Understanding of AWS Continuous Integration/Continuous Deployment (CI/CD)
Definition of CI/CD and its importance in modern software development:
CI/CD, which stands for Continuous Integration and Continuous Delivery/Continuous Deployment, is a set of practices that enable software development teams to deliver code changes more frequently and reliably.
Continuous Integration (CI) involves frequently integrating code changes into a shared repository. Each integration is verified by automatically building and testing the code. This helps detect integration errors early in the development process, ensuring that the codebase remains stable.
Continuous Delivery (CD) focuses on automating the deployment process to ensure that code changes are always in a deployable state. It involves automating the steps required to release code to production, such as testing, deployment, and validation.
Continuous Deployment (CD) takes the concept further by automatically deploying every change that passes through the CI/CD pipeline to production without manual intervention.
Importance:
CI/CD practices help streamline the development process, reduce the time to market, and improve the overall quality of software.
By automating repetitive tasks such as testing and deployment, CI/CD frees up developers’ time to focus on building features and fixing bugs.
It also encourages collaboration among team members and fosters a culture of continuous improvement.
Key benefits of implementing CI/CD pipelines:
- Faster Time to Market: CI/CD allows teams to release software updates more frequently, reducing the time it takes to deliver new features to users.
- Improved Quality: Automated testing and continuous feedback loops help catch bugs and errors early in the development process, leading to higher-quality software.
- Reduced Risk: Automated deployments and comprehensive testing minimize the risk of introducing errors into production environments.
- Increased Collaboration: CI/CD encourages collaboration among developers, testers, and operations teams by providing a standardized and automated process for delivering changes.
- Scalability: CI/CD pipelines can easily scale to handle growing codebases and development teams, ensuring that the development process remains efficient and consistent.
Overview of CI/CD workflow: from code commit to deployment:
- Code Commit: Developers push code changes to a version control system.
- Continuous Integration: The CI server automatically builds and tests the code whenever changes are pushed to the repository.
- Artifact Generation: Upon successful build and testing, artifacts (e.g., compiled binaries, Docker images) are generated.
- Continuous Delivery/Deployment: The artifacts are deployed to various environments (e.g., development, staging, production) based on predefined rules and triggers.
- Automated Testing: Automated tests, including unit tests, integration tests, and acceptance tests, are executed to verify the functionality and quality of the application.
- Deployment: The application is deployed to production or staging environments, either automatically (Continuous Deployment) or manually (Continuous Delivery) after passing all tests.
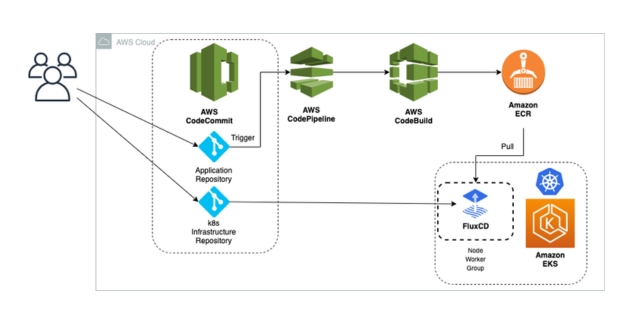
Introduction to AWS CodePipeline as the central orchestrator of CI/CD pipelines on AWS:
AWS CodePipeline is a fully managed continuous integration and continuous delivery service provided by Amazon Web Services (AWS). It allows you to automate the build, test, and deployment phases of your release process.
Features:
- Pipeline Orchestration: CodePipeline allows you to define and manage your CI/CD pipelines as a series of stages and actions.
- Integration with AWS Services: It seamlessly integrates with other AWS services such as AWS CodeBuild, AWS CodeDeploy, and AWS Lambda for building, testing, and deploying applications.
- Customization and Flexibility: CodePipeline supports custom actions and third-party integrations, allowing you to extend its capabilities to suit your specific requirements.
- Scalability and Reliability: As a managed service, CodePipeline provides scalability, high availability, and reliability out of the box, so you can focus on building and delivering your applications without worrying about infrastructure management.
