Introduction
Brief overview of AWS Cloud Identity Management:
AWS Cloud Identity Management refers to the set of tools, policies, and procedures employed by Amazon Web Services (AWS) to manage and secure user identities, access controls, and permissions within its cloud infrastructure. This includes services such as AWS Identity and Access Management (IAM), AWS Single Sign-On (SSO), and AWS Directory Service, which facilitate the management of users, groups, roles, and policies across various AWS services and resources.
Importance of identity management in cloud environments:
Identity management is crucial in cloud environments due to several reasons. Firstly, with the increasing adoption of cloud computing, businesses are relying more on remote access to their resources, making it essential to have robust mechanisms for authenticating and authorizing users. Secondly, cloud environments often involve the sharing of resources among multiple users and entities, necessitating stringent controls over who can access what data or services. Thirdly, the dynamic nature of cloud infrastructure requires agile identity management solutions that can adapt to changes in user roles, permissions, and resource configurations.
Objectives of the paper:
The objectives of the paper may include:
- Providing an in-depth understanding of AWS Cloud Identity Management, including its components, functionalities, and best practices.
- Exploring the challenges and complexities associated with identity management in cloud environments and how AWS addresses them.
- Discussing the benefits of implementing robust identity management practices in AWS, such as improved security, compliance, and operational efficiency.
- Presenting case studies or real-world examples illustrating successful implementations of AWS Cloud Identity Management.
- Offering recommendations or strategies for optimizing identity management workflows and mitigating common pitfalls or risks.
- Highlighting emerging trends or advancements in AWS identity management services and their implications for businesses.
- By addressing these objectives, the paper aims to provide valuable insights and guidance to organizations seeking to leverage AWS Cloud Identity Management effectively in their cloud operations.
Understanding AWS Identity and Access Management (IAM)
Overview of IAM:
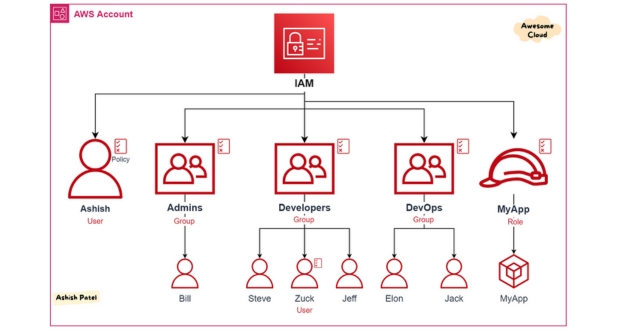
AWS Identity and Access Management (IAM) is a service provided by Amazon Web Services (AWS) that enables you to manage access to AWS services and resources securely. It allows you to control who can access your AWS resources and what actions they can perform. IAM helps you set up and manage users, groups, and roles to grant the appropriate level of permissions needed to perform tasks within your AWS environment.
Key features and components:
- Users: IAM allows you to create individual user accounts for anyone who needs access to your AWS account. Each user has unique security credentials.
- Groups: You can organize users into groups and manage permissions collectively. This simplifies the management of permissions for multiple users with similar roles or responsibilities.
- Roles: IAM roles are sets of permissions that you can assign to AWS resources. Roles are commonly used to grant permissions to services, applications, or users from another AWS account.
- Policies: IAM policies are JSON documents that define permissions. Policies can be attached to users, groups, or roles to specify what actions they are allowed or denied to perform on AWS resources.
- Multi-factor authentication (MFA): IAM supports MFA, adding an extra layer of security by requiring users to present two or more forms of authentication before gaining access to AWS resources.
- Identity Federation: IAM enables you to grant temporary access to AWS resources for users authenticated through external identity providers such as Active Directory, LDAP, or Facebook.
IAM policies and permissions:
IAM policies are at the core of controlling access in AWS. Policies define permissions using JSON syntax, specifying which actions are allowed or denied for which AWS resources. They can be attached to users, groups, or roles. Permissions can be fine-grained, allowing you to control access at the level of individual API calls or resources. IAM policies follow the principle of least privilege, meaning users are only granted the permissions necessary to perform their tasks.
Best practices for IAM configuration:
- Use IAM roles for applications running on Amazon EC2: Instead of embedding long-term credentials within applications or instances, use IAM roles to grant temporary credentials to applications running on EC2 instances.
- Implement least privilege: Follow the principle of least privilege when assigning permissions, granting users only the permissions they need to perform their tasks.
- Regularly review and audit permissions: Periodically review IAM policies and permissions to ensure they align with the current requirements and revoke unnecessary permissions.
- Enable MFA: Enable multi-factor authentication for IAM users to add an extra layer of security to your AWS account.
