Introduction to Zoho Workplace User Access Control
Imagine your Zoho Workplace as a bustling city. Information flows like traffic, emails whizz by like scooters, and documents reside in towering skyscrapers. But who gets to navigate this urban landscape? That’s where User Access Control (UAC) steps in, acting as the city’s traffic lights and security guards, ensuring only authorized individuals access the right data at the right time.
What is User Access Control?
Define UAC:
User Access Control (UAC) is the digital guardian of your Zoho Workplace. It’s a system that meticulously manages user access to resources and information within the platform. In the context of Zoho Workplace, UAC governs who can access emails, documents, apps, and other features, creating a secure and organized digital environment.
Key Components:
- Users: These are individuals with Zoho accounts, each with a unique digital identity.
- Roles: Predefined sets of permissions designed for specific tasks or departments. Examples include Administrator, Editor, and Viewer.
- Permissions: These are granular controls, allowing or restricting actions like creating, editing, deleting, or sharing specific data or features.
- Access Levels: Additional restrictions based on factors like location, device, or time of day, adding an extra layer of security.
Why is User Access Control Important?
- Data Security:
In the digital landscape, security is paramount. UAC prevents unauthorized access, acting as a vigilant gatekeeper and safeguarding sensitive information from potential data breaches, leaks, and accidental exposure.
- Compliance:
As businesses navigate complex data privacy regulations like GDPR and CCPA, UAC becomes a crucial ally. It ensures that only authorized individuals handle personal data, promoting compliance and avoiding legal pitfalls.
- Improved Collaboration:
UAC isn’t just about restriction; it’s also about facilitating secure collaboration. By granting access based on need, it prevents confusion, reduces the risk of misuse, and fosters a collaborative environment.
- Enhanced Productivity:
Simplicity often breeds productivity. UAC streamlines access management, reducing the burden on IT teams, and freeing up resources for more strategic tasks.
- Boosted Trust and Reputation:
In an era where data breaches can damage reputations irreparably, a robust UAC system demonstrates a commitment to data security. This builds trust with customers, partners, and employees, enhancing your brand reputation.
Benefits of Using Zoho Workplace User Access Control
- Granular Control:
Zoho Workplace offers a level of granularity that allows you to tailor access to individual files, folders, and app features. This precision ensures that access is finely tuned to business requirements.
- Role-Based Access:
Customization is key in user access management. With Zoho, you can create custom roles with specific permissions, easily assigning them to users based on their job functions and needs.
- Conditional Access Control:
Security isn’t one-size-fits-all. Zoho’s UAC lets you set access rules based on factors like location, device, and time of day, providing an additional layer of security tailored to your unique business needs.
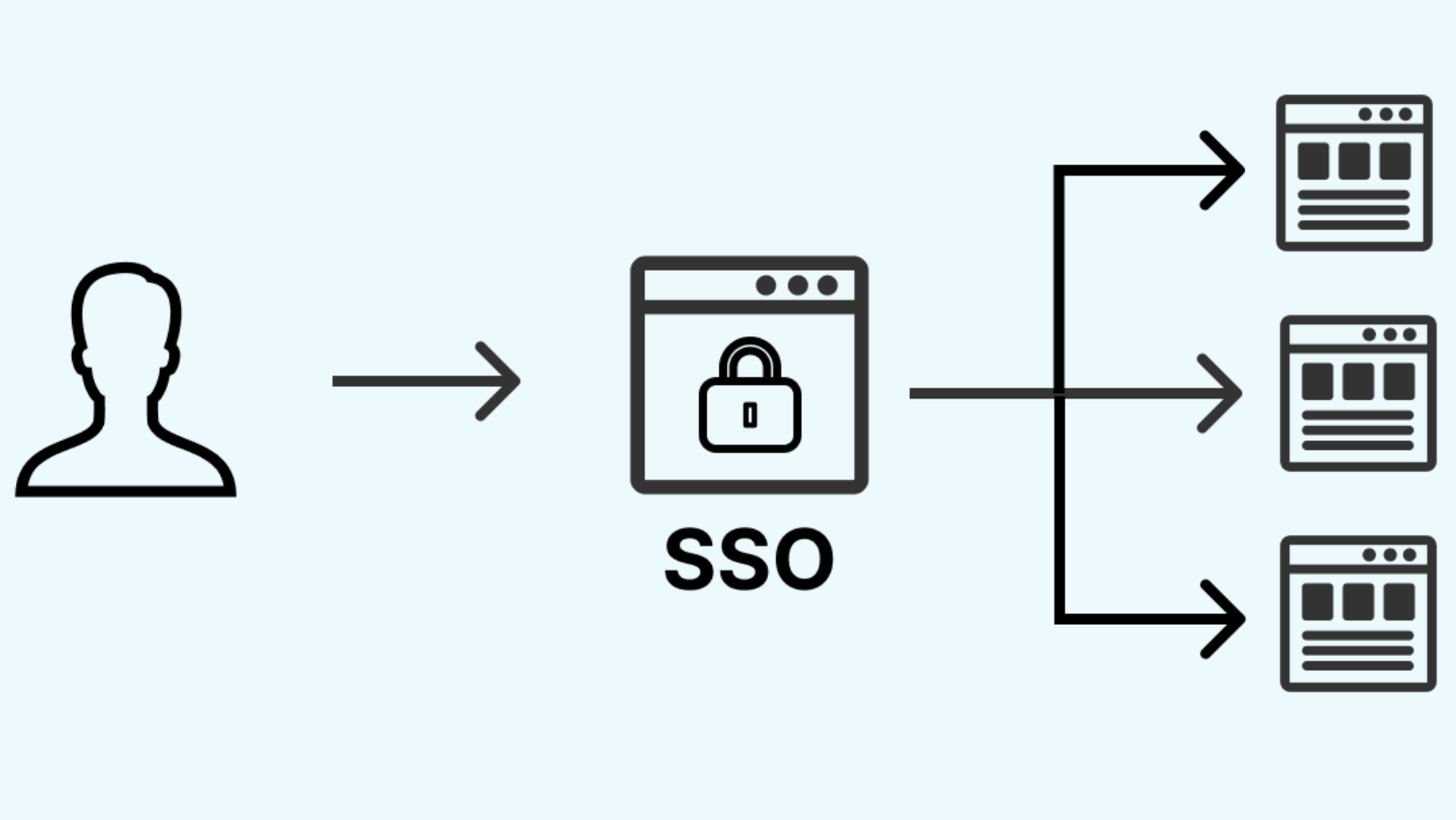
- Single Sign-On (SSO):
Simplify access for your users with Single Sign-On (SSO). This not only enhances user experience but also strengthens security by allowing users to access multiple Zoho applications with a single login.
- Multi-Factor Authentication (MFA):
Security is about layers. MFA adds an extra layer by requiring a second factor, such as a code, for login. This ensures that even if someone knows the password, they need more than that for access.
- Audit Logs and Reporting:
Visibility is crucial in security. Zoho Workplace provides detailed audit logs and reporting tools, allowing you to track user activity, identify trends, and spot suspicious behavior, ensuring a proactive approach to security.
- Scalability:
Businesses evolve, and so do their needs. Zoho’s UAC features are scalable, adapting to your growing business, easily managing access for large teams and complex data structures.
- User-friendly Interface:
UAC features are designed with the end-user in mind. Zoho ensures that even non-technical users can manage access effortlessly, promoting a user-friendly experience across the board.
Zoho Workplace User Access Control is not just a security feature; it’s an investment in your data, business, and brand reputation. By implementing UAC effectively, you can create a secure and collaborative environment where information flows freely but only to those who need it most. It’s the guardian of your digital city, ensuring a smooth and secure journey for every user.