AWS CodePipeline simplifies the process of setting up and managing CI/CD pipelines on AWS, enabling teams to deliver software changes faster and more efficiently.
Core Components of AWS CI/CD
AWS CodePipeline:
- Features: AWS CodePipeline is a continuous integration and continuous delivery service that automates the build, test, and deployment phases of your release process. It provides a graphical user interface for creating, configuring, and managing your pipelines. CodePipeline supports various source control repositories such as AWS CodeCommit, GitHub, Bitbucket, and Amazon S3.
- Capabilities: CodePipeline allows you to define the workflow of your release process using stages and actions. Each stage represents a phase of the pipeline, such as source, build, test, and deploy. Actions within each stage are tasks performed by AWS services or custom scripts. CodePipeline integrates seamlessly with other AWS services like AWS CodeBuild, AWS CodeDeploy, AWS Elastic Beanstalk, AWS Lambda, and third-party tools through custom integrations.
- Integration: CodePipeline integrates with other AWS services to automate the entire CI/CD process. For example, it can trigger builds using AWS CodeBuild, deploy applications using AWS CodeDeploy, and invoke serverless functions using AWS Lambda. It also supports notifications and approvals to facilitate collaboration and control over the release process.
AWS CodeBuild:
- Role: AWS CodeBuild is a fully managed build service that compiles source code, runs tests, and produces deployable artifacts. It eliminates the need to provision, manage, and scale your own build servers.
- Functions: CodeBuild supports various programming languages, build tools, and frameworks, making it versatile for different types of projects. It pulls source code from your chosen repository, executes build commands specified in the buildspec.yml file, and uploads build artifacts to Amazon S3 or other storage locations.
- Optimization: Best practices for optimizing build processes include caching dependencies, parallelizing builds, and using appropriate instance types based on workload requirements. CodeBuild integrates with AWS CodePipeline to automatically trigger builds when changes are detected in the source repository.
AWS CodeDeploy:
- Automation: AWS CodeDeploy automates the deployment of applications to a variety of compute services such as Amazon EC2 instances, AWS Lambda functions, and Amazon ECS containers.
- Flexibility: CodeDeploy supports different deployment strategies including in-place deployments, blue/green deployments, and canary deployments. This allows you to control the pace and risk of your deployments, ensuring smooth transitions and minimizing downtime.
- Integration: CodeDeploy integrates seamlessly with CodePipeline to automate the deployment process as part of your CI/CD pipeline. It supports application revisions stored in Amazon S3, GitHub, or Bitbucket, making it easy to manage and version your deployments.
AWS CodeCommit:
- Source Control: AWS CodeCommit is a fully managed source control service that hosts private Git repositories. It provides secure and scalable infrastructure for storing and versioning your source code.
- Integration: CodeCommit integrates with other AWS services such as CodePipeline and CodeBuild, allowing you to seamlessly incorporate source control into your CI/CD workflows. It also supports Git commands and repository management features, making it familiar to developers already accustomed to Git workflows.
Designing CI/CD Pipelines on AWS
Designing Continuous Integration/Continuous Deployment (CI/CD) pipelines on AWS involves a strategic approach to leverage AWS services effectively while considering architectural principles, scalability, and efficiency.
Architectural Considerations:
- Scalability: AWS offers a wide range of services that can scale with your application needs. Consider using services like AWS CodePipeline, AWS CodeBuild, and AWS CodeDeploy which can automatically scale based on your workload.
- Fault Tolerance: Distribute your CI/CD pipeline across multiple availability zones to ensure high availability and fault tolerance. Services like AWS CodePipeline can be configured to run in multiple regions for added resilience.
- Security: Implement IAM (Identity and Access Management) policies to control access to your pipeline resources. Utilize AWS Key Management Service (KMS) for encryption of sensitive data such as deployment artifacts.
- Cost Optimization: Leverage AWS’s pay-as-you-go pricing model by optimizing resource usage. Consider using spot instances for AWS CodeBuild to reduce costs for non-critical workloads.