- Monitor IAM activity: Utilize AWS CloudTrail to track API calls made to IAM and other AWS services, helping you identify and investigate suspicious behavior.
Single Sign-On (SSO) Solutions in AWS
Overview of SSO in AWS:
Single Sign-On (SSO) in AWS allows users to authenticate once and gain access to multiple AWS accounts and applications without having to log in multiple times. This enhances user experience and security by reducing the need for remembering multiple passwords and reducing the risk of password-related security incidents. AWS offers various SSO solutions, including AWS Single Sign-On (AWS SSO) and integration with third-party identity providers.
Integrating AWS with third-party identity providers:
AWS allows integration with third-party identity providers (IdPs) such as Microsoft Active Directory, Okta, Google Workspace, or any IdP that supports SAML 2.0 or OpenID Connect. By integrating AWS with these IdPs, organizations can leverage their existing user directories and authentication mechanisms, enabling seamless access control and user management across AWS services and applications.
Benefits and challenges of SSO implementation:
Benefits of implementing SSO in AWS include:
- Improved user experience: Users can access multiple applications with a single set of credentials, reducing the need for remembering and managing multiple passwords.
- Enhanced security: Centralized authentication and access control help enforce security policies consistently across applications and reduce the risk of unauthorized access.
- Simplified administration: SSO streamlines user provisioning, deprovisioning, and access management, leading to reduced administrative overhead and improved operational efficiency.
Challenges of SSO implementation may include:
- Complexity of integration: Integrating SSO with existing infrastructure and applications may require careful planning and coordination.
- User adoption and training: Users may require education and training to understand the new authentication workflow and security implications of SSO.
- Potential for single point of failure: SSO introduces a single point of authentication, which, if compromised, could lead to unauthorized access to multiple applications.
Case studies of successful SSO deployments:
Case studies provide real-world examples of organizations successfully deploying SSO in AWS. These case studies may highlight the challenges faced, the solutions implemented, and the benefits achieved through SSO adoption. They can serve as valuable references for organizations planning to implement SSO in their AWS environments, offering insights into best practices, lessons learned, and potential use cases.
Federated Identity Management
Federated Identity Management (FIM) is a system that enables users to access multiple applications or systems using a single set of credentials, while also allowing organizations to maintain control over their user authentication and authorization processes.
Explanation of federated identity management:
Federated Identity Management allows users to use their existing credentials (such as username and password) from one trusted identity provider to access multiple services or applications across different organizations. Instead of creating separate accounts for each service, users can log in using their existing credentials, which are authenticated by the identity provider. This eliminates the need for users to manage multiple sets of credentials and simplifies the authentication process.
Federating AWS with external identity providers:
In the context of AWS (Amazon Web Services), federated identity management involves integrating AWS with external identity providers, such as Active Directory, Okta, or Google Workspace. This integration allows users to use their existing corporate credentials to access AWS resources, rather than creating separate AWS accounts. AWS supports various federation standards like SAML (Security Assertion Markup Language) and OpenID Connect, enabling seamless integration with different identity providers.
Advantages and limitations of federated identity management:
Advantages:
Improved user experience: Users can access multiple services with a single set of credentials, enhancing convenience and reducing password fatigue.
Enhanced security: Centralized authentication and authorization processes enable organizations to enforce consistent security policies and better protect sensitive data.
Simplified administration: IT administrators can manage user access centrally, reducing administrative overhead and streamlining user provisioning and deprovisioning processes.
Limitations:
Complexity: Setting up federated identity management requires coordination between different systems and organizations, which can be complex and time-consuming.
Dependency on external providers: Organizations rely on external identity providers for authentication, which can introduce dependencies and potential points of failure.
Security risks: Integrating with external identity providers increases the attack surface and introduces potential security vulnerabilities if not properly configured and managed.
Real-world examples of federated identity management in AWS:
- Single Sign-On (SSO) with Active Directory: Many organizations federate AWS with their on-premises Active Directory to enable users to sign in to AWS using their corporate credentials.
- SAML-based federation with identity providers like Okta or Azure AD: Organizations leverage SAML to federate AWS with cloud-based identity providers, allowing users to access AWS resources using their existing cloud identity.
- OpenID Connect integration: AWS supports integration with OpenID Connect providers, enabling users to authenticate to AWS using their Google or Microsoft accounts.
Multi-Factor Authentication (MFA) in AWS
Importance of MFA in securing AWS accounts:
Multi-Factor Authentication (MFA) plays a crucial role in enhancing the security of AWS accounts by adding an additional layer of verification beyond just a username and password. With MFA enabled, even if an attacker manages to obtain a user’s credentials, they would still need the additional factor (typically a physical device or a time-based code generator) to gain access, significantly reducing the risk of unauthorized access and data breaches. MFA helps safeguard sensitive data, resources, and infrastructure within AWS by requiring users to authenticate themselves using something they possess (like a smartphone or hardware token) in addition to something they know (like a password).
