Understanding AWS Virtual Private Cloud (VPC)
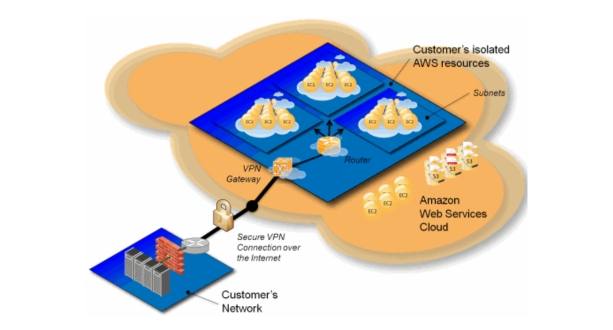
What is a VPC?
A Virtual Private Cloud (VPC) is a virtual network dedicated to your AWS account. It provides you with control over a virtual networking environment, including selection of your IP address range, creation of subnets, and configuration of route tables and network gateways.
Why use a VPC?
Using a VPC allows you to logically isolate resources within the AWS cloud, providing an additional layer of security and control. It enables you to extend your on-premises network infrastructure into the cloud and connect securely to resources and services within your VPC.
Key concepts:
- Subnets: Subnets are segments of the VPC’s IP address range where you can place groups of resources. They allow you to organize and manage your resources efficiently.
- Route Tables: Route tables determine where network traffic is directed within the VPC. They specify the rules for routing traffic between subnets, internet gateways, NAT gateways, and other network devices.
- Internet Gateways: Internet gateways allow resources within your VPC to access the internet and enable internet-initiated traffic to reach your VPC resources.
- NAT Gateways: Network Address Translation (NAT) gateways allow private subnet resources to initiate outbound traffic to the internet while preventing inbound traffic from reaching them directly.
- Security Groups: Security groups act as virtual firewalls for instances within the VPC. They control inbound and outbound traffic at the instance level by defining rules.
- Network Access Control Lists (NACLs): NACLs are stateless firewalls that control traffic at the subnet level. They allow you to create rules that govern both inbound and outbound traffic.
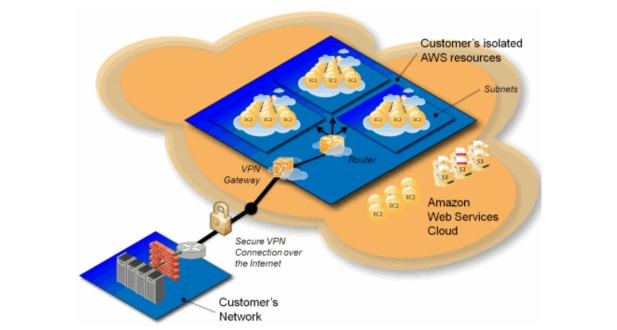
- VPN Connections: VPN connections enable secure communication between your on-premises network and your VPC using encrypted tunnels over the internet.
- VPC Peering: VPC peering allows you to connect multiple VPCs together, enabling communication between them as if they were part of the same network.
Benefits of using VPCs in AWS:

- Security: VPCs offer a secure environment by allowing you to define and enforce security policies using security groups and NACLs.
- Customization: VPCs provide flexibility in designing your network infrastructure, allowing you to configure IP address ranges, subnets, and routing tables according to your requirements.
- Scalability: VPCs can scale with your infrastructure needs, allowing you to add or remove resources easily without disrupting your existing network configuration.
- Connectivity: VPCs enable seamless connectivity between on-premises resources and AWS cloud resources through VPN connections or direct connect options.
- Cost Optimization: By leveraging VPCs, you can optimize costs by efficiently managing resources and controlling data transfer costs between regions and availability zones.
Planning Your VPC Architecture
When planning your VPC (Virtual Private Cloud) architecture, there are several key factors to consider to ensure it meets the requirements of your applications and business needs.
- Scalability: A well-designed VPC should be able to scale seamlessly as your application grows. This involves planning for increased traffic, resource demand, and potential expansion into new regions. Utilizing auto-scaling groups, load balancers, and appropriately sized instances can help ensure scalability
- Security: Security is paramount in any VPC architecture. Implementing robust security measures such as network access control lists (NACLs), security groups, encryption, and network traffic monitoring are essential to protect your infrastructure from unauthorized access, data breaches, and other security threats.
- Availability: High availability ensures that your application remains accessible and operational even in the face of failures or disruptions. Leveraging multiple availability zones within your VPC helps distribute your resources across different physical locations, reducing the risk of downtime due to infrastructure failures.
- Compliance: Depending on your industry and geographic location, you may need to adhere to various compliance standards and regulations (such as GDPR, HIPAA, PCI DSS, etc.). Ensuring your VPC architecture complies with these requirements is crucial to avoid legal and regulatory issues.