Pipeline Organization Strategies:
- Modularity: Break down your pipeline into smaller, modular stages for easier management and troubleshooting. Each stage should represent a distinct part of your deployment process such as building, testing, and deploying.
- Automation: Automate as much as possible using AWS services like AWS CodePipeline. Define clear transitions between pipeline stages to streamline the deployment process.
- Environment Management: Utilize AWS CloudFormation or AWS Elastic Beanstalk to manage different environments (e.g., development, staging, production) within your pipeline. This ensures consistency and reproducibility across environments.
Advanced Features Implementation:
- Parallel Execution: Improve pipeline efficiency by running independent tasks in parallel. AWS CodePipeline supports parallel stages, allowing you to execute multiple actions concurrently.
- Manual Approval Gates: Introduce manual approval steps in your pipeline to control the promotion of changes to production environments. AWS CodePipeline provides built-in support for manual approval actions.
- Rollback Mechanisms: Implement rollback mechanisms to revert changes in case of deployment failures. Use services like AWS CodeDeploy, which supports automated rollback configurations based on predefined conditions or manual triggers.
Integrating Third-party Tools and Services
Integration/Continuous Deployment (CI/CD) pipelines is crucial for modern software development workflows. This integration allows organizations to leverage a wide range of tools and services available in the market to streamline their development processes, improve efficiency, and enhance the overall quality of their software releases.
Leveraging AWS Marketplace offerings and third-party integrations:
AWS Marketplace provides a vast array of third-party tools and services that can be seamlessly integrated into CI/CD pipelines hosted on Amazon Web Services (AWS). These offerings cover various aspects of the software development lifecycle, including testing, monitoring, security, and deployment. By leveraging these offerings, organizations can access pre-built solutions that help them accelerate their CI/CD processes without the need for extensive custom development.
Integration with popular DevOps tools:
Integrating with popular DevOps tools such as Jenkins, GitLab, and Atlassian Bamboo is essential for ensuring compatibility and interoperability across different stages of the CI/CD pipeline. These tools provide features such as version control, automated builds, testing automation, and deployment orchestration. By integrating them into AWS CI/CD workflows, teams can create a cohesive and efficient development environment that facilitates collaboration and automation.
Best practices for securely integrating external services:
Security is a critical aspect of CI/CD workflows, especially when integrating with external services and third-party tools. Best practices for securely integrating external services into AWS CI/CD workflows include:
Implementing robust authentication and authorization mechanisms to control access to external services and sensitive resources.
Encrypting sensitive data and communications to protect against unauthorized access and data breaches.
Regularly updating and patching third-party tools and dependencies to address security vulnerabilities and ensure compliance with industry standards.
Monitoring and logging activities within the CI/CD pipeline to detect and respond to security incidents in a timely manner.
Following the principle of least privilege to restrict access to only those resources and permissions necessary for each component of the CI/CD pipeline.
By adhering to these best practices, organizations can mitigate security risks associated with integrating external services into their CI/CD workflows and maintain the integrity and confidentiality of their software development processes.
Integrating third-party tools and services into AWS CI/CD pipelines, including popular DevOps tools, requires careful consideration of security implications and adherence to best practices to ensure efficiency, reliability, and security throughout the software development lifecycle.
Securing CI/CD Pipelines on AWS
Securing CI/CD pipelines on AWS (Amazon Web Services) is crucial for ensuring the integrity, confidentiality, and availability of the software development and deployment processes. Here’s a more detailed overview of the key aspects mentioned:
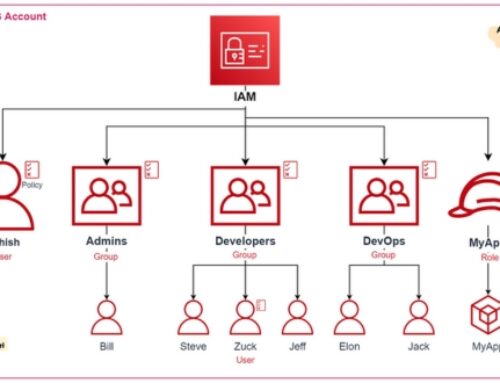
IAM Roles, Policies, and Resource Permissions:
- IAM (Identity and Access Management) roles should be carefully defined and assigned to users, services, or resources within the CI/CD pipeline.
