Introduction:
Cloud computing has revolutionized the way organizations manage and process their data, providing scalable and flexible solutions to meet evolving business needs. However, as businesses increasingly rely on cloud services, ensuring the security of data and resources becomes paramount. This has led to the emergence of robust cloud security measures, with Identity and Access Management (IAM) playing a crucial role. This discussion will delve into the importance of IAM within the broader context of cloud security, with a specific focus on Google Cloud Platform (GCP) as a leading cloud service provider.
Overview of Cloud Security:
Cloud security encompasses a set of policies, technologies, and controls designed to protect data, applications, and infrastructure in the cloud environment. It addresses concerns related to data breaches, unauthorized access, and compliance with regulatory requirements. IAM, as a subset of cloud security, focuses on managing and controlling access to resources within the cloud infrastructure. Effective IAM ensures that only authorized individuals or systems can access specific resources, reducing the risk of security breaches.
Importance of Identity and Access Management:
IAM is integral to maintaining a secure cloud environment by establishing and managing user identities, defining their roles, and regulating their access permissions. Without proper IAM, organizations risk unauthorized access, data leaks, and compromised systems. IAM helps organizations enforce the principle of least privilege, ensuring users have the minimum necessary access required to perform their tasks. This not only enhances security but also streamlines administration and reduces the chances of human error.
GCP as a Cloud Service Provider:
Google Cloud Platform (GCP) is one of the leading cloud service providers, offering a comprehensive suite of cloud computing services. GCP is known for its robust security measures, including advanced IAM capabilities. GCP’s IAM allows organizations to manage access to resources on its platform securely, providing a flexible and scalable framework for identity and access control.
Understanding GCP IAM Concepts:
GCP IAM is built on several key concepts that form the foundation of its access management framework.
- Identity Providers: GCP supports various identity providers, including Google Accounts, Service Accounts, and external identity providers. These entities define the users and systems that can access GCP resources.
- Roles and Permissions: Roles in GCP define sets of permissions that can be assigned to users, groups, or service accounts. GCP provides predefined roles with specific permissions, and organizations can create custom roles to meet their unique requirements.
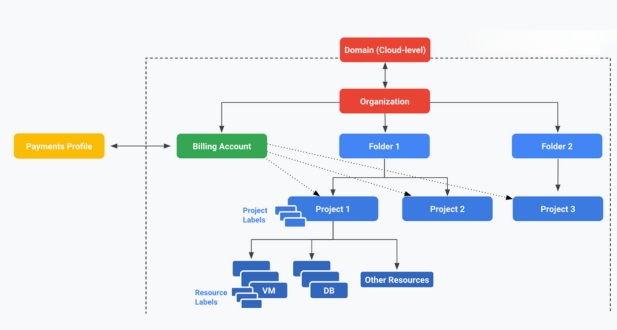
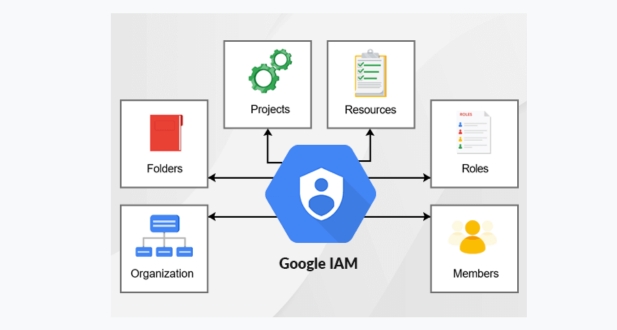
- Resource Hierarchy: GCP resources are organized in a hierarchy, with projects at the top level. The hierarchy includes organizations, folders, and resources within projects. IAM policies can be applied at different levels to control access across the hierarchy.
- Policies and Policy Binding: IAM policies are rules that specify who (identity) has what type of access (permission) to which resources. Policy bindings connect policies to specific resources, defining the access control for those resources.
IAM Roles in GCP
IAM (Identity and Access Management) Roles in Google Cloud Platform (GCP) play a crucial role in defining and managing permissions for resources within the cloud environment. IAM roles are a key component of GCP’s security model, allowing organizations to control access to their resources effectively.