Configuring MFA in AWS IAM:
In AWS Identity and Access Management (IAM), administrators can easily configure MFA for user accounts to enforce an additional layer of security. This involves associating an MFA device, such as a virtual MFA device (using apps like Google Authenticator or Authy) or a hardware MFA token, with IAM users. Once configured, users are required to provide both their regular credentials (username and password) as well as the one-time code generated by their MFA device during the authentication process.
Types of MFA supported in AWS:
AWS supports various types of MFA methods, including:
- Virtual MFA devices: These are software-based authenticators that generate time-based one-time passwords (TOTPs) on smartphones or other devices.
- Hardware MFA tokens: Physical devices that generate one-time passwords, typically in the form of a keychain fob or a card.
- SMS-based MFA: AWS also supports MFA via SMS, where users receive one-time codes through text messages on their registered mobile numbers. However, this method is considered less secure due to vulnerabilities associated with SMS interception.
MFA best practices and considerations:
When implementing MFA in AWS, it’s essential to adhere to best practices to maximize security:
- Enable MFA for all IAM users, especially those with administrative privileges or access to sensitive resources.
- Encourage users to use virtual or hardware MFA devices rather than SMS-based authentication for improved security.
- Implement MFA not only for console access but also for programmatic access (using AWS CLI, SDKs, etc.) where applicable.
- Regularly review and monitor MFA configurations, ensuring that revoked or compromised devices are promptly removed from IAM users’ accounts.
- Educate users about the importance of MFA and provide clear instructions on how to set it up and use it effectively.
- Consider integrating MFA with identity federation solutions (e.g., AWS Single Sign-On) for centralized management and enhanced security across multiple AWS accounts and services.
Security Best Practices in AWS Identity Management
Principle of least privilege:
The principle of least privilege is a fundamental concept in security that dictates that individuals or processes should only have access to the resources and permissions necessary to perform their specific tasks and no more. In AWS Identity and Access Management (IAM), this means granting the minimum permissions required for users, groups, or roles to carry out their responsibilities effectively. By adhering to this principle, you can limit the potential damage caused by compromised credentials or insider threats, as attackers will have limited access even if they gain unauthorized access to an account.
Regularly reviewing and auditing IAM configurations:
Regularly reviewing and auditing IAM configurations involves periodically assessing and validating the access permissions granted to users, groups, and roles within your AWS environment. This practice ensures that access remains aligned with business requirements and security policies over time. Through audits, you can identify any overly permissive permissions, unused credentials, or potential misconfigurations that could introduce security risks. By conducting these reviews on a scheduled basis, you can maintain the integrity of your IAM setup and promptly address any issues that arise.
Implementing strong password policies:
Implementing strong password policies is crucial for protecting AWS accounts against unauthorized access. This involves establishing guidelines for creating and managing passwords that are difficult to guess or brute-force. AWS IAM enables you to enforce various password requirements such as minimum length, complexity (including the use of uppercase letters, lowercase letters, numbers, and special characters), and expiration periods. By implementing strong password policies, you reduce the likelihood of successful password-based attacks and enhance the overall security posture of your AWS environment.
Monitoring and alerting for suspicious activities:
Monitoring and alerting for suspicious activities involve continuously monitoring user actions, API calls, and resource usage within your AWS environment for signs of anomalous behavior or potential security threats. AWS provides various monitoring and logging services, such as AWS CloudTrail, AWS Config, and Amazon CloudWatch, which can be leveraged to track and analyze activity logs in real-time. By setting up alerts and notifications based on predefined criteria (e.g., unusual access patterns, unauthorized API calls, privilege escalation attempts), you can promptly detect and respond to security incidents before they escalate. This proactive approach to monitoring helps mitigate risks and ensures the integrity and availability of your AWS resources.
Compliance and Governance in AWS Identity Management
Overview of Compliance Standards in AWS:
- AWS adheres to various compliance standards and certifications such as HIPAA, GDPR, SOC 2, PCI DSS, etc.
- Each compliance standard has its own set of requirements and controls regarding data protection, privacy, security, and governance.
- AWS provides documentation and resources to help customers understand how AWS services can be used to meet compliance requirements.
Using IAM for Regulatory Compliance:
- Identity and Access Management (IAM) is a crucial component for ensuring regulatory compliance in AWS.
- IAM allows organizations to manage user identities, roles, and permissions effectively, ensuring that only authorized users have access to resources.