Best practices for VPC design include:
- Using multiple availability zones: Distributing your resources across multiple availability zones increases fault tolerance and enhances the overall availability of your application. It ensures that if one availability zone goes down, your application can still function without interruption.
- Segregating resources into different subnets: Segmentation of resources into different subnets based on their function or security requirements allows for better control and isolation. For example, you might have separate subnets for web servers, application servers, and databases, each with its own access controls and routing policies.
- Implementing least privilege access controls: Following the principle of least privilege ensures that each component of your VPC only has the permissions necessary to perform its intended function. This minimizes the risk of unauthorized access and reduces the potential impact of security breaches.
Case studies:
- VPC architectures for web applications: A VPC architecture for a web application might include public subnets for web servers, private subnets for application servers, and a database subnet. Load balancers can distribute traffic across multiple web servers for scalability, while security groups and NACLs enforce access controls.
- VPC architectures for databases: For database-heavy applications, you might design a VPC architecture with dedicated subnets for database instances, separate from the application servers. Encryption, access controls, and backup strategies are crucial considerations for securing and managing database resources within the VPC.
- VPC architectures for microservices: Microservices architectures often involve multiple interconnected services running in containers or serverless environments. In a VPC architecture for microservices, you might use container orchestration platforms like Kubernetes or AWS ECS to manage and scale individual services within the VPC, with appropriate network policies and security measures in place to control communication between services.
Setting Up Your AWS VPC

Setting up an AWS Virtual Private Cloud (VPC) involves several steps to create a virtual network environment in the AWS cloud. Below is a more detailed description of each step mentioned in the provided list:
Creating a VPC using the AWS Management Console:
- Access the AWS Management Console and navigate to the VPC dashboard.
- Click on “Create VPC” and provide details such as VPC name, IPv4 CIDR block, and optionally IPv6 CIDR block.
- You can choose whether to enable DNS hostnames and DNS resolution for the VPC.
Configuring subnets: public, private, and isolated subnets:
- After creating the VPC, you can create subnets within it.
- Subnets can be classified into three types: public, private, and isolated.
- Public subnets have a route to the internet gateway, allowing instances within them to communicate directly with the internet.
- Private subnets do not have a direct route to the internet and are typically used for backend services that shouldn’t be directly accessible from the internet.
- Isolated subnets are completely private and have no internet access, often used for databases or other sensitive resources.
Creating and attaching internet and NAT gateways:
- An internet gateway (IGW) allows instances within public subnets to communicate with the internet.
- A NAT gateway (or NAT instance) allows instances within private subnets to initiate outbound traffic to the internet while preventing inbound traffic from reaching them.
Configuring route tables to control traffic flow:
- Each subnet is associated with a route table that controls the traffic flow.
- Route tables define the routes for network traffic, including local routes within the VPC and routes to internet gateways, NAT gateways, VPN connections, etc.
- Ensure that the route tables for public subnets have routes to the internet gateway, while private subnets have routes to the NAT gateway for internet access.
Assigning Elastic IP addresses:
- Elastic IP addresses (EIPs) are static IPv4 addresses that can be associated with instances or other AWS resources.
- You can allocate and associate EIPs with instances in your VPC to ensure they retain the same public IP address even if the instance is stopped and restarted.
Configuring security groups and NACLs:
- Security groups act as virtual firewalls for your instances, controlling inbound and outbound traffic based on rules that you define.
- Network Access Control Lists (NACLs) are an additional layer of security that operate at the subnet level, controlling traffic in and out of subnets based on rules you define.
Setting up VPN connections for secure access:
- VPN connections allow you to establish encrypted connections between your on-premises network and your AWS VPC.
- You can set up VPN connections using AWS Virtual Private Gateway and Customer Gateway.
Troubleshooting common setup issues:
- Troubleshooting may involve checking configuration settings, reviewing logs, and ensuring that all necessary resources are properly configured and connected.
- Common issues may include misconfigured route tables, security group rules blocking traffic, or issues with internet or NAT gateways.
Managing and Monitoring Your VPC
Managing and monitoring your Virtual Private Cloud (VPC) in AWS involves several key components and practices to ensure the security, performance, and efficiency of your network infrastructure.
- CloudWatch: AWS CloudWatch is a monitoring and observability service that provides you with data and actionable insights to monitor your AWS resources, including your VPC. You can use CloudWatch to collect and track metrics, set alarms, and visualize logs. In the context of VPC management, you can monitor network traffic, performance metrics, and resource utilization to ensure optimal performance and identify any issues or anomalies.
