specified in your CloudFormation templates. This is important for cost management because it ensures that your resources are provisioned according to the intended configuration, helping to prevent unnecessary spending on resources that may have deviated from the desired state over time.
Resource Tagging and Cost Allocation:
Resource tagging involves assigning custom metadata tags to your AWS resources to categorize and organize them for cost allocation and management purposes. By tagging resources with attributes such as department, project, environment, or owner, you can gain visibility into resource usage patterns and allocate costs more accurately to different cost centers or stakeholders. This enables you to track and analyze spending at a granular level, optimize resource utilization, and enforce cost accountability within your organization.
Conclusion
As organizations continue to embrace cloud-native architectures and infrastructure automation, mastering AWS CloudFormation is essential for developers, DevOps engineers, and cloud architects alike. By leveraging the power of Infrastructure as Code, teams can achieve greater agility, scalability, and operational efficiency in their AWS environments.
CloudFormation templates are JSON or YAML formatted files that describe the AWS resources you want to provision and their configurations.
You can create CloudFormation templates using a text editor or CloudFormation Designer, a visual tool provided by AWS.
CloudFormation allows for infrastructure as code (IaC), enabling automation, version control, and consistency in resource provisioning. It also simplifies resource management and updates.
CloudFormation supports provisioning various AWS resources such as EC2 instances, S3 buckets, RDS databases, IAM roles, and more.
You can reference resources using their logical names defined within the template.