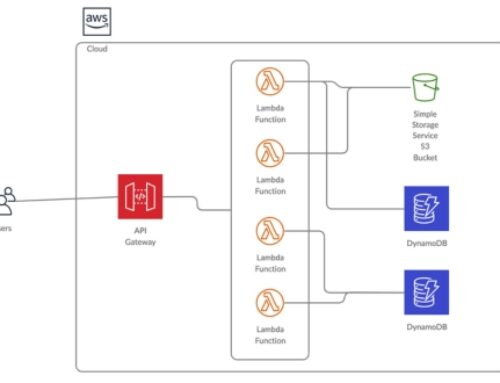
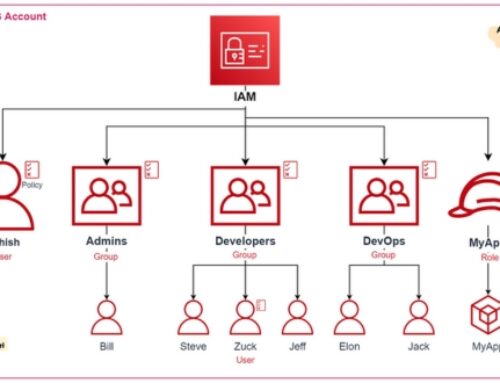
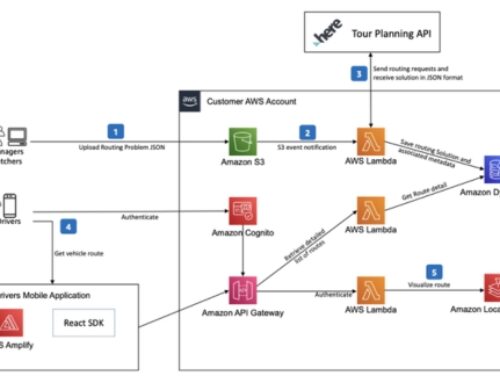
Introduction to AWS Security Assessment
In the dynamic landscape of cloud computing, securing digital assets is paramount, and Amazon Web Services (AWS) stands as a global leader in providing a secure cloud environment. This section delves into the foundational aspects of AWS security, emphasizing the crucial role of regular security assessments in mitigating evolving cyber threats.
Overview of AWS Security
- Navigating the Digital Fortress:
AWS, as a cloud services provider, prioritizes the security of its users’ data and applications. The AWS shared responsibility model highlights the collaborative effort between AWS and its users, emphasizing a division of responsibilities for securing the cloud infrastructure.
- Multi-Layered Security:
AWS implements a multi-layered security approach, encompassing physical security, network security, data encryption, and access controls. This holistic strategy ensures that every facet of the AWS environment is fortified against potential threats.
- Robust Identity and Access Management (IAM):
IAM is at the core of AWS security, providing a granular control mechanism for user access to resources. Through IAM, organizations can define and manage permissions, enhancing overall data confidentiality and integrity.
Importance of Regular Security Assessments
- The Evolving Threat Landscape:
Cyber threats are dynamic and ever-evolving, making regular security assessments indispensable. With the rapid pace of technological advancements, staying ahead of potential vulnerabilities and emerging threats is a continuous endeavor.
- Proactive Threat Mitigation:
Regular security assessments serve as a proactive measure to identify, analyze, and mitigate potential vulnerabilities before they can be exploited. This approach minimizes the risk of security breaches and strengthens the overall resilience of the AWS environment.
- Compliance and Regulatory Requirements:
In an era of stringent data protection regulations and industry-specific compliance standards, regular security assessments are instrumental in ensuring that AWS deployments adhere to legal and regulatory requirements. This is crucial for maintaining trust with users and stakeholders.
AWS Security, Assessment, Cybersecurity, Threat Mitigation

- Defending the Digital Realm:
AWS security is synonymous with defending the digital realm, encompassing a spectrum of services and features designed to create a robust shield against cyber threats. Understanding the intricacies of AWS security sets the stage for organizations to harness the full potential of cloud computing without compromising on data integrity or confidentiality.