- VPC Flow Logs: VPC Flow Logs is a feature that enables you to capture information about the IP traffic going to and from network interfaces in your VPC. This information can include details such as source and destination IP addresses, ports, protocols, and packet counts. By enabling VPC Flow Logs, you can gain visibility into network traffic patterns, troubleshoot connectivity issues, and enhance security by detecting and responding to suspicious activity.
- AWS Config: AWS Config provides you with a detailed inventory of your AWS resources and configuration history, allowing you to assess, audit, and evaluate the configuration changes to your VPC over time. With AWS Config, you can enforce compliance policies, track resource relationships, and identify configuration drift to maintain the desired state of your VPC infrastructure.
- Scaling Resources: As your workload demands change, you may need to scale your VPC resources to accommodate increased traffic or workloads. This could involve adding more subnets, adjusting the size of your instances, or increasing the capacity of your network infrastructure to meet growing demands efficiently.
- Modifying Subnet Configurations: Subnet configurations define the network boundaries within your VPC and determine how resources are connected and accessed. Modifying subnet configurations may involve adjusting CIDR blocks, adding or removing subnets, or configuring route tables to optimize network routing and improve connectivity.
- Updating Security Groups and NACLs: Security Groups and Network Access Control Lists (NACLs) are essential for controlling inbound and outbound traffic to and from your VPC resources. Regularly reviewing and updating security group rules and NACL configurations is critical to maintaining a secure network environment, preventing unauthorized access, and complying with security policies and regulations.
- VPC Tagging: Tagging resources with metadata allows you to categorize and organize your VPC resources for better resource management, cost allocation, and access control. By implementing consistent tagging strategies, you can easily identify, track, and manage your VPC resources across various dimensions, such as environment, application, or owner.
- Automating VPC Management Tasks: AWS offers services like AWS Lambda and AWS Systems Manager that enable you to automate repetitive VPC management tasks and workflows. By leveraging serverless computing and automation capabilities, you can streamline provisioning, configuration, and maintenance processes, reduce manual overhead, and improve operational efficiency.
Advanced VPC Configurations
VPC Peering:
VPC peering allows you to connect multiple Virtual Private Clouds (VPCs) within the same AWS region, enabling them to communicate with each other using private IP addresses. This facilitates the creation of a virtual network that spans multiple VPCs while keeping the traffic within the AWS network. This can be useful for scenarios where you have different applications or environments deployed in separate VPCs but need them to communicate securely.
VPC Endpoints:
VPC endpoints provide a secure and private connection between your VPC and AWS services without the need for internet exposure. This is achieved by creating an interface endpoint or a gateway endpoint within your VPC. Interface endpoints are used for services such as Amazon S3 or DynamoDB, while gateway endpoints are used for services like Amazon SNS or SQS. By utilizing VPC endpoints, you can enhance security by keeping traffic within the AWS network and avoid exposing your resources to the public internet.
VPC Endpoint Services:
VPC endpoint services allow you to privately expose your own services or applications to other VPCs within the same AWS account or across different accounts. This enables secure communication between VPCs without traversing the public internet. It’s particularly useful when you have SaaS (Software as a Service) applications deployed in your VPC and want to provide access to them from other VPCs in a secure manner.
AWS Transit Gateway:
AWS Transit Gateway simplifies network connectivity by acting as a centralized hub that connects multiple VPCs, on-premises networks, and VPN connections. It enables you to scale your network infrastructure easily and efficiently manage communication between various resources spread across different VPCs. With Transit Gateway, you can consolidate network routing and security policies, reducing complexity and administrative overhead.
Integration with other AWS Services:
VPC can be integrated with various other AWS services to enhance network connectivity and management. For instance, AWS Direct Connect allows you to establish a dedicated network connection between your on-premises data center and AWS, providing consistent and reliable network performance. AWS CloudFormation enables you to automate the provisioning and management of your VPC resources, making it easier to maintain consistency and scalability across your infrastructure.
Security Best Practices for VPCs
Implementing encryption for data in transit and at rest:
Encryption is vital for protecting sensitive data from unauthorized access. In a VPC, data should be encrypted both when it’s moving between different components within the VPC (data in transit) and when it’s stored in databases or on disk (data at rest). This typically involves using protocols like SSL/TLS for data in transit and encrypting data using encryption algorithms such as AES or RSA when it’s at rest. Services like AWS Key Management Service (KMS) can be used for managing encryption keys.
Applying IAM policies to control access to VPC resources:
Identity and Access Management (IAM) policies define who can access which resources within the VPC and what actions they can perform on those resources. By properly configuring IAM policies, you can enforce the principle of least privilege, ensuring that users and services have only the permissions they need to perform their intended tasks. This helps minimize the risk of unauthorized access or accidental data exposure.