Predefined Roles:
GCP provides a set of predefined roles that cover common use cases and job functions. These roles are designed to encapsulate specific sets of permissions needed for different responsibilities within an organization. Examples of predefined roles include Owner, Editor, and Viewer. The Owner role, for instance, grants full control over resources, while the Editor role allows for modifications but not permission changes, and the Viewer role provides read-only access.
Custom Roles:
In addition to predefined roles, GCP allows organizations to create custom roles tailored to their specific needs. Custom roles enable fine-grained control over permissions by allowing administrators to specify exactly which actions users or service accounts can perform on particular resources. This flexibility is essential for organizations with unique security and compliance requirements that cannot be satisfied by predefined roles alone.
Granting and Revoking Roles:
IAM roles are assigned to identities, such as users, groups, and service accounts, at the project, folder, or resource level. Granting a role to an identity means giving that identity the specified permissions associated with the role. Conversely, revoking a role removes those permissions. This dynamic assignment of roles allows organizations to adapt quickly to changes in personnel or project requirements, ensuring that users have the necessary access without unnecessary privileges.
Best Practices for Role Management:
Effective role management is critical for maintaining a secure and well-organized cloud environment. Some best practices include the principle of least privilege, which advocates for granting users the minimum level of access needed to perform their tasks. Regularly auditing and reviewing roles ensures that permissions align with current organizational requirements. Additionally, organizations should leverage the principle of separation of duties, avoiding situations where a single user or role has excessive power, reducing the risk of unauthorized access or misuse.
IAM roles in GCP provide a robust framework for controlling access to cloud resources. Whether using predefined roles for common scenarios or crafting custom roles for specific needs, understanding and implementing role management best practices is essential for maintaining a secure and efficient cloud infrastructure in the Google Cloud Platform.
Service Accounts in GCP IAM
Service Accounts in Google Cloud Platform (GCP) Identity and Access Management (IAM) play a crucial role in managing and securing access to GCP resources. A Service Account is a special type of Google Account that belongs to your project or a Compute Engine virtual machine (VM) instance, rather than to an individual end user. These accounts are used to perform automated tasks, such as interacting with GCP APIs, without the need for human intervention. Service Accounts are essential for maintaining the security and integrity of GCP environments, allowing for controlled access to various resources.
Creating and Managing Service Accounts
Creating and managing Service Accounts is a fundamental aspect of GCP IAM. Service Accounts can be created through the GCP Console, the command-line interface (CLI), or by using the API. When creating a Service Account, users can assign specific roles and permissions, dictating the level of access the Service Account will have within the project. Properly managing these accounts ensures that the principle of least privilege is upheld, granting only the necessary permissions for a Service Account to perform its designated tasks. Regularly reviewing and updating Service Account permissions is crucial for maintaining a secure GCP environment.
Key Management for Service Accounts
Key management is an integral part of Service Account administration. Service Accounts use cryptographic keys, such as JSON Web Tokens (JWTs), to authenticate and authorize API requests. Users are responsible for securely storing and rotating these keys to minimize the risk of unauthorized access. GCP provides tools and APIs for key management, allowing users to generate and revoke keys as needed. Effective key management practices enhance the overall security posture of GCP environments and help prevent potential security breaches.
Service Account Best Practices
Adhering to best practices when working with Service Accounts is essential for maintaining a secure and well-managed GCP environment. Some key best practices include:
- Principle of Least Privilege: Assign the minimum set of permissions necessary for a Service Account to perform its tasks. Avoid granting unnecessary privileges to mitigate potential security risks.
- Regular Auditing: Periodically review and audit Service Account permissions to ensure they align with the current requirements of your projects. Remove any unnecessary access rights to reduce the attack surface.
- Key Rotation: Implement a key rotation policy to regularly update cryptographic keys associated with Service Accounts. This practice enhances security by minimizing the impact of compromised or outdated keys.
- Use Managed Service Accounts: Leverage Managed Service Accounts whenever possible, as they provide a more secure and automated way to handle Service Account credentials, reducing the risk of credential mismanagement.