- Continuous Vigilance:
Regular security assessments form the bedrock of continuous vigilance, enabling organizations to adapt their security postures in response to the evolving threat landscape. By embracing the principles of AWS security and committing to ongoing assessments, businesses can navigate the cloud with confidence, knowing that their digital assets are fortified against contemporary and future challenges.
As we embark on this exploration of AWS security assessment, the subsequent sections will delve into specific components, strategies, and best practices that collectively contribute to a comprehensive and resilient security framework within the AWS ecosystem.
Key Components of AWS Security

Identity and Access Management (IAM)
IAM Best Practices
Identity and Access Management (IAM) serves as the cornerstone of AWS security, offering a robust framework for managing user identities and controlling access to resources. Employing IAM best practices is crucial to fortify the digital perimeter.
- Principle of Least Privilege:
IAM best practices advocate for the implementation of the principle of least privilege, ensuring that users and applications only have access to the resources necessary for their specific roles. This minimizes the attack surface and mitigates potential risks.
- Multi-Factor Authentication (MFA):
Enforcing multi-factor authentication adds an extra layer of security by requiring users to verify their identity through multiple means. This significantly enhances the resilience of access controls, particularly for critical systems and sensitive data.
- Regular Auditing and Monitoring:
Continuous auditing and monitoring of IAM configurations are imperative to identify and rectify potential security gaps. Regular reviews of user permissions and access logs help organizations stay proactive in maintaining a secure IAM environment.
User Access Reviews
Conducting regular user access reviews is a fundamental aspect of IAM governance. This involves systematically evaluating and validating user permissions to ensure alignment with current job roles and responsibilities.
- Periodic Access Reviews:
Establishing a routine schedule for access reviews enables organizations to promptly identify and address any discrepancies in user permissions. This proactive approach aligns with the principle of continuous security improvement.
- Automated Access Review Tools
Leveraging automated tools for access reviews streamlines the process, making it more efficient and less prone to human error. AWS offers solutions that can automatically analyze user permissions and generate comprehensive access reports.
Network Security
VPC Configuration
Amazon Virtual Private Cloud (VPC) forms the foundation of network security in AWS, allowing users to create isolated and secure environments. Proper VPC configuration is essential for establishing a robust network architecture.
- Subnet Design and Segmentation:
Effective VPC configuration involves careful subnet design and segmentation to isolate different components of the infrastructure. This prevents lateral movement of threats and enhances overall network resilience.
- Network ACLs and Security Groups:
Network Access Control Lists (NACLs) and Security Groups provide additional layers of defense within the VPC. NACLs operate at the subnet level, controlling inbound and outbound traffic, while Security Groups act at the instance level, specifying allowable traffic to and from instances.
Security Groups and NACLs
- Fine-Grained Control with Security Groups:
Security Groups enable fine-grained control over inbound and outbound traffic for instances. By defining rules within Security Groups, organizations can restrict access to specific ports and protocols, reducing the risk of unauthorized access.
- Layered Defense with NACLs:
Network ACLs operate at the network level, offering a layered defense strategy. Configuring NACLs involves defining rules that govern traffic flow between subnets, providing an additional barrier against malicious activity.
Data Encryption
Encryption at Rest and in Transit
Securing data is a pivotal aspect of AWS security, and encryption plays a pivotal role in safeguarding information both at rest and in transit.
- Encryption at Rest:
Implementing encryption at rest involves encrypting data stored in AWS services such as Amazon S3, EBS volumes, and RDS databases. AWS Key Management Service (KMS) facilitates the management of encryption keys, ensuring a robust and centralized approach to data protection.
- Encryption in Transit:
Encrypting data in transit involves securing the communication channels between different components of the AWS infrastructure. Utilizing protocols like HTTPS and SSL/TLS ensures that data remains confidential during transmission.