Setting Up User Access Control in Zoho Workplace
User Access Control (UAC) is the backbone of security and organization within Zoho Workplace. Effectively configuring UAC involves creating user roles, defining permissions, assigning these roles to users, and configuring access levels for various applications.
Creating User Roles and Permissions
- Define User Roles:
Start by understanding the organizational structure and tasks within your business. Create user roles that align with these functions, ensuring clarity and relevance. Examples include Administrator, Editor, and Viewer.
- Set Permissions:
Define granular permissions for each role. Consider what actions each role should perform—whether it’s creating, editing, deleting, or sharing specific data or features. This step ensures that every user has precisely the right level of access.
- Configuring Access Levels:
Introduce access levels to add an extra layer of control. Access levels can be based on factors like location, device, or time of day, offering conditional access to further refine security.
Assigning Roles and Permissions to Users
- Identify User Needs:
Understand the tasks and responsibilities of each user. Based on this, assign the appropriate role. Ensure that roles align with job functions to optimize efficiency.
- Role Assignment:
Navigate to the Zoho Workplace admin panel and access the User Management section. Here, you can assign roles to users effortlessly. The system is designed for user-friendly role assignment, even for non-technical users.
- Fine-Tune Permissions:
After role assignment, fine-tune permissions for specific users. Not every user with the same role needs identical permissions. Tailor access to individual requirements to maintain a balance between security and productivity.
Configuring Access Levels for Different Applications
- Evaluate Application Sensitivity:
Different applications within Zoho Workplace may contain varying levels of sensitive information. Evaluate the sensitivity of each application to determine the appropriate access levels.
- Location-Based Access:
For added security, configure access levels based on the user’s location. This ensures that sensitive data is only accessible from authorized locations, minimizing the risk of unauthorized access.
- Device-Based Access:
Consider the devices used by your workforce. If certain devices are more secure or managed, configure access levels accordingly. This ensures that even if login credentials are compromised, access remains restricted based on device policies.
- Time-Based Access:
Time-based access is a powerful tool to control when users can access specific applications. For instance, restrict access to confidential documents outside of regular working hours.
- Single Sign-On (SSO) Integration:
Integrate Single Sign-On (SSO) for a seamless and secure access experience. SSO simplifies the login process, allowing users to access multiple Zoho applications with a single set of credentials.
- Multi-Factor Authentication (MFA):
Enhance security further by configuring Multi-Factor Authentication (MFA). This additional layer requires users to provide a second form of identification, such as a code sent to their mobile device, ensuring robust protection.
Setting up User Access Control in Zoho Workplace is a strategic investment in securing your digital landscape. By meticulously crafting user roles, defining permissions, and configuring access levels, businesses can foster a secure and efficient work environment. With Zoho Workplace, the journey to enhanced access control begins, ensuring that data flows freely but only to those with authorized access.
Managing User Access in Zoho Workplace 
User access management is a critical aspect of maintaining a secure and organized digital workspace. In Zoho Workplace, efficiently managing user access involves tasks such as adding and deleting users, monitoring user activity, and auditing user access logs.