Policy in GCP IAM:
In Google Cloud Platform (GCP), Identity and Access Management (IAM) plays a crucial role in controlling access to resources. IAM allows you to define and manage policies that determine who (or what) has access to specific resources and what actions they can perform. Policies in GCP IAM are essentially sets of rules that govern permissions for users, groups, and service accounts. These policies ensure that only authorized entities can interact with GCP resources, contributing to a secure and well-managed cloud environment.
Creating Policies:
Creating policies in GCP IAM involves specifying the permissions for a particular identity (user, group, or service account) on a specific resource. Policies are defined at the project, folder, or organization level and can be inherited by resources within those scopes. When creating a policy, administrators can choose from a wide range of predefined roles that encompass common sets of permissions, or they can define custom roles for more granular control. By carefully crafting policies, organizations can align access permissions with their security and operational requirements.
Understanding Policy Structure:
GCP IAM policies have a hierarchical structure. At the top level, you have the organization, which can contain multiple folders. Each folder can, in turn, contain projects, and projects host GCP resources. Policies can be applied at any of these levels, and they are inherited downward in the hierarchy. The policies themselves consist of bindings, which associate members (identities) with roles.
Effective Policy Management:
Effective policy management in GCP IAM involves regular review, updates, and enforcement of access controls. It’s essential to periodically assess and adjust policies as the organization evolves, ensuring that they remain aligned with security and compliance standards. IAM provides tools for auditing and monitoring changes to policies, allowing administrators to track who has access to what resources and when those permissions were modified. By actively managing policies, organizations can minimize the risk of unauthorized access, reduce the attack surface, and maintain a robust security posture in the cloud.
Policy Best Practices:
Implementing IAM policies in GCP comes with certain best practices to enhance security and operational efficiency. Some key practices include the principle of least privilege, where entities are granted only the minimum permissions necessary for their tasks. Regularly reviewing and auditing policies helps identify and mitigate potential security risks. Organizations should also leverage predefined roles when possible, as they encapsulate well-defined sets of permissions. Additionally, considering resource hierarchy when designing policies ensures that access controls align with organizational structure.
Access Control in GCP IAM
Access Control in Google Cloud Platform’s Identity and Access Management (GCP IAM) is a critical aspect of ensuring the security and integrity of resources within the cloud environment. IAM allows organizations to manage and control access to various GCP resources, such as virtual machines, storage buckets, and databases, among others.
Fine-grained access Control is a feature within GCP IAM that provides organizations with a high level of granularity in defining access permissions. This means that administrators can precisely tailor permissions for individual users or groups, allowing them to perform specific actions on particular resources. Fine-Grained Access Control helps organizations enforce the principle of least privilege, ensuring that users have only the permissions necessary to perform their tasks, reducing the risk of unauthorized access or accidental data exposure.
Conditional IAM takes access control a step further by allowing organizations to set conditions for access based on various parameters. These conditions may include factors such as the user’s location, device characteristics, or time of access. For example, an organization may implement conditional access policies to restrict access to sensitive data only during business hours or from specific geographic locations. This enhances security by adding an additional layer of context-aware control over resource access.
Access Control Best Practices are guidelines and recommendations provided by Google Cloud to help organizations establish and maintain a secure access control framework. These best practices cover a range of areas, including user and group management, role assignment, auditing, and monitoring. By adhering to these best practices, organizations can enhance the overall security posture of their GCP environment. This may involve regularly reviewing and updating access policies, conducting regular audits to identify and address any potential security gaps, and staying informed about the latest IAM features and updates.
GCP IAM offers a robust set of features to manage and control access to resources within the Google Cloud environment. Fine-Grained Access Control provides precision in defining permissions, Conditional IAM adds contextual conditions for access, and Access Control Best Practices offer guidelines to help organizations establish a secure access control framework. Together, these elements contribute to a comprehensive and effective security strategy within GCP.