Key Management
- Centralized Key Management with AWS KMS:
AWS Key Management Service (KMS) provides a centralized platform for managing encryption keys. This service simplifies key creation, rotation, and auditing, ensuring a secure and compliant key management process.
- Integration with Other AWS Services:
AWS KMS seamlessly integrates with various AWS services, allowing organizations to extend encryption capabilities across their entire cloud environment. This includes integration with S3, RDS, and Lambda, among others.
In this exploration of the key components of AWS security, we’ve unveiled the critical role played by IAM, network security, and data encryption in creating a resilient and well-protected cloud environment. The subsequent sections will further unravel advanced strategies, best practices, and real-world applications that collectively contribute to a comprehensive security framework within AWS.
Threat Detection and Incident Response
Implementing CloudWatch for Monitoring
CloudWatch Alarms and Events
Implementing robust threat detection mechanisms is critical in maintaining the security posture of an AWS environment. Amazon CloudWatch serves as a comprehensive monitoring solution, offering a range of features to detect and respond to potential threats.
- CloudWatch Alarms:
CloudWatch Alarms provide a proactive approach to threat detection by allowing users to set thresholds for various metrics. When these thresholds are breached, CloudWatch Alarms trigger notifications, enabling timely response to anomalies or potential security incidents.
- Events and Event Rules:
CloudWatch Events allow users to define and respond to changes in the AWS environment. By creating event rules, organizations can automate responses to specific events, such as changes in resource configurations, API calls, or the detection of unauthorized activities.
Custom Metrics
- Tailored Monitoring with Custom Metrics:
While CloudWatch provides a plethora of predefined metrics, organizations may have unique requirements that necessitate custom metrics. Custom metrics enable the monitoring of specific aspects of an application or infrastructure, offering a tailored approach to threat detection.
- Integration with AWS Services:
CloudWatch seamlessly integrates with various AWS services, allowing organizations to monitor and create custom metrics for resources like EC2 instances, RDS databases, Lambda functions, and more. This comprehensive coverage enhances visibility into the entire AWS environment.
Incident Response Planning
Creating an Incident Response Team
- Building a Skilled Incident Response Team:
An effective incident response plan begins with the formation of a skilled and dedicated Incident Response Team (IRT). This team comprises individuals with expertise in cybersecurity, forensics, and AWS services, ensuring a holistic approach to incident response.
- Roles and Responsibilities:
Defining clear roles and responsibilities within the Incident Response Team is paramount. This includes roles such as Incident Coordinator, Forensic Analyst, Communications Lead, and Legal Advisor. Each role plays a specific part in the incident response process.
Tabletop Exercises
- Simulating Real-World Scenarios:
Tabletop exercises are simulated scenarios that allow the Incident Response Team to practice and refine their response procedures. These exercises involve discussing and simulating potential security incidents to ensure preparedness and coordination among team members.
- Identifying Weaknesses and Improving Response Plans:
Through tabletop exercises, organizations can identify weaknesses in their incident response plans and address them proactively. This iterative process contributes to continuous improvement, ensuring that the team is well-prepared to handle a variety of security incidents.
Conclusion
In conclusion, the implementation of threat detection and incident response measures is foundational to a robust AWS security strategy. Leveraging CloudWatch for continuous monitoring, utilizing custom metrics for tailored insights, and establishing a well-organized Incident Response Team are key components in safeguarding an AWS environment. Tabletop exercises further enhance the preparedness of the response team, ensuring a coordinated and effective approach in the face of security incidents.
The subsequent sections will explore advanced aspects of AWS security, including penetration testing, security automation, and compliance measures. Each component contributes to a comprehensive security posture that is adaptive, proactive, and resilient against evolving cyber threats.
Penetration Testing in AWS Environment
Understanding Penetration Testing
Authorized vs. Unauthorized Testing
Penetration testing, also known as ethical hacking, is a crucial component of proactive security measures to identify vulnerabilities within an AWS environment. Understanding the distinction between authorized and unauthorized testing is fundamental to conducting effective penetration tests.