Enforcing network segmentation using security groups and NACLs:
Network segmentation involves dividing the VPC into smaller, isolated segments to limit the impact of security breaches and control the flow of traffic between different parts of the network. Security groups and Network Access Control Lists (NACLs) are two key mechanisms for implementing network segmentation in a VPC. Security groups act as virtual firewalls at the instance level, controlling inbound and outbound traffic based on rules, while NACLs operate at the subnet level, providing an additional layer of control over traffic flow.
Implementing DDoS protection and intrusion detection measures:
Distributed Denial of Service (DDoS) attacks can overwhelm a VPC with a flood of traffic, disrupting services and causing downtime. Implementing DDoS protection measures such as AWS Shield can help mitigate the impact of these attacks by automatically detecting and mitigating malicious traffic. Additionally, deploying intrusion detection systems (IDS) or intrusion prevention systems (IPS) within the VPC can help identify and respond to unauthorized access attempts or malicious activities in real-time.
Regularly auditing VPC configurations for compliance with security standards:
VPC configurations should be regularly audited to ensure they adhere to security best practices and compliance requirements. This involves conducting comprehensive security assessments, reviewing access controls, encryption settings, network configurations, and other security-related parameters to identify any misconfigurations or vulnerabilities. Automated tools and services, along with manual reviews by security experts, can be used to perform these audits and ensure ongoing compliance with security standards.
Optimizing Performance and Cost
Optimizing Network Performance:
- Choosing the Right Instance Types: Different cloud providers offer various instance types optimized for specific workloads. For instance, some instances are optimized for compute-heavy tasks, while others are better suited for memory-intensive applications. Selecting the appropriate instance type can significantly enhance network performance.
- Configuring Elastic Network Interfaces (ENIs): ENIs provide networking capabilities to instances in the cloud. Properly configuring ENIs involves setting up parameters such as bandwidth, security groups, and subnet associations to ensure optimal performance and security.
- Optimizing Routing: Efficient routing of network traffic is crucial for minimizing latency and maximizing throughput. This involves configuring routing tables, using content delivery networks (CDNs) for caching frequently accessed content, and employing techniques like anycast routing for distributing traffic to the nearest available server.
Cost Optimization Strategies:
- Rightsizing Resources: Rightsizing involves matching the resources (e.g., CPU, memory, storage) of instances to the actual requirements of the workload. Overprovisioning resources can lead to unnecessary costs, while underprovisioning can result in performance issues. Continuously monitoring resource utilization and adjusting accordingly can help optimize costs.
- Leveraging Spot Instances: Spot instances are unused compute capacity offered at a significantly lower price compared to on-demand instances. By utilizing spot instances for non-critical or fault-tolerant workloads, organizations can achieve substantial cost savings. However, it’s essential to have mechanisms in place to handle instance termination with minimal disruption.
- Using Reserved Instances for Predictable Workloads: Reserved instances offer a discounted pricing model in exchange for a commitment to a specific instance type, region, and term length. For workloads with predictable usage patterns, such as steady-state applications, purchasing reserved instances can provide significant cost savings compared to on-demand pricing.
- Implementing Cost Allocation Tags: Cost allocation tags allow organizations to categorize resources based on various attributes (e.g., department, project, environment). By applying tags consistently across resources, it becomes easier to track and allocate costs accurately, enabling better cost management and optimization.
Conclusion
In conclusion, AWS Virtual Private Cloud (VPC) is a powerful tool for creating secure and isolated network environments within the AWS cloud. By following best practices for VPC design, configuration, and management, businesses can ensure the security, scalability, and reliability of their cloud infrastructure. With the comprehensive guide provided here, you should now have a solid understanding of how to set up and manage a VPC in AWS effectively.
AWS VPC allows you to have complete control over your virtual networking environment, including selection of IP address range, creation of subnets, configuration of route tables, and network gateways. It enables you to create a secure and private environment in the AWS Cloud.
You can create a VPC using the AWS Management Console, AWS Command Line Interface (CLI), or AWS SDKs. Simply navigate to the VPC dashboard in the AWS Management Console and follow the prompts to create a new VPC.
A subnet is a range of IP addresses in your VPC. Subnets allow you to partition your VPC into smaller networks for organizational or security purposes. Each subnet must reside entirely within one Availability Zone.
VPC peering allows you to connect one VPC with another VPC through a direct network route using private IP addresses. This enables instances in different VPCs to communicate with each other as if they are within the same network.
You can secure your AWS VPC using various methods including Network Access Control Lists (NACLs), Security Groups, and by configuring routing tables. Additionally, you can use AWS Identity and Access Management (IAM) to control access to AWS resources.