Adding and Deleting Users
Adding Users:
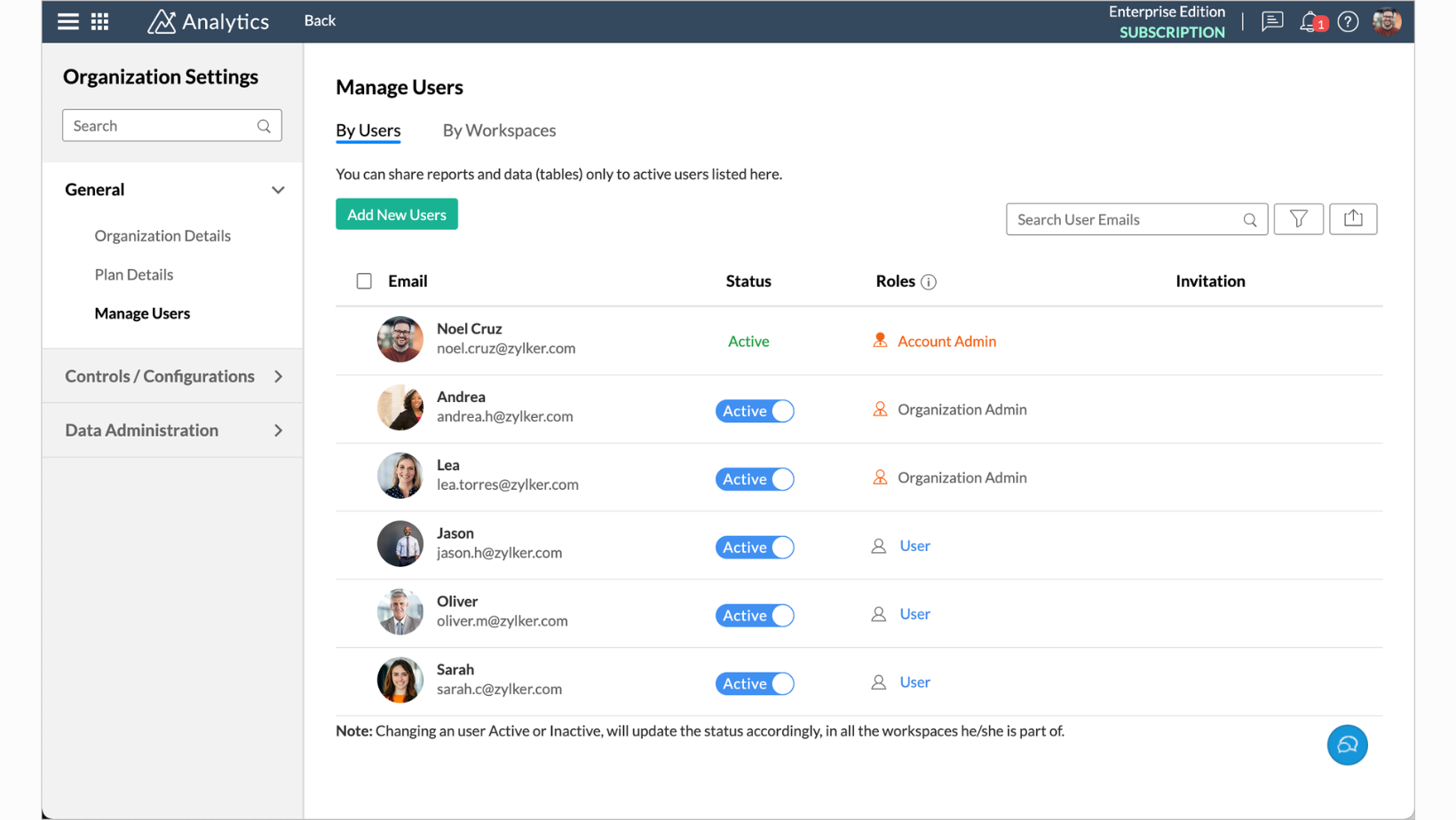
- Navigating to User Management:
Access the Zoho Workplace admin panel and locate the User Management section. This serves as the central hub for user-related activities.
- Adding Individual Users:
Add individual users by providing necessary details such as name, email address, and role. Zoho Workplace offers predefined roles like Administrator, Editor, and Viewer.
- Bulk User Import:
For larger teams, utilize the bulk user import feature. Prepare a CSV file with user details and import it seamlessly to expedite the onboarding process.
- Customizing User Roles:
Tailor user roles based on organizational needs. Assign roles with specific permissions that align with individual responsibilities.