- Authorized Penetration Testing:
Authorized penetration testing involves deliberate attempts to assess the security of an AWS infrastructure with the explicit permission of the organization. This proactive approach allows businesses to identify and rectify potential vulnerabilities before malicious actors can exploit them.
- Unauthorized Penetration Testing:
Unauthorized penetration testing, on the other hand, refers to attempts to assess security without proper authorization. This can lead to legal consequences and potential disruptions to services. It is imperative for organizations to strictly adhere to authorized testing to ensure the legality and effectiveness of the process.
AWS Guidelines for Penetration Testing
AWS-Specific Guidelines:
AWS provides specific guidelines and recommendations for conducting penetration testing within its environment. These guidelines aim to ensure the security and stability of AWS services while allowing organizations to assess their own security posture.
- Permission Request Process:
Organizations planning penetration tests in an AWS environment must follow a permission request process. This involves submitting a request to AWS, outlining the scope, methods, and expected impact of the testing. AWS reviews the request and provides explicit authorization.
Selecting a Qualified Penetration Testing Provider
Certifications and Expertise
Choosing a qualified penetration testing provider is crucial for obtaining accurate and actionable insights into the security of an AWS environment. Several factors should be considered when selecting a provider, including certifications and expertise.
- Certifications:
A reputable penetration testing provider should possess relevant certifications, such as Certified Ethical Hacker (CEH), Offensive Security Certified Professional (OSCP), or AWS Certified Security Specialty. These certifications demonstrate the provider’s proficiency in ethical hacking and security assessments.
- Expertise in AWS Environment:
Expertise in AWS-specific environments is a critical factor. The penetration testing team should have a deep understanding of AWS services, configurations, and potential vulnerabilities unique to the cloud environment. This expertise ensures comprehensive testing tailored to the AWS infrastructure.
Compliance with AWS Policies
Adherence to AWS Policies:
A qualified penetration testing provider must comply with AWS policies and guidelines throughout the testing process. This includes following the AWS Acceptable Use Policy and adhering to the terms outlined in the AWS Customer Agreement. Compliance ensures a lawful and ethical testing process.
- Data Handling and Privacy:
The provider should have robust policies for handling sensitive data discovered during penetration testing. Clear guidelines on data privacy and confidentiality are essential to prevent any unauthorized disclosure or misuse of information.
Conclusion
In conclusion, penetration testing is a vital practice for proactively identifying and addressing vulnerabilities within an AWS environment. Understanding the nuances between authorized and unauthorized testing, following AWS guidelines, and selecting a qualified provider with the right certifications and expertise are essential steps in ensuring a comprehensive and lawful penetration testing process.
The subsequent sections will delve into advanced aspects of AWS security, including security automation, compliance measures, and emerging trends. Each component contributes to a holistic security strategy, reinforcing the resilience of AWS environments against evolving cyber threats.
Security Automation and DevSecOps
Integrating Security into DevOps Processes
CI/CD Pipeline Security
Integrating security into DevOps processes is a fundamental practice known as DevSecOps. This approach emphasizes the importance of embedding security measures throughout the entire software development lifecycle. In the context of AWS, DevSecOps involves securing Continuous Integration/Continuous Deployment (CI/CD) pipelines.
- Secure CI/CD Pipelines:
Securing CI/CD pipelines ensures that security measures are seamlessly integrated into the software delivery process. This involves implementing automated security checks at various stages of the pipeline, such as code commits, build processes, and deployment stages. Automated testing tools can scan code for vulnerabilities, ensuring that only secure code is deployed.
Infrastructure as Code (IaC) Security Scanning
- Ensuring IaC Security:
Infrastructure as Code (IaC) is a key element of modern cloud environments. DevSecOps practices include incorporating security scanning into the IaC development process. Automated tools can analyze IaC templates to identify security misconfigurations, vulnerabilities, and compliance issues before infrastructure is provisioned.
