Introduction
What is AWS CloudTrail?

AWS CloudTrail is a service provided by Amazon Web Services (AWS) that enables governance, compliance, operational auditing, and risk auditing of your AWS account. It records all API calls made on your AWS account, providing visibility into user activity and resource usage. CloudTrail captures API calls made via the AWS Management Console, AWS Command Line Interface (CLI), SDKs, and other AWS services.
Core Components of AWS CloudTrail
The core components of AWS CloudTrail include:
- Trails: Trails are configurations that specify the types of events to log and the destination to which log files are delivered.
- Event history: CloudTrail records every API call made within your AWS account as an event.
- Log files: CloudTrail stores logs as JSON files in an Amazon S3 bucket. These logs contain information about the API call, including who made the call, when it was made, and which resources were affected.
- CloudWatch Logs integration: You can optionally configure CloudTrail to send log events to CloudWatch Logs for real-time monitoring and alerting.
Benefits of AWS CloudTrail
- Auditing: CloudTrail enables auditing of AWS API activity, providing detailed records for compliance and governance purposes.
- Security: It helps in detecting and investigating security incidents by providing insight into changes made to AWS resources.
- Operational insight: CloudTrail logs offer valuable operational insight into resource usage, access patterns, and system behavior.
- Compliance: CloudTrail assists in meeting compliance requirements by providing a detailed history of API calls made on your AWS account.
Use Cases of AWS CloudTrail

Some common use cases for AWS CloudTrail include:
- Security analysis: Investigating security incidents and unauthorized access attempts.
- Compliance auditing: Meeting regulatory compliance requirements by maintaining detailed logs of all API activity.
- Operational troubleshooting: Analyzing API calls to identify operational issues or diagnose errors.
- Change tracking: Tracking changes to AWS resources for auditing and accountability purposes.
Setting Up AWS CloudTrail
- Create a Trail: Define a Trail configuration specifying the events to log and the S3 bucket to store log files.
- Enable CloudTrail: Activate CloudTrail for your AWS account or specific AWS regions.
- Configure logging: Choose the level of logging detail and configure integration with CloudWatch Logs if desired.
Configuring AWS CloudTrail Trails

Trail name: A unique name for the Trail configuration.
S3 bucket: The Amazon S3 bucket where CloudTrail log files will be stored.
Logging settings: Configuration options for log file delivery, including encryption and log file validation.
Interpreting CloudTrail Logs
- Event metadata: Details about the API call, including the user identity, timestamp, and source IP address.
- Resource information: Information about the AWS resource affected by the API call.
- User agent: Information about the tool or service used to make the API call.
- Request and response elements: Additional details about the API request and response.
Security and Compliance with AWS CloudTrail
CloudTrail enhances security and compliance by:
- Recording all API activity: Providing a comprehensive audit trail for security analysis and compliance auditing.
- Integrating with AWS Identity and Access Management (IAM): Allowing you to control access to CloudTrail resources and restrict who can view or modify Trail configurations.
- Supporting encryption and access controls: Enabling you to encrypt log files at rest and restrict access to CloudTrail log data using IAM policies.
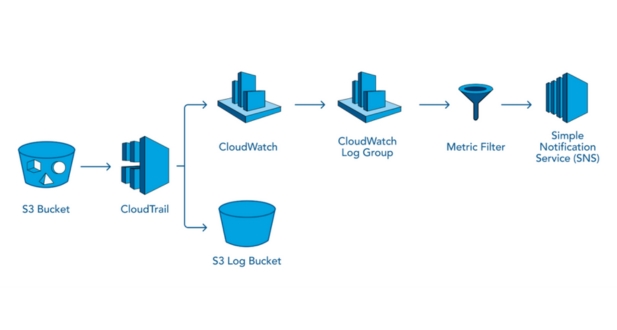
Integrating AWS CloudTrail and CloudWatch
Integrating AWS CloudTrail and CloudWatch offers a robust solution for monitoring, analyzing, and responding to events and activities within your AWS environment. Here’s a more detailed exploration of each aspect mentioned:
Synergies between CloudTrail and CloudWatch:
CloudTrail records API calls and events for your AWS account and delivers log files to an Amazon S3 bucket, while CloudWatch provides monitoring and management for AWS resources and applications.