- Follow the principle of least privilege, granting only the permissions necessary for each entity to perform its designated tasks.
- Utilize IAM policies to control access to AWS resources, ensuring that only authorized entities can interact with the pipeline components.
- Regularly review and update IAM policies and roles to align with the evolving requirements and changes in the CI/CD environment.
Encryption at Rest and in Transit:
- Implement encryption mechanisms to protect sensitive data stored within the CI/CD pipeline components, such as source code repositories, build artifacts, and deployment configurations.
- Use AWS Key Management Service (KMS) to manage encryption keys securely and enforce encryption at rest for data stored in Amazon S3 buckets, EBS volumes, and other storage services.
- Configure SSL/TLS encryption for communication channels between pipeline components, ensuring that data transmitted between services remains protected from eavesdropping and tampering.
Compliance with Industry Standards and Regulatory Requirements:
- Understand the specific compliance requirements relevant to your industry, such as GDPR, HIPAA, PCI DSS, or SOC 2, and ensure that the CI/CD pipeline adheres to these standards.
- Implement controls and processes to monitor and audit pipeline activities, maintaining an audit trail of changes, deployments, and access events.
- Integrate compliance checks into the CI/CD workflow, automating the validation of security controls, vulnerability assessments, and configuration management checks.
- Regularly assess the CI/CD pipeline against industry standards and regulatory frameworks, addressing any gaps or non-compliance issues promptly.
In addition to these key practices, it’s essential to adopt a holistic approach to security by implementing other relevant security measures such as network segmentation, secure coding practices, vulnerability management, and incident response procedures. By incorporating security into every stage of the CI/CD pipeline, organizations can minimize risks, safeguard sensitive data, and maintain the trust of customers and stakeholders.
Best Practices
Case studies of organizations successfully implementing CI/CD pipelines on AWS:
Case studies provide real-world examples of how organizations have implemented CI/CD pipelines on AWS, showcasing their challenges, strategies, and outcomes. These studies often highlight the benefits of using AWS services such as CodePipeline, CodeBuild, and CodeDeploy for automating various stages of the software development lifecycle. Examples may include companies from diverse industries like technology, finance, healthcare, or e-commerce, demonstrating how CI/CD pipelines have improved their release cycles, reduced errors, and enhanced overall efficiency.
Best practices for overcoming common challenges and pitfalls in CI/CD adoption:
CI/CD adoption can face numerous challenges, including cultural resistance, lack of automation expertise, security concerns, and integration issues. Best practices offer guidance on addressing these challenges effectively. Strategies may include establishing clear goals and expectations, providing comprehensive training for teams, implementing robust security measures such as automated testing and vulnerability scanning, and gradually phasing in CI/CD processes to minimize disruption. Additionally, best practices may emphasize the importance of continuous monitoring and feedback loops to identify and address issues promptly.
Tips for fostering a culture of continuous improvement and innovation within development teams:
Creating a culture of continuous improvement and innovation is crucial for the success of CI/CD initiatives. Tips for fostering this culture often include promoting transparency, collaboration, and accountability among team members. Encouraging experimentation and embracing failure as a learning opportunity can also stimulate innovation. Additionally, providing resources for professional development, such as training programs and hackathons, can empower developers to explore new technologies and methodologies. Leaders play a vital role in setting the tone for innovation by recognizing and rewarding innovative ideas and initiatives within the organization.
By studying successful implementations, adopting best practices, and fostering a culture of continuous improvement and innovation, organizations can maximize the benefits of CI/CD pipelines on AWS and drive meaningful transformation in their software development processes.