Automation Tools and Best Practices
AWS Config and AWS Security Hub
- Continuous Monitoring with AWS Config:
AWS Config provides continuous monitoring and assessment of AWS resource configurations. It automatically evaluates resource configurations against desired settings, providing real-time insights into compliance and security posture. This proactive approach helps organizations identify and remediate security issues promptly.
- Centralized Security Visibility with AWS Security Hub:
AWS Security Hub offers centralized security visibility by aggregating findings from various AWS services and third-party tools. It simplifies the detection and prioritization of security issues, streamlining the incident response process. Automated responses can be triggered based on the severity of findings, enhancing overall security automation.
Infrastructure Security Automation
- Automating Security Controls:
Security automation in AWS involves leveraging tools and scripts to automate security controls and responses. This includes automating tasks such as patch management, threat detection, and incident response. By automating routine security tasks, organizations can enhance efficiency and responsiveness to emerging threats.
Conclusion
In conclusion, integrating security into DevOps processes through practices like secure CI/CD pipelines and IaC security scanning is integral to achieving a robust DevSecOps model. Automation tools such as AWS Config and AWS Security Hub contribute to continuous monitoring and centralized security visibility. Embracing infrastructure security automation further fortifies an organization’s ability to respond swiftly to evolving security challenges.
The subsequent sections will explore advanced aspects of AWS security, including compliance measures, data protection strategies, and emerging trends in cloud security. Each component adds layers of resilience to AWS environments, ensuring a comprehensive and adaptive security posture.
AWS Security Compliance
Understanding Compliance Frameworks
HIPAA, GDPR, and Other Regulations
Achieving and maintaining security compliance within the AWS environment requires a comprehensive understanding of relevant frameworks and regulations. This includes compliance with standards such as the Health Insurance Portability and Accountability Act (HIPAA) and the General Data Protection Regulation (GDPR), among others.
- AWS Shared Responsibility Model:
Navigating the AWS Shared Responsibility Model is essential in ensuring compliance. While AWS manages the security of the cloud infrastructure, customers are responsible for securing their data, applications, and configurations within the cloud.
Achieving and Maintaining Compliance
Auditing and Reporting
- Comprehensive Auditing Processes:
To achieve compliance, organizations must implement thorough auditing processes. Regular audits assess the alignment of AWS environments with specific compliance requirements, providing insights into potential gaps that need to be addressed.
Continuous Compliance Monitoring
- Dynamic Compliance Monitoring:
Continuous compliance monitoring involves real-time assessment of AWS environments to ensure ongoing adherence to regulatory standards. Automated tools and processes can detect deviations from compliance requirements promptly, allowing organizations to take corrective actions in a timely manner.
Conclusion
In conclusion, understanding compliance frameworks, such as HIPAA and GDPR, and embracing the AWS Shared Responsibility Model are foundational steps in achieving security compliance within AWS environments. Implementing comprehensive auditing and continuous compliance monitoring processes ensures ongoing adherence to regulatory standards.
The subsequent sections will explore advanced aspects of AWS security, including data protection strategies, incident response best practices, and emerging trends in cloud security. Each component contributes to a resilient and adaptive security posture within AWS environments.
Employee Training and Awareness
Importance of Security Training
Security Awareness Programs
Employee training and awareness play a pivotal role in enhancing the overall security posture of an organization within the AWS environment. Implementing security awareness programs ensures that employees are equipped with the knowledge and skills to identify and mitigate potential security risks.
- Role-Based Training for Teams:
Tailoring training programs to specific roles within the organization is crucial. Role-based training ensures that employees acquire relevant skills and insights aligned with their responsibilities, fostering a more targeted and effective approach to security.
Creating a Security-Aware Culture
Regular Training Modules
- Continuous Learning Initiatives:
Establishing a security-aware culture involves incorporating regular training modules into the organization’s learning framework. Continuous learning initiatives keep employees informed about evolving security threats and best practices.