By integrating CloudTrail with CloudWatch, you can gain real-time visibility into AWS API activity and use CloudWatch features to analyze and respond to events efficiently.
Sending CloudTrail Logs to CloudWatch:
AWS provides a simple way to send CloudTrail logs directly to CloudWatch Logs. This enables you to centralize log data and take advantage of CloudWatch’s powerful log management and analysis capabilities.
Leveraging CloudWatch Alarms for CloudTrail Events:
CloudWatch Alarms allow you to set up notifications based on predefined thresholds or conditions. By creating alarms based on CloudTrail events, such as unauthorized access attempts or changes to critical resources, you can receive immediate alerts and take proactive measures to address potential security issues.
Building Custom Monitoring Solutions with CloudTrail and CloudWatch:
CloudTrail and CloudWatch provide APIs and SDKs that allow you to build custom monitoring solutions tailored to your specific requirements. You can programmatically retrieve and analyze CloudTrail logs, integrate them with other AWS services or third-party tools, and create custom dashboards and reports to gain deeper insights into your AWS environment.
Real-time Analysis and Alerting:
With CloudWatch, you can set up real-time metric filters and alarms to detect and respond to events as they occur. This enables you to quickly identify and mitigate security threats, performance issues, or compliance violations before they escalate.
Cost Optimization Strategies with CloudTrail and CloudWatch:
By monitoring and analyzing AWS usage and resource utilization data captured by CloudTrail and CloudWatch, you can identify opportunities to optimize costs, such as rightsizing instances, implementing auto-scaling policies, or optimizing storage usage. Additionally, CloudWatch offers detailed billing metrics and cost allocation tags that help you track and manage AWS spending effectively.
Scaling and Performance Optimization:
CloudTrail and CloudWatch are designed to scale with your AWS environment, allowing you to monitor and manage resources across multiple regions and accounts. By fine-tuning monitoring configurations, leveraging features like CloudWatch Logs Insights for advanced log analysis, and implementing best practices for performance optimization, you can ensure optimal performance and reliability for your AWS workloads.
Leveraging CloudTrail for Security and Compliance
Auditing AWS API Calls and Activities (3.1):
- CloudTrail records API calls and actions taken by users, services, or AWS resources, providing detailed information such as who made the call, the source IP address, when the call was made, and more.
- This auditing capability enables organizations to track changes and activities within their AWS environment, helping to identify potential security issues, unauthorized access, or compliance violations.
Detecting and Investigating Security Incidents (3.2):
- CloudTrail logs can be analyzed to detect and investigate security incidents such as unauthorized access attempts, changes to permissions, or unusual activity patterns.
- By monitoring CloudTrail logs in real-time or through periodic analysis, security teams can identify anomalies or indicators of compromise and take appropriate actions to mitigate risks.
Ensuring Compliance with Regulatory Requirements (3.3):
- CloudTrail logs provide a detailed trail of activities within an AWS account, which can be invaluable for demonstrating compliance with various regulatory requirements such as GDPR, HIPAA, PCI DSS, etc.
- Organizations can use CloudTrail logs to show auditors or regulators that they have implemented appropriate controls and are effectively monitoring and managing their AWS environment.
Integrating CloudTrail with AWS Config and Security Services (3.4)
- AWS Config is a service that enables the assessment, audit, and evaluation of the configurations of AWS resources. Integrating CloudTrail with AWS Config provides additional context and visibility into changes made to resources.
- Furthermore, CloudTrail can be integrated with other AWS security services such as AWS Identity and Access Management (IAM), AWS Security Hub, and AWS Guard Duty to enhance overall security posture and incident response capabilities.
Implementing Security Automation with CloudTrail (3.5):
- CloudTrail logs can be leveraged to automate security-related tasks and responses to events within an AWS environment.