Deleting Users:
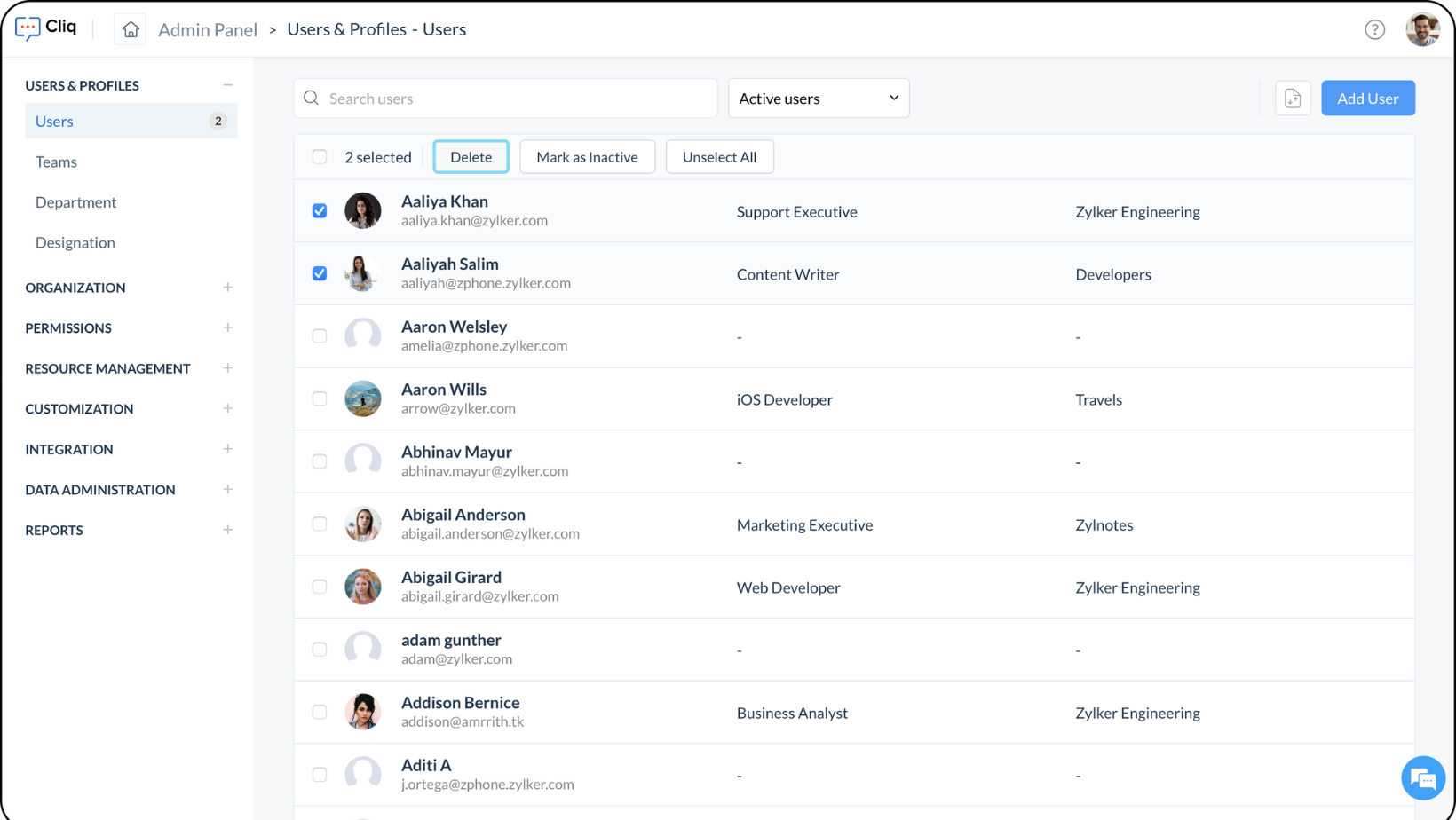
- Accessing User Deletion Settings:
In cases where user access needs to be revoked, navigate to the User Management section and locate the user to be deleted.