Monitoring and Performance Optimization
Monitoring and performance optimization are critical aspects of continuous integration and continuous deployment (CI/CD) pipelines, ensuring that software development processes run smoothly and efficiently. Let’s delve deeper into each component mentioned:
Comprehensive Monitoring and Logging with AWS CloudWatch and Other Tools:
- AWS CloudWatch: AWS CloudWatch is a monitoring and observability service provided by Amazon Web Services. It allows you to collect and track metrics, monitor log files, set alarms, and automatically react to changes in your AWS resources. In the context of CI/CD pipelines, CloudWatch can be used to monitor various metrics such as build duration, resource utilization, and error rates.
- Other Monitoring Tools: Apart from CloudWatch, there are several other monitoring tools available in the market such as Prometheus, Grafana, Datadog, and New Relic. These tools offer additional capabilities for monitoring various aspects of CI/CD pipelines, including infrastructure monitoring, application performance monitoring (APM), and user experience monitoring.
Performance Optimization Techniques:
- Parallelization: Splitting tasks across multiple agents or nodes to run in parallel can significantly reduce the overall build and deployment times. This can be achieved by using parallel stages or jobs in CI/CD pipelines.
- Caching: Caching dependencies, build artifacts, and intermediate files can help speed up subsequent builds by reducing the need to re-download or recompile them.
- Optimizing Docker Images: Streamlining Docker images by removing unnecessary layers, reducing image size, and optimizing Dockerfiles can improve build and deployment times.
- Infrastructure Scaling: Automatically scaling infrastructure resources such as compute instances or containers based on workload demands can ensure optimal performance during peak usage periods.
- Code Optimization: Identifying and optimizing performance bottlenecks in application code, such as inefficient algorithms or resource-intensive operations, can lead to significant improvements in overall system performance.
Utilizing AWS X-Ray for Distributed Tracing:
AWS X-Ray: AWS X-Ray is a distributed tracing service that helps developers analyze and debug distributed applications, such as those built using a microservices architecture. It provides end-to-end visibility into requests as they travel through various components of the application stack, allowing you to identify performance bottlenecks, latency issues, and errors.
Troubleshooting Performance Bottlenecks: By instrumenting your CI/CD pipelines and application code with X-Ray, you can trace requests from the moment they enter the system until they exit, gaining insights into the performance of individual components and the interactions between them. This can help you identify and address performance bottlenecks more effectively, ultimately improving the overall reliability and efficiency of your CI/CD workflows.
Conclusion:
In conclusion, AWS CI/CD empowers organizations to accelerate their software delivery lifecycle, reduce manual intervention, and improve overall code quality. By leveraging AWS’s robust suite of CI/CD services and adhering to best practices outlined in this guide, teams can achieve greater agility, reliability, and innovation in their software development processes. Whether you’re a startup, enterprise, or independent developer, mastering AWS CI/CD is essential for staying competitive in today’s fast-paced digital economy.
Continuous Integration (CI) is the practice of integrating code changes from multiple developers into a shared repository frequently, followed by automated build and test execution.
Continuous Deployment (CD) involves automatically deploying code changes to production or staging environments after passing the CI tests.
AWS offers services like AWS CodeBuild and AWS Device Farm that facilitate automated testing. CodeBuild can execute unit tests, integration tests, and other types of tests as part of the build process. Device Farm provides real-device testing for mobile applications.
AWS Lambda enables serverless computing, allowing developers to run code without provisioning or managing servers. It can be used in CI/CD pipelines for executing custom logic or automating tasks, such as triggering deployments based on specific events.
Security in CI/CD pipelines on AWS can be ensured by implementing best practices such as using AWS Identity and Access Management (IAM) roles with least privilege, encrypting sensitive data, integrating security checks into the pipeline (e.g., vulnerability scanning), and adhering to AWS security standards.
AWS offers services like AWS CloudWatch, AWS X-Ray, and AWS CodePipeline’s built-in monitoring capabilities to monitor CI/CD pipelines. Developers can set up alarms, visualize pipeline executions, and trace performance bottlenecks to troubleshoot issues effectively.