- For example, organizations can use CloudTrail logs to trigger AWS Lambda functions or AWS Step Functions to automatically respond to security incidents, such as disabling compromised accounts or blocking suspicious IP addresses.
Leveraging CloudTrail for security and compliance in AWS involves utilizing its auditing capabilities, integrating it with other AWS services, and leveraging its logs for real-time monitoring, incident detection, investigation, and automation to enhance the security posture of AWS environments and ensure compliance with regulatory requirements.
Setting Up CloudWatch Monitoring
Configuring Metrics and Alarms
- Metrics: CloudWatch collects and stores metrics from various AWS services, providing insights into resource utilization, performance, and operational health. Configuring metrics involves selecting the relevant metrics for your resources and applications.
- Alarms: Alarms are notifications triggered based on predefined thresholds set on CloudWatch metrics. These thresholds can indicate when resources are experiencing issues or approaching capacity limits. Configuring alarms ensures timely alerts for proactive monitoring and intervention.
Creating Custom Dashboards
Custom Dashboards: CloudWatch allows you to create custom dashboards to visualize metrics and alarms relevant to your specific use cases and applications. These dashboards provide a centralized view of key performance indicators (KPIs) and enable stakeholders to monitor the health and performance of their systems in real time.
Utilizing CloudWatch Logs for Monitoring and Troubleshooting
CloudWatch Logs: CloudWatch Logs enables you to collect, store, and monitor logs from various AWS services and applications. By analyzing logs, you can gain insights into system behavior, diagnose issues, and troubleshoot errors effectively. Configuring log streams and filters enhances visibility into system activity and performance.
Integrating CloudWatch with AWS Services and Applications
Integration: CloudWatch seamlessly integrates with a wide range of AWS services and applications, allowing you to monitor and manage your entire AWS environment from a single platform. Integrating CloudWatch with services such as EC2, RDS, Lambda, and S3 enables comprehensive monitoring and automation of resource management tasks.
Best Practices for CloudWatch Monitoring Implementation
Best Practices: Implementing CloudWatch monitoring effectively requires adherence to best practices to ensure optimal performance, cost-efficiency, and security. Best practices may include defining clear monitoring objectives, selecting appropriate metrics and alarms, optimizing resource utilization, configuring logging and retention policies, and regularly reviewing and refining monitoring configurations.
Advanced CloudWatch Use Cases
Performance Optimization and Resource Management:
CloudWatch provides extensive monitoring capabilities for AWS resources such as EC2 instances, databases, load balancers, and more. With custom metrics and alarms, you can set up alerts to notify you when performance metrics exceed certain thresholds. This allows you to proactively optimize your resources for better performance and cost-efficiency. For example, you can scale up or down your EC2 instances based on CPU utilization metrics to ensure optimal performance without over-provisioning resources.
Application Monitoring and Performance Insights:
CloudWatch enables you to monitor the performance of your applications running on AWS infrastructure. By collecting and analyzing logs, metrics, and traces, you gain insights into application health, response times, error rates, and other critical performance indicators. This helps you identify bottlenecks, troubleshoot issues, and optimize the performance of your applications to deliver a better user experience.
Infrastructure Scaling and Auto-Scaling:
CloudWatch integrates seamlessly with AWS Auto Scaling to automatically adjust the capacity of your AWS resources based on demand. By setting up CloudWatch alarms to trigger scaling actions, you can dynamically scale your infrastructure in response to changing workload patterns. This ensures that your applications can handle fluctuations in traffic efficiently, while also optimizing resource utilization and minimizing costs.
Cost Optimization with CloudWatch Billing and Usage Reports:
CloudWatch provides detailed billing and usage reports that allow you to track and analyze your AWS spending. By monitoring usage metrics, identifying cost drivers, and setting up budget alerts, you can optimize your resource usage and control costs effectively. CloudWatch also offers insights into Reserved Instance utilization and recommendations for purchasing Reserved Instances to maximize cost savings.