- Removing Individual Users:
Delete individual users by selecting the delete option. This action revokes all access
and permissions associated with that user.
- Bulk User Deletion:
For larger-scale user management, leverage bulk user deletion options. Select multiple users for deletion to streamline the process.
Monitoring User Activity
User Activity Overview:
- Dashboard Insights:
Utilize the Zoho Workplace dashboard to gain an overview of user activity. Understand login patterns, application usage, and document interactions.
- Real-time Monitoring:
Zoho Workplace provides real-time monitoring features, allowing administrators to observe user actions as they happen. This ensures prompt responses to any suspicious activities.
Application-Specific Monitoring:
- Email Activity:
Monitor email activity to ensure proper communication within the organization. Identify trends and anomalies in email usage.
Document Interactions:
Track document interactions within Zoho Workplace. Understand who accesses, edits, or shares documents to maintain data security.
Application Usage:
Gain insights into the usage of specific applications. Identify popular tools and ensure that all applications are utilized securely.
Auditing User Access Logs
- Access Logs Overview:
Locating Access Logs:
Access logs are crucial for understanding who accessed what and when. Locate the access logs within Zoho Workplace for comprehensive auditing.
Filtering Logs:
Use filters to narrow down logs based on parameters such as user, date, and application. This targeted approach aids in efficiently auditing specific activities.
User Activity Auditing:
Identifying Anomalies:
Regularly audit user access logs to identify anomalies or unauthorized access attempts. Swiftly address any irregularities to bolster security.
Compliance Tracking:
Maintain compliance by tracking user activities. Ensure that actions align with organizational policies and legal requirements.
Integration with Security Measures:
Integrate access logs with other security measures such as Multi-Factor Authentication (MFA) to create a robust defense against unauthorized access.
Managing user access in Zoho Workplace is a multifaceted process encompassing user addition and deletion, real-time activity monitoring, and comprehensive auditing. By incorporating these practices into your user access management strategy, you not only ensure a secure digital workspace but also lay the foundation for proactive security measures and compliance adherence. Zoho Workplace empowers administrators to navigate this landscape effectively, fostering a secure and efficient work environment.
Advanced User Access Control Features in Zoho Workplace
User access control goes beyond basic permissions; it involves advanced features designed to fortify the digital fortress of your workspace. In Zoho Workplace, three key features take center stage: Single Sign-On (SSO), Multi-Factor Authentication (MFA), and Conditional Access Control.
Single Sign-On (SSO)
Defining Single Sign-On:
Streamlined Access:
Single Sign-On (SSO) is a game-changer in user access. It simplifies the login process by allowing users to access multiple Zoho applications with a single set of credentials. This streamlines the access experience, enhancing user convenience.
Unified User Identity:
SSO creates a unified user identity across various Zoho applications. Users authenticate once, and subsequent access to other connected applications happens seamlessly, reducing the need for multiple logins.
Implementing SSO in Zoho Workplace:
Integration Setup:
Navigate to the Zoho Workplace admin panel and locate the SSO settings. Initiate the integration process by connecting Zoho Workplace with your chosen identity provider.
Customization Options:
Customize SSO settings based on organizational needs. Define policies for user authentication, ensuring that access aligns with security protocols.
User Experience Enhancement:
Evaluate the user experience. SSO not only enhances security but also contributes to user satisfaction by reducing the complexity of accessing various Zoho applications.
Multi-Factor Authentication (MFA)
- Understanding Multi-Factor Authentication:
Layered Security:
Multi-Factor Authentication (MFA) introduces an additional layer of security beyond traditional username and password combinations. It requires users to provide a second form of identification, such as a code sent to their mobile device.
Combatting Unauthorized Access:
MFA is a powerful defense against unauthorized access attempts. Even if someone gains knowledge of the password, MFA adds an extra barrier, ensuring that only authorized users can proceed.