Simulated Phishing Exercises
- Hands-On Phishing Prevention:
Simulated phishing exercises provide employees with practical experience in recognizing and responding to phishing attempts. These hands-on exercises are instrumental in fortifying the organization against social engineering threats.
Conclusion
In conclusion, prioritizing employee training and awareness is integral to building a resilient security culture within an AWS environment. Security awareness programs, role-based training, and simulated phishing exercises collectively contribute to creating a workforce that is vigilant and proactive in safeguarding against cyber threats.
The subsequent sections will delve into advanced aspects of AWS security, including incident response strategies, data protection measures, and emerging trends in cloud security. Each component adds layers of resilience to AWS environments, ensuring a comprehensive and adaptive security posture.
AWS Security Best Practices for Specific Services
Securing Amazon S3
Bucket Policies and Access Control
Securing Amazon S3 is paramount for safeguarding data stored in the cloud. Implementing robust bucket policies and access control measures ensures that only authorized entities have access to sensitive information. Fine-grained control over permissions enhances overall data security within the S3 environment.
- Data Classification and Lifecycle Management:
Effective security practices for Amazon S3 involve classifying data based on sensitivity and implementing lifecycle management policies. This includes automating data archival and deletion based on predefined criteria, reducing the risk of unauthorized access to obsolete information.
Securing Amazon RDS
Database Encryption
Securing Amazon RDS databases requires robust encryption mechanisms. Implementing encryption at rest and in transit ensures that sensitive data remains protected from unauthorized access. Utilizing industry-standard encryption protocols adds an additional layer of defense against potential security threats.
- Access Controls and Monitoring:
Establishing stringent access controls and continuous monitoring mechanisms is critical for securing Amazon RDS. Limiting access to authorized users and implementing real-time monitoring helps detect and respond to suspicious activities promptly.
Conclusion
In conclusion, implementing security best practices for specific AWS services such as Amazon S3 and Amazon RDS is essential for maintaining a secure cloud environment. By focusing on access controls, encryption, and data lifecycle management, organizations can significantly enhance the overall security posture of their AWS deployments.
The subsequent sections will explore advanced aspects of AWS security, including incident response strategies, compliance measures, and emerging trends in cloud security. Each component contributes to building a robust and adaptive security framework within AWS environments.
Conclusion
Conducting a comprehensive AWS Security Assessment and Enhancement is imperative for organizations seeking to fortify their cloud environments against evolving cyber threats. By understanding the key components of AWS security, including identity and access management, network security, data encryption, threat detection, and incident response, businesses can establish a resilient defense against potential vulnerabilities.
The integration of penetration testing, compliance adherence, and employee training further augments the security posture within AWS environments. Penetration testing ensures proactive identification and resolution of vulnerabilities, while compliance measures align the infrastructure with industry regulations. Employee training cultivates a security-aware culture, empowering the workforce to actively participate in safeguarding against potential risks.
Automated security measures, continuous compliance monitoring, and adherence to best practices for specific AWS services, such as Amazon S3 and Amazon RDS, contribute to a robust security framework. As organizations navigate the dynamic landscape of cloud security, ongoing vigilance, education, and strategic enhancements remain essential. Embracing these principles enables organizations to not only address current security challenges but also proactively prepare for future threats within the AWS ecosystem.
The collective implementation of these practices establishes a resilient security foundation, fostering trust, compliance, and operational excellence within the AWS cloud.
A security assessment in AWS is crucial for identifying vulnerabilities, ensuring compliance, and proactively enhancing the overall security posture of cloud environments.
AWS provides a range of tools and services, including AWS Config, AWS Security Hub, and IAM, to facilitate security assessments and continuously monitor and improve security.
IAM in AWS ensures that only authorized individuals or systems have access to resources, reducing the risk of unauthorized access and data breaches.
Compliance ensures that AWS environments adhere to industry regulations and standards, providing a framework for robust security practices and risk mitigation.
Penetration testing identifies vulnerabilities through simulated attacks, allowing organizations to address weaknesses before they can be exploited by real threats.