Integration with External Identity Systems
In the realm of cloud computing, integration with external identity systems is a critical aspect to ensure secure and seamless access to resources. Google Cloud Platform (GCP) employs a robust system for managing identities called Identity and Access Management (IAM). One significant facet of this integration is the concept of Federated Identity. Federated Identity enables users to access multiple applications and services with a single set of credentials across different domains. In the context of GCP IAM, this involves linking external identity providers to GCP, allowing users to authenticate using their existing credentials from these external systems.
Federated Identity and GCP IAM
Federated Identity plays a pivotal role in enhancing user experience and security within the GCP ecosystem. By leveraging standards like OAuth and OpenID Connect, GCP IAM seamlessly integrates with various identity providers, enabling users to log in with their existing credentials. This not only simplifies the authentication process but also centralizes access control, making it easier for administrators to manage permissions across different services and applications.
Identity Providers
Identity Providers (IdPs) are crucial components in the external identity integration landscape. These are external systems or services that manage and authenticate user identities. GCP IAM supports a variety of identity providers, including Google Workspace (formerly G Suite), Microsoft Azure Active Directory, and third-party providers like Okta and Auth0. This flexibility ensures that organizations can choose the identity solution that best aligns with their existing infrastructure and security policies.
Best Practices for External Identity Integration
Ensuring a secure and efficient external identity integration requires adherence to best practices. This includes implementing strong authentication mechanisms, regularly auditing and monitoring access, and staying informed about updates and security patches. Additionally, organizations should adopt a least privilege access model, granting users only the permissions necessary for their roles, thereby minimizing potential security risks.
GCP IAM in Real-World Scenarios
Understanding how GCP IAM operates in real-world scenarios is essential for organizations looking to implement effective identity and access management strategies.
Use Cases Across Different Industries
GCP IAM finds applications across diverse industries, from finance and healthcare to education and e-commerce. Its flexibility allows organizations to tailor access controls to specific industry regulations and compliance requirements. For instance, in healthcare, GCP IAM can be configured to adhere to Health Insurance Portability and Accountability Act (HIPAA) standards, ensuring the secure handling of sensitive patient data.
Case Studies of Successful IAM Implementations
Examining case studies of successful IAM implementations provides valuable insights into the benefits and challenges of deploying GCP IAM. These case studies showcase how organizations have effectively utilized GCP IAM to enhance security, streamline access management, and adapt to evolving business needs.
Lessons Learned from IAM Challenges
IAM implementations are not without challenges, and lessons learned from these challenges are crucial for refining strategies. Issues such as misconfigurations, inadequate training, and evolving threat landscapes can impact the effectiveness of IAM solutions. Learning from these challenges helps organizations proactively address potential pitfalls and continuously improve their identity and access management practices.
Auditing and Monitoring IAM Activities
Auditing and monitoring Identity and Access Management (IAM) activities are critical components of ensuring the security and compliance of cloud environments. This process involves tracking and analyzing user access, permissions, and changes within an IAM system. Three key aspects of auditing and monitoring IAM activities include Cloud Audit Logging, monitoring IAM changes, and the integration of Security Command Center with IAM.
Cloud Audit Logging:
Cloud Audit Logging is a fundamental feature in cloud platforms that enables the recording of activities and events related to IAM. This service provides detailed logs and insights into who did what, where, and when within the IAM infrastructure. These logs are invaluable for security investigations, compliance audits, and incident response. By centralizing and analyzing these logs, organizations can gain visibility into potential security threats, unauthorized access, or configuration errors. Cloud Audit Logging contributes to a proactive security posture by allowing organizations to detect and respond to suspicious activities in real-time.
Monitoring IAM Changes:
Effective monitoring of IAM changes involves continuous tracking of modifications to user permissions, role assignments, and other access controls. This includes additions, modifications, and deletions of users, roles, and policies. Monitoring IAM changes is crucial for detecting and responding to unauthorized or suspicious activities that could compromise the security of the cloud environment. Automated alerts and notifications can be configured to promptly notify administrators of any significant changes, enabling them to take immediate action to mitigate potential security risks. Regular reviews of these changes also contribute to maintaining a well-defined and secure IAM infrastructure.