- Configuring MFA in Zoho Workplace:
Accessing Security Settings:
In the Zoho Workplace admin panel, locate the security settings. Navigate to the MFA section to configure multi-factor authentication for users.
Enrollment Processes:
Define the enrollment process for MFA. Zoho Workplace allows administrators to specify how users enroll in MFA, ensuring a smooth transition for enhanced security.
Backup Authentication Methods:
Consider backup authentication methods. In case the primary method is unavailable, users should have alternative options for MFA, maintaining access without compromising security.
Conditional Access Control
- Unveiling Conditional Access Control:
Contextual Access Rules:
Conditional Access Control is about context. It allows administrators to set access rules based on contextual factors such as location, device, or time of day, adding an extra layer of specificity to access management.
Tailored Security Policies:
Tailor security policies based on specific scenarios. For example, restrict access to sensitive information to specific locations or devices, minimizing the risk of unauthorized exposure.
- Setting Up Conditional Access Control in Zoho Workplace:
Accessing Control Settings:
Within the Zoho Workplace admin panel, find the settings for Conditional Access Control. This is where administrators can define rules and conditions.
Location-Based Access Rules:
Configure rules based on location. For instance, restrict access to certain applications or data to specific geographical locations, enhancing security for sensitive information.
Device-Based Access Rules:
Implement device-based access rules. Define conditions for access based on the type of device, ensuring that only authorized devices can access critical data.
Time-Based Access Rules:
Time-based access rules add another layer of control. Limit access to specific applications or features during defined time windows, reducing exposure risks during non-business hours.
Conclusion
Incorporating advanced user access control features like Single Sign-On (SSO), Multi-Factor Authentication (MFA), and Conditional Access Control elevates the security posture of Zoho Workplace. These features not only fortify access but also contribute to a seamless and user-friendly experience. Zoho Workplace empowers organizations with the tools needed to navigate the nuanced landscape of advanced user access control, ensuring a robust and secure digital workspace.
Best Practices for Secure User Access Control in Zoho Workplace
User access control is the linchpin of a secure digital workspace, and adopting best practices is paramount for maintaining data integrity and confidentiality. In Zoho Workplace, three key practices stand out for ensuring secure user access: the Principle of Least Privilege, regular reviews and audits, and user training and awareness.
Principle of Least Privilege
- Understanding the Principle:
Defining Least Privilege:
The Principle of Least Privilege is a security concept advocating for granting individuals the minimum level of access or permissions needed to perform their job functions. In essence, users should only have access to the resources necessary for their roles, minimizing the potential impact of security breaches.
Reducing Attack Surface:
By adhering to the Principle of Least Privilege, organizations can significantly reduce their attack surface. Limiting user access mitigates the risk of accidental or intentional misuse of critical data, enhancing overall security.
- Implementing Least Privilege in Zoho Workplace:
Role-Based Access Control:
Leverage Zoho Workplace’s role-based access control features. Define roles with specific permissions tailored to job functions, ensuring users have precisely the access they need.
Regularly Review and Adjust Roles:
Conduct periodic reviews of user roles and permissions. As job responsibilities evolve, adjust roles accordingly to maintain alignment with the Principle of Least Privilege.
Custom Permissions for Specific Users:
Customize permissions for individual users when necessary. Not every user with the same role requires identical access. Tailor permissions based on specific job requirements to enhance security.
Regular Reviews and Audits
- Importance of Reviews and Audits:
Dynamic Nature of User Access:
User access requirements evolve over time. Employees may change roles, responsibilities, or leave the organization. Regular reviews and audits are essential to ensure that access privileges align with current needs.
Identifying Anomalies:
Regular reviews help identify anomalies in user access patterns. This proactive approach allows administrators to spot unauthorized access attempts or irregularities before they escalate.
- Conducting Reviews and Audits in Zoho Workplace:
Access Logs and Reports:
Leverage Zoho Workplace’s access logs and reporting tools. These features provide detailed insights into user activity, enabling administrators to track changes and identify potential security risks.