Cross-Account Monitoring and Multi-Region Setup:
CloudWatch supports cross-account monitoring, allowing you to aggregate and centralize monitoring data from multiple AWS accounts. This is particularly useful for organizations with multiple AWS accounts or environments, providing a consolidated view of performance metrics and alarms across all accounts. Additionally, CloudWatch supports multi-region setup, enabling you to monitor resources and applications deployed in different AWS regions from a single console. This ensures consistent monitoring and management of your AWS infrastructure regardless of its geographical distribution.
Securing CloudWatch Data and Access Controls
Implementing IAM Policies for CloudWatch
IAM (Identity and Access Management) policies dictate who can access what resources within AWS. When it comes to CloudWatch, you want to ensure that only authorized users and services have access to your monitoring data and configurations. This involves creating IAM policies that grant appropriate permissions to users, roles, or groups. For example, you may create policies that allow specific users to view CloudWatch metrics or create alarms while restricting others from making any changes.
Encrypting CloudWatch Logs and Data
Encrypting CloudWatch logs and data ensures that they remain protected from unauthorized access or tampering. AWS offers various encryption options, including server-side encryption (SSE) with AWS Key Management Service (KMS). By enabling encryption, you ensure that even if someone gains access to your logs or data, they cannot read it without the proper decryption keys.
Monitoring and Managing Access to CloudWatch Resources
Continuous monitoring of access to CloudWatch resources is essential for detecting any unauthorized activities or security breaches. You can use CloudTrail to track API calls and AWS Config to monitor changes to CloudWatch configurations. By analyzing these logs and configurations, you can identify and mitigate any security issues promptly. Additionally, regularly reviewing IAM policies and access permissions helps ensure that access is granted based on the principle of least privilege.
Best Practices for CloudWatch Security
Best practices for CloudWatch security include implementing multi-factor authentication (MFA) for privileged accounts, regularly rotating access keys and credentials, using strong encryption for data in transit and at rest, and enabling logging and monitoring features to detect and respond to security incidents promptly. It’s also crucial to stay updated with AWS security advisories and implement patches and updates promptly to mitigate any known vulnerabilities.
Securing CloudWatch data and access controls involves implementing robust IAM policies, encrypting data, monitoring access and activities, and following best practices to ensure the overall security of your cloud monitoring environment. By adhering to these practices, you can mitigate risks and safeguard your organization’s sensitive information and infrastructure.
Best Practices and Recommendations
Designing a Robust Monitoring and Security Strategy
This involves creating a comprehensive plan for monitoring your AWS environment for security threats, performance issues, and compliance violations.
It includes setting up monitoring tools like AWS CloudTrail and CloudWatch to track user activity, API usage, system performance metrics, and log data.
Additionally, implementing security best practices such as using IAM (Identity and Access Management) policies, encryption, and network security controls to protect your resources.
Regularly Reviewing and Optimizing Configurations
Continuously assess and optimize your AWS configurations to ensure they align with best practices and meet your evolving business needs.
This involves reviewing settings related to compute instances, storage, networking, security groups, and other AWS services to ensure they are configured securely and efficiently.
Training and Educating Teams on CloudTrail and CloudWatch
Provide training and education to your teams on how to effectively use AWS CloudTrail and CloudWatch.
This includes understanding how to interpret monitoring data, set up alerts and notifications, troubleshoot issues, and optimize performance based on insights gained from monitoring.
Keeping Abreast of AWS Updates and New Features
Stay informed about the latest updates, features, and best practices provided by AWS.
Regularly review AWS documentation, attend webinars, and participate in training sessions to keep your knowledge up to date.
Understanding new features and updates allows you to leverage them to improve the efficiency, security, and performance of your AWS environment.
Engaging with AWS Community and Support Channels
Take advantage of AWS community forums, user groups, and support channels to seek advice, share experiences, and get assistance with AWS-related challenges.
Engaging with the AWS community can provide valuable insights, best practices, and solutions to common issues.
Utilize AWS support resources such as AWS Support plans, documentation, and forums to troubleshoot problems and get expert assistance when needed.
Integrating CloudTrail and CloudWatch for Enhanced Monitoring and Security
Integrating CloudTrail and CloudWatch for enhanced monitoring and security involves leveraging the capabilities of both AWS services to gain deeper insights into your cloud environment’s activities and to implement proactive measures to ensure the security and reliability of your infrastructure. Here’s a deeper dive into each aspect:
Correlating CloudTrail Events with CloudWatch Metrics:
- CloudTrail captures API activity within your AWS account, providing detailed logs of actions taken by users, services, and resources.
- CloudWatch Metrics provides a way to monitor various aspects of your AWS resources and applications, including system performance metrics and custom application metrics.
- By correlating CloudTrail events with CloudWatch metrics, you can gain deeper insights into the impact of API actions on system performance, resource utilization, and overall health.
- For example, you can correlate API calls related to resource provisioning with metrics such as CPU usage or network traffic to understand the resource consumption patterns associated with specific actions.
Creating Alarms Based on CloudTrail Activities:
- CloudWatch Alarms allow you to set up notifications or automated actions based on predefined thresholds or conditions.
- By analyzing CloudTrail logs and identifying critical events or patterns indicative of security threats or operational issues, you can create alarms to trigger alerts or responses.
- For instance, you can create alarms to notify administrators when unusual or unauthorized API activities are detected, such as changes to IAM policies or access to sensitive resources.
Automating Incident Response with CloudWatch Events:
- CloudWatch Events enable you to respond automatically to system events and trigger actions in response to predefined triggers.
- By configuring event rules based on specific CloudTrail events or patterns, you can automate incident response processes, such as isolating compromised resources, revoking unauthorized access, or launching forensic investigations.
- For example, you can create event rules to automatically block IP addresses associated with suspicious API activity or to trigger the deployment of security patches in response to detected vulnerabilities.
Building Comprehensive Monitoring and Security Workflows:
- By combining CloudTrail, CloudWatch Metrics, Alarms, and Events, you can build comprehensive monitoring and security workflows tailored to your organization’s requirements and risk profile.
- These workflows can include proactive monitoring of critical resources, real-time alerting on security incidents, automated incident response actions, and post-incident analysis and remediation.
- Continuously refining and optimizing these workflows based on insights from monitoring and incident response activities can help strengthen your cloud security posture and operational resilience over time.
Real-Life Use Cases and Success Stories:
- Real-life examples and success stories showcase how organizations have effectively leveraged the integration of CloudTrail and CloudWatch to enhance their monitoring and security capabilities.
- These use cases may include scenarios such as detecting and mitigating insider threats, responding to external cyber attacks, ensuring compliance with regulatory requirements, and optimizing resource utilization and cost management.
- By learning from these experiences and best practices, organizations can adapt and implement similar approaches to address their own monitoring and security challenges effectively.
Integrating CloudTrail and CloudWatch empowers organizations to proactively monitor, analyze, and respond to events and activities within their AWS environments, enabling them to enhance security, compliance, and operational efficiency.
Conclusion
AWS CloudTrail and CloudWatch are indispensable tools for ensuring the security, compliance, and operational efficiency of cloud environments. By implementing these services effectively and following best practices, organizations can gain deeper insights, streamline monitoring processes, and bolster their overall cloud infrastructure’s resilience.
AWS CloudWatch is a monitoring service for AWS resources and applications. It collects and tracks metrics, monitors log files, sets alarms, and automatically reacts to changes in AWS resources.
You can enable CloudTrail in the AWS Management Console by navigating to the CloudTrail service, clicking on “Trails,” and creating a new trail. Follow the prompts to specify settings such as the S3 bucket for log storage and which AWS regions to monitor.
CloudTrail records API activity for your AWS account, while CloudWatch monitors performance metrics and logs of AWS resources. CloudTrail is primarily used for auditing and compliance purposes, while CloudWatch is used for monitoring and troubleshooting.
CloudTrail logs can be used for security analysis, resource change tracking, compliance auditing, troubleshooting, and forensic analysis.
CloudTrail logs API calls made by or on behalf of your AWS account, including calls from the AWS Management Console, SDKs, command-line tools, and other AWS services.