- By implementing IAM best practices such as least privilege access, role-based access control (RBAC), and multi-factor authentication (MFA), organizations can enhance their compliance posture.
AWS Config and AWS CloudTrail for Governance:
- AWS Config provides continuous monitoring and assessment of AWS resource configurations against predefined rules.
- It helps organizations ensure compliance by detecting configuration changes, assessing their impact, and automatically remediating non-compliant configurations.
- AWS CloudTrail records API activity and user actions in AWS, providing a detailed audit trail for compliance and governance purposes.
- By analyzing CloudTrail logs, organizations can track user activity, detect unauthorized access attempts, and demonstrate compliance with regulatory requirements.
Case Studies of Compliance and Governance Implementation:
Case studies provide real-world examples of how organizations have implemented compliance and governance measures in AWS.
These case studies showcase best practices, challenges faced, and lessons learned during the implementation process.
They serve as valuable resources for other organizations looking to enhance their compliance and governance practices in AWS.
Integration with AWS Organizations
Introduction to AWS Organizations:
AWS Organizations is a service that allows you to centrally manage and govern multiple AWS accounts. It provides features such as consolidated billing, centralized security controls, and simplified management of resources across accounts. Organizations help businesses implement a scalable and efficient multi-account strategy.
Managing multiple AWS accounts with Organizations:
With AWS Organizations, you can create and manage multiple AWS accounts within your organization’s hierarchy. This hierarchical structure allows for better organization and management of resources. You can establish policies at different levels of the hierarchy, such as service control policies (SCPs) to control access to AWS services, and organizational units (OUs) to group accounts based on business units, teams, or applications.
Implementing centralized identity management with Organizations:
One of the key benefits of AWS Organizations is the ability to implement centralized identity management through AWS Single Sign-On (SSO) or AWS Identity and Access Management (IAM). This allows you to manage user access centrally across multiple AWS accounts, simplifying user provisioning, authentication, and authorization processes. Centralized identity management improves security and compliance by ensuring consistent access controls across all accounts.
Benefits and challenges of Organizations integration:
Benefits:
- Simplified management: Organizations streamline the management of multiple AWS accounts by providing a centralized console and API for account provisioning, policy enforcement, and resource management.
- Cost optimization: With consolidated billing, Organizations allow you to aggregate usage and receive volume discounts, leading to cost savings.
- Enhanced security and compliance: By enforcing consistent security policies across accounts and implementing centralized identity management, Organizations improve security posture and facilitate compliance with regulatory requirements.
- Scalability: Organizations support a hierarchical structure that scales with your organization, allowing you to add or remove accounts as needed without compromising management efficiency.
Challenges:
- Complexity: Managing a multi-account environment with Organizations can be complex, especially for organizations with a large number of accounts and diverse workloads.
- Governance overhead: Implementing and enforcing governance policies across multiple accounts requires careful planning and ongoing maintenance to ensure compliance and security.
- Learning curve: Organizations introduce new concepts and practices for managing AWS accounts, which may require training and familiarization for administrators and users.
- Integration with existing systems: Integrating AWS Organizations with existing identity management and governance systems may require custom development and integration efforts.
Conclusion
In conclusion, AWS Cloud Identity Management is a robust and comprehensive solution for managing user identities, access controls, and authentication mechanisms within AWS environments. By leveraging AWS IAM and related services, organizations can enhance security, scalability, flexibility, integration capabilities, compliance, and cost-effectiveness in their cloud infrastructure deployments. However, it’s crucial for organizations to carefully design and implement their identity management strategies to align with their specific security requirements and regulatory obligations. Regular monitoring, review, and updates to IAM configurations are essential to maintain a secure and efficient cloud environment.
IAM users are entities within your AWS account that can be assigned individual security credentials and permissions. IAM roles, on the other hand, are similar to users but are intended for specific tasks, applications, or services. Roles can be assumed by IAM users, AWS services, or even external users.
You can create IAM users and groups through the AWS Management Console, AWS CLI, or API. Once created, you can assign permissions to users and manage their memberships in groups for easier access control management.
IAM policies are JSON documents that define permissions. They can be attached to IAM users, groups, or roles to specify what actions are allowed or denied on AWS resources. Policies are the primary means of managing permissions in IAM.
Temporary access can be granted through IAM roles with temporary security credentials. These credentials are valid for a limited time and are often used for applications running on Amazon EC2 instances or for cross-account access.
Yes, IAM supports integration with external identity providers (IdPs) through standards like SAML 2.0 and OpenID Connect. This enables single sign-on (SSO) capabilities, allowing users to authenticate using their existing credentials.