Scheduled Audits:
Establish a schedule for access audits. Regularly review user roles, permissions, and access logs. This systematic approach ensures that user access aligns with organizational policies and security standards.
User Departure Protocols:
Implement protocols for user departures. When an employee leaves the organization, ensure that their access is promptly revoked. Regular audits help catch any oversight in the access removal process.
User Training and Awareness
- Building a Security-Conscious Culture:
Educate Users on Security Policies:
Provide comprehensive training on security policies and the importance of secure access practices. Users should be aware of the risks associated with unauthorized access and the role they play in maintaining a secure environment.
Phishing Awareness:
Include phishing awareness in training programs. Phishing attacks can compromise user credentials, leading to unauthorized access. Educate users on recognizing and reporting phishing attempts.
- Training Initiatives in Zoho Workplace:
Incorporate Training Modules:
Utilize training modules within Zoho Workplace. These modules can cover topics such as secure password practices, recognizing suspicious activities, and reporting security incidents.
Regular Security Reminders:
Implement regular security reminders. Periodic communication on secure access practices reinforces the importance of maintaining vigilance and adhering to security protocols.
Conclusion (50 words)
In Zoho Workplace, implementing the Principle of Least Privilege, conducting regular reviews and audits, and prioritizing user training and awareness are pivotal for establishing a secure user access control framework. These best practices collectively contribute to creating a resilient and secure digital workspace, ensuring that user access aligns with organizational security objectives and safeguards sensitive information effectively.
Conclusion
In conclusion, Zoho Workplace emerges as a robust platform for organizations seeking secure and efficient user access control. Implementing best practices ensures not only the protection of sensitive data but also the cultivation of a culture where security is ingrained in every aspect of digital interactions.
The Principle of Least Privilege serves as a foundational pillar, emphasizing the importance of granting users the minimum access necessary for their roles. By leveraging Zoho Workplace’s role-based access controls and regularly reviewing and adjusting permissions, organizations can minimize the risk of security breaches and enhance overall data protection.
Regular reviews and audits complement the Principle of Least Privilege by providing a proactive mechanism for identifying anomalies and maintaining the dynamism required in user access management. Zoho Workplace’s comprehensive access logs and reporting tools empower administrators to conduct thorough audits, ensuring that user access aligns with organizational policies and security standards.
Furthermore, a secure digital workspace is not solely reliant on technological measures. The human element is equally critical. User training and awareness play a pivotal role in creating a security-conscious culture within the organization. Zoho Workplace facilitates this through training modules and security reminders, educating users on the significance of secure access practices, recognizing phishing attempts, and reporting suspicious activities.
The integration of advanced features like Single Sign-On (SSO), Multi-Factor Authentication (MFA), and Conditional Access Control elevates Zoho Workplace’s capability to fortify user access. SSO simplifies the user experience, MFA adds an extra layer of defense against unauthorized access attempts, and Conditional Access Control allows administrators to set access rules based on contextual factors, enhancing precision in access management.
As organizations navigate the ever-evolving landscape of digital threats, the secure user access control measures embedded in Zoho Workplace provide a comprehensive solution. By adopting these best practices, organizations not only safeguard their digital assets but also foster a secure and efficient work environment.
In essence, Zoho Workplace goes beyond being a mere collaboration platform; it stands as a partner in creating a secure digital ecosystem. Whether through the implementation of access controls based on the Principle of Least Privilege, regular reviews and audits, or user training initiatives, Zoho Workplace empowers organizations to navigate the nuanced challenges of user access security effectively.
In the dynamic world of digital workspaces, where the demand for collaboration meets the necessity for security, Zoho Workplace stands as a beacon, offering a versatile and secure environment where information flows freely but only to those with authorized access. As organizations strive to protect their data and maintain operational integrity, Zoho Workplace emerges not just as a tool but as a strategic ally in the pursuit of a secure and productive digital future.