Security Command Center and IAM:
Integrating Security Command Center with IAM enhances the overall security posture of a cloud environment. Security Command Center is a comprehensive security management and data risk platform that provides a unified view of security threats and vulnerabilities. When integrated with IAM, it offers a centralized dashboard for monitoring and managing access controls, permissions, and user activities. This integration allows security teams to correlate IAM events with broader security incidents, providing context and facilitating a more effective response to potential security threats. By leveraging Security Command Center in conjunction with IAM, organizations can strengthen their security strategy, streamline incident response, and enhance overall cloud security.
Best Practices for GCP IAM Security
Auditing and monitoring IAM activities are integral to maintaining a secure and compliant cloud environment. Cloud Audit Logging, continuous monitoring of IAM changes, and the integration of Security Command Center with IAM collectively contribute to a robust security framework, enabling organizations to detect, respond to, and mitigate potential security risks in real-time.
Principle of Least Privilege:
The Principle of Least Privilege (PoLP) is a fundamental concept in GCP IAM (Identity and Access Management) security. It advocates granting users and processes the minimum level of access required to perform their job functions. By adhering to this principle, organizations can mitigate the risk of unauthorized access and potential misuse of sensitive data. This approach helps limit the potential damage caused by accidental or intentional security breaches. Implementation involves defining and assigning roles with the least amount of permissions necessary for users to complete their tasks, ensuring that they can operate effectively without unnecessary access.
Regular Access Reviews:
Regular access reviews are a crucial component of maintaining a secure IAM environment in GCP. Periodic reviews of user permissions and roles help ensure that access remains aligned with current job responsibilities and organizational requirements. This practice involves systematically evaluating and validating user access rights, removing unnecessary permissions, and updating roles based on any changes in job roles or responsibilities. Regular access reviews are essential for identifying and mitigating potential security risks, such as users with excessive permissions or dormant accounts that may pose a threat to the organization’s security posture.
Multi-Factor Authentication (MFA):
Multi-Factor Authentication (MFA) is an effective security measure that adds an extra layer of protection to GCP IAM. MFA requires users to provide multiple forms of identification before gaining access to their accounts or resources. This typically involves something the user knows (e.g., a password) and something the user has (e.g., a mobile device for receiving authentication codes). Enforcing MFA enhances the security of user accounts by reducing the likelihood of unauthorized access, even if login credentials are compromised. It is a recommended practice to enable MFA for all users, especially those with elevated privileges, to bolster the overall security posture of the GCP environment.
IAM Security Checklist:
An IAM security checklist serves as a comprehensive guide for organizations to ensure they are following best practices and maintaining a robust IAM security posture in GCP. This checklist typically includes items such as reviewing and updating roles and permissions, conducting regular access reviews, implementing MFA, monitoring and auditing IAM activities, and staying informed about the latest security features and updates provided by GCP. The checklist acts as a roadmap for organizations to assess, implement, and continuously improve their IAM security measures, helping them stay proactive in addressing potential vulnerabilities and adapting to evolving security threats in the cloud environment. Regularly revisiting and updating the IAM security checklist ensures that the organization’s GCP IAM security remains robust and aligned with industry best practices.
Conclusion
In conclusion, auditing and monitoring IAM activities are integral to maintaining a secure and compliant cloud environment. Cloud Audit Logging, continuous monitoring of IAM changes, and the integration of Security Command Center with IAM collectively contribute to a robust security framework, enabling organizations to detect, respond to, and mitigate potential security risks in real-time.
IAM works by associating roles with Google Cloud resources. Users and service accounts are granted these roles, defining what actions they can perform.
A role is a collection of permissions. It defines a set of actions that can be performed on GCP resources, such as read, write, or modify.
Permissions are granted by assigning roles to users, groups, or service accounts. Roles can be project-level, organization-level, or resource-specific.
The hierarchy in IAM on GCP consists of organizations, folders, projects, and resources. Permissions can be inherited from parent levels to child levels.
Yes, IAM roles can be customized on GCP. Custom roles allow you to define a set of permissions tailored to your